 Collaboration diagram for ilLDAPRoleGroupMapping:
Collaboration diagram for ilLDAPRoleGroupMapping:Public Member Functions | |
| getInfoStrings ($a_obj_id, $a_check_type=false) | |
| Get info string for object If check info type is enabled this function will check if the info string is visible in the repository. | |
| assign ($a_role_id, $a_usr_id) | |
| This method is typically called from class RbacAdmin::assignUser() It checks if there is a role mapping and if the user has auth mode LDAP After these checks the user is assigned to the LDAP group. | |
| deleteRole ($a_role_id) | |
| Delete role. | |
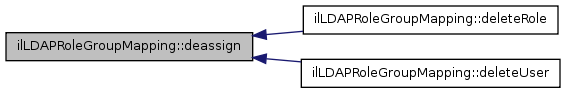
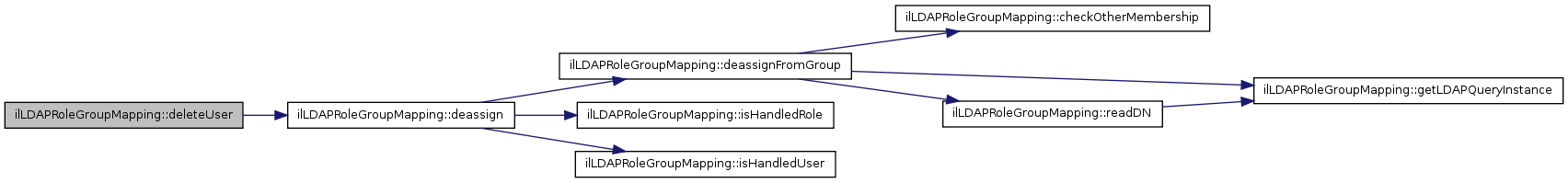
| deassign ($a_role_id, $a_usr_id) | |
| This method is typically called from class RbacAdmin::deassignUser() It checks if there is a role mapping and if the user has auth mode LDAP After these checks the user is deassigned from the LDAP group. | |
| deleteUser ($a_usr_id) | |
| Delete user => deassign from all ldap groups. | |
Static Public Member Functions | |
| static | _getInstance () |
| Get singleton instance of this class. | |
Private Member Functions | |
| __construct () | |
| Singleton contructor. | |
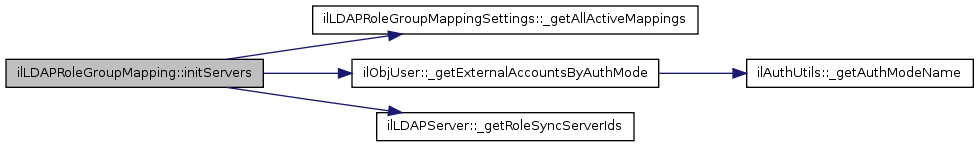
| initServers () | |
| Check if there is any active server with. | |
| isHandledRole ($a_role_id) | |
| Check if a role is handled or not. | |
| isHandledUser ($a_usr_id) | |
| Check if user is ldap user. | |
| assignToGroup ($a_role_id, $a_usr_id) | |
| Assign user to group. | |
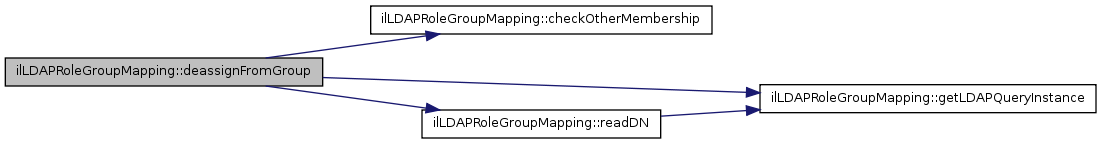
| deassignFromGroup ($a_role_id, $a_usr_id) | |
| Deassign user from group. | |
| isMember ($a_uid, $data) | |
| Check if user is member. | |
| checkOtherMembership ($a_usr_id, $a_role_id, $a_data) | |
| Check other membership. | |
| storeMembers ($a_mapping_id, $a_data) | |
| Store Members. | |
| readDN ($a_usr_id, $a_server_id) | |
| Read DN of user. | |
| getLDAPQueryInstance ($a_server_id, $a_url) | |
| Get LDAPQueryInstance. | |
Private Attributes | |
| $log = null | |
| $servers = null | |
| $mappings = array() | |
| $mapping_members = array() | |
| $query = array() | |
| $active_servers = false | |
Static Private Attributes | |
| static | $instance = null |
Detailed Description
- Version:
- $Id$
Definition at line 34 of file class.ilLDAPRoleGroupMapping.php.
Constructor & Destructor Documentation
| ilLDAPRoleGroupMapping::__construct | ( | ) | [private] |
Singleton contructor.
private
Definition at line 50 of file class.ilLDAPRoleGroupMapping.php.
References $ilLog, and initServers().
{
global $ilLog;
$this->log = $ilLog;
$this->initServers();
}
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
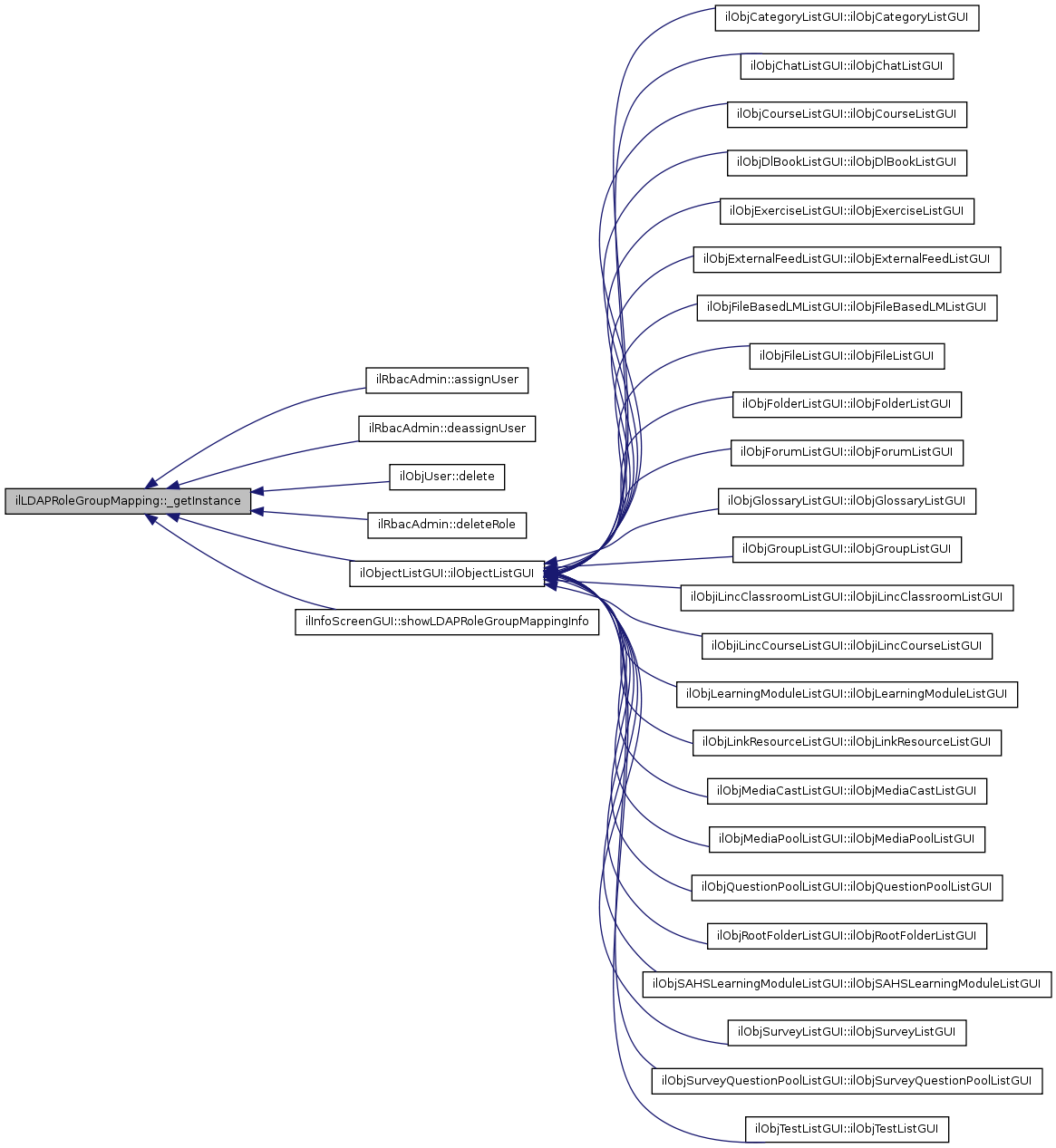
| static ilLDAPRoleGroupMapping::_getInstance | ( | ) | [static] |
Get singleton instance of this class.
public
Definition at line 64 of file class.ilLDAPRoleGroupMapping.php.
Referenced by ilRbacAdmin::assignUser(), ilRbacAdmin::deassignUser(), ilObjUser::delete(), ilRbacAdmin::deleteRole(), ilObjectListGUI::ilObjectListGUI(), and ilInfoScreenGUI::showLDAPRoleGroupMappingInfo().
{
if(is_object(self::$instance))
{
return self::$instance;
}
return self::$instance = new ilLDAPRoleGroupMapping();
}
 Here is the caller graph for this function:
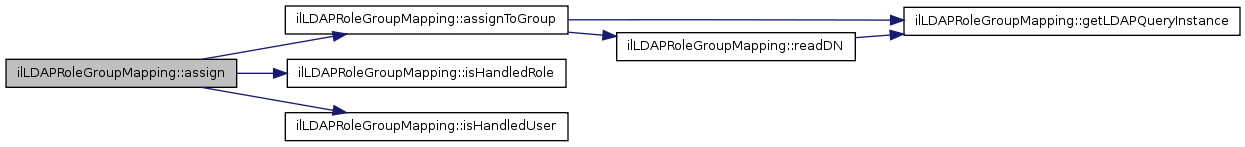
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::assign | ( | $ | a_role_id, | |
| $ | a_usr_id | |||
| ) |
This method is typically called from class RbacAdmin::assignUser() It checks if there is a role mapping and if the user has auth mode LDAP After these checks the user is assigned to the LDAP group.
public
- Parameters:
-
Definition at line 116 of file class.ilLDAPRoleGroupMapping.php.
References assignToGroup(), isHandledRole(), and isHandledUser().
{
// return if there nothing to do
if(!$this->active_servers)
{
return false;
}
if(!$this->isHandledRole($a_role_id))
{
return false;
}
if(!$this->isHandledUser($a_usr_id))
{
$this->log->write('LDAP assign: User ID: '.$a_usr_id.' has no LDAP account');
return false;
}
$this->log->write('LDAP assign: User ID: '.$a_usr_id.' Role Id: '.$a_role_id);
$this->assignToGroup($a_role_id,$a_usr_id);
return true;
}
 Here is the call graph for this function:
Here is the call graph for this function:| ilLDAPRoleGroupMapping::assignToGroup | ( | $ | a_role_id, | |
| $ | a_usr_id | |||
| ) | [private] |
Assign user to group.
private
- Parameters:
-
int role_id int user_id
Definition at line 295 of file class.ilLDAPRoleGroupMapping.php.
References $data, getLDAPQueryInstance(), and readDN().
Referenced by assign().
{
foreach($this->mappings[$a_role_id] as $data)
{
try
{
if($data['isdn'])
{
$external_account = $this->readDN($a_usr_id,$data['server_id']);
}
else
{
$external_account = $this->users[$a_usr_id];
}
// Forcing modAdd since Active directory is too slow and i cannot check if a user is member or not.
#if($this->isMember($external_account,$data))
#{
# $this->log->write("LDAP assign: User already assigned to group '".$data['dn']."'");
#}
#else
{
// Add user
$query_obj = $this->getLDAPQueryInstance($data['server_id'],$data['url']);
$query_obj->modAdd($data['dn'],array($data['member'] => $external_account));
$this->log->write('LDAP assign: Assigned '.$external_account.' to group '.$data['dn']);
}
}
catch(ilLDAPQueryException $exc)
{
$this->log->write($exc->getMessage());
// try next mapping
continue;
}
}
}
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::checkOtherMembership | ( | $ | a_usr_id, | |
| $ | a_role_id, | |||
| $ | a_data | |||
| ) | [private] |
Check other membership.
private
- Returns:
- string role name
Definition at line 440 of file class.ilLDAPRoleGroupMapping.php.
References $data.
Referenced by deassignFromGroup().
{
global $rbacreview,$ilObjDataCache;
foreach($this->mappings as $role_id => $tmp_data)
{
foreach($tmp_data as $data)
{
if($role_id == $a_role_id)
{
continue;
}
if($data['server_id'] != $a_data['server_id'])
{
continue;
}
if($data['dn'] != $a_data['dn'])
{
continue;
}
if($rbacreview->isAssigned($a_usr_id,$role_id))
{
return $ilObjDataCache->lookupTitle($role_id);
}
}
}
return false;
}
 Here is the caller graph for this function:
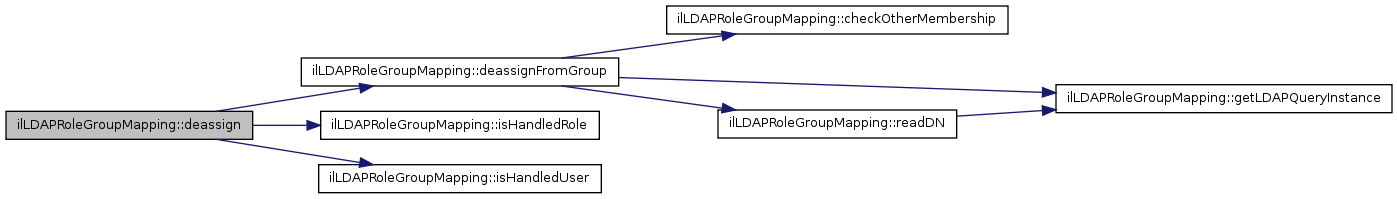
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::deassign | ( | $ | a_role_id, | |
| $ | a_usr_id | |||
| ) |
This method is typically called from class RbacAdmin::deassignUser() It checks if there is a role mapping and if the user has auth mode LDAP After these checks the user is deassigned from the LDAP group.
public
- Parameters:
-
Definition at line 180 of file class.ilLDAPRoleGroupMapping.php.
References deassignFromGroup(), isHandledRole(), and isHandledUser().
Referenced by deleteRole(), and deleteUser().
{
// return if there notzing to do
if(!$this->active_servers)
{
return false;
}
if(!$this->isHandledRole($a_role_id))
{
return false;
}
if(!$this->isHandledUser($a_usr_id))
{
return false;
}
$this->log->write('LDAP deassign: User ID: '.$a_usr_id.' Role Id: '.$a_role_id);
$this->deassignFromGroup($a_role_id,$a_usr_id);
return true;
}
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::deassignFromGroup | ( | $ | a_role_id, | |
| $ | a_usr_id | |||
| ) | [private] |
Deassign user from group.
private
- Parameters:
-
int role_id int user_id
Definition at line 340 of file class.ilLDAPRoleGroupMapping.php.
References $data, checkOtherMembership(), getLDAPQueryInstance(), and readDN().
Referenced by deassign().
{
foreach($this->mappings[$a_role_id] as $data)
{
try
{
if($data['isdn'])
{
$external_account = $this->readDN($a_usr_id,$data['server_id']);
}
else
{
$external_account = $this->users[$a_usr_id];
}
// Check for other role membership
if($role_id = $this->checkOtherMembership($a_usr_id,$a_role_id,$data))
{
$this->log->write('LDAP deassign: User is still assigned to role "'.$role_id.'".');
continue;
}
/*
if(!$this->isMember($external_account,$data))
{
$this->log->write("LDAP deassign: User not assigned to group '".$data['dn']."'");
continue;
}
*/
// Deassign user
$query_obj = $this->getLDAPQueryInstance($data['server_id'],$data['url']);
$query_obj->modDelete($data['dn'],array($data['member'] => $external_account));
$this->log->write('LDAP deassign: Deassigned '.$external_account.' from group '.$data['dn']);
// Delete from cache
if(is_array($this->mapping_members[$data['mapping_id']]))
{
$key = array_search($external_account,$this->mapping_members[$data['mapping_id']]);
if($key or $key === 0)
{
unset($this->mapping_members[$data['mapping_id']]);
}
}
}
catch(ilLDAPQueryException $exc)
{
$this->log->write($exc->getMessage());
// try next mapping
continue;
}
}
}
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::deleteRole | ( | $ | a_role_id | ) |
Delete role.
This function triggered from ilRbacAdmin::deleteRole It deassigns all user from the mapped ldap group.
public
- Parameters:
-
int role id
Definition at line 148 of file class.ilLDAPRoleGroupMapping.php.
References deassign(), and isHandledRole().
{
global $rbacreview;
// return if there nothing to do
if(!$this->active_servers)
{
return false;
}
if(!$this->isHandledRole($a_role_id))
{
return false;
}
foreach($rbacreview->assignedUsers($a_role_id) as $usr_id)
{
$this->deassign($a_role_id,$usr_id);
}
return true;
}
 Here is the call graph for this function:
Here is the call graph for this function:| ilLDAPRoleGroupMapping::deleteUser | ( | $ | a_usr_id | ) |
Delete user => deassign from all ldap groups.
public
- Parameters:
-
int user id
Definition at line 207 of file class.ilLDAPRoleGroupMapping.php.
References $data, and deassign().
{
foreach($this->mappings as $role_id => $data)
{
$this->deassign($role_id,$a_usr_id);
}
return true;
}
 Here is the call graph for this function:
Here is the call graph for this function:| ilLDAPRoleGroupMapping::getInfoStrings | ( | $ | a_obj_id, | |
| $ | a_check_type = false | |||
| ) |
Get info string for object If check info type is enabled this function will check if the info string is visible in the repository.
public
- Parameters:
-
int object id bool check info type
Definition at line 82 of file class.ilLDAPRoleGroupMapping.php.
{
if(!$this->active_servers)
{
return false;
}
if($a_check_type)
{
if(isset($this->mapping_info_strict[$a_obj_id]) and is_array($this->mapping_info_strict[$a_obj_id]))
{
return $this->mapping_info_strict[$a_obj_id];
}
}
else
{
if(isset($this->mapping_info[$a_obj_id]) and is_array($this->mapping_info[$a_obj_id]))
{
return $this->mapping_info[$a_obj_id];
}
}
return false;
}
| ilLDAPRoleGroupMapping::getLDAPQueryInstance | ( | $ | a_server_id, | |
| $ | a_url | |||
| ) | [private] |
Get LDAPQueryInstance.
private
- Parameters:
-
@throws ilLDAPQueryException
Definition at line 561 of file class.ilLDAPRoleGroupMapping.php.
Referenced by assignToGroup(), deassignFromGroup(), isMember(), and readDN().
{
include_once 'Services/LDAP/classes/class.ilLDAPQuery.php';
if(array_key_exists($a_server_id,$this->query) and
array_key_exists($a_url,$this->query[$a_server_id]) and
is_object($this->query[$a_server_id][$a_url]))
{
return $this->query[$a_server_id][$a_url];
}
try
{
$tmp_query = new ilLDAPQuery($this->servers[$a_server_id],$a_url);
$tmp_query->bind(IL_LDAP_BIND_ADMIN);
}
catch(ilLDAPQueryException $exc)
{
throw $exc;
}
return $this->query[$a_server_id][$a_url] = $tmp_query;
}
 Here is the caller graph for this function:
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::initServers | ( | ) | [private] |
Check if there is any active server with.
private
- Parameters:
-
Definition at line 224 of file class.ilLDAPRoleGroupMapping.php.
References $data, ilLDAPRoleGroupMappingSettings::_getAllActiveMappings(), ilObjUser::_getExternalAccountsByAuthMode(), ilLDAPServer::_getRoleSyncServerIds(), and ilLDAPRoleGroupMappingSettings::MAPPING_INFO_ALL.
Referenced by __construct().
{
$server_ids = ilLDAPServer::_getRoleSyncServerIds();
if(!count($server_ids))
{
return false;
}
// Init servers
include_once('Services/LDAP/classes/class.ilLDAPRoleGroupMappingSettings.php');
$this->active_servers = true;
$this->mappings = array();
foreach($server_ids as $server_id)
{
$this->servers[$server_id] = new ilLDAPServer($server_id);
$this->mappings = ilLDAPRoleGroupMappingSettings::_getAllActiveMappings();
}
$this->mapping_info = array();
$this->mapping_info_strict = array();
foreach($this->mappings as $mapping)
{
foreach($mapping as $key => $data)
{
if(strlen($data['info']) and $data['object_id'])
{
$this->mapping_info[$data['object_id']][] = $data['info'];
}
if(strlen($data['info']) && ($data['info_type'] == ilLDAPRoleGroupMappingSettings::MAPPING_INFO_ALL))
{
$this->mapping_info_strict[$data['object_id']][] = $data['info'];
}
}
}
$this->users = ilObjUser::_getExternalAccountsByAuthMode('ldap',true);
return true;
}
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::isHandledRole | ( | $ | a_role_id | ) | [private] |
Check if a role is handled or not.
private
- Parameters:
-
int role_id
- Returns:
- int server id or 0 if mapping exists
Definition at line 272 of file class.ilLDAPRoleGroupMapping.php.
Referenced by assign(), deassign(), and deleteRole().
{
return array_key_exists($a_role_id,$this->mappings);
}
 Here is the caller graph for this function:
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::isHandledUser | ( | $ | a_usr_id | ) | [private] |
Check if user is ldap user.
private
Definition at line 282 of file class.ilLDAPRoleGroupMapping.php.
Referenced by assign(), and deassign().
{
return array_key_exists($a_usr_id,$this->users);
}
 Here is the caller graph for this function:
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::isMember | ( | $ | a_uid, | |
| $ | data | |||
| ) | [private] |
Check if user is member.
private
- Exceptions:
-
ilLDAPQueryException
Definition at line 399 of file class.ilLDAPRoleGroupMapping.php.
References $data, $res, $server, getLDAPQueryInstance(), and storeMembers().
{
if(!isset($this->mapping_members["$data[mapping_id]"]))
{
// Read members
try
{
$server = $this->servers["$data[server_id]"];
$query_obj = $this->getLDAPQueryInstance($data['server_id'],$server->getUrl());
// query for members
$res = $query_obj->query($data['dn'],
'(objectClass=*)',
IL_LDAP_SCOPE_BASE,
array($data['member']));
$this->storeMembers($data['mapping_id'],$res->get());
unset($res);
}
catch(ilLDAPQueryException $exc)
{
throw $exc;
}
}
#var_dump("<pre>",$a_uid,$this->mapping_members,"</pre>");
// Now check for membership in stored result
if(in_array($a_uid,$this->mapping_members["$data[mapping_id]"]))
{
return true;
}
return false;
}
 Here is the call graph for this function:
Here is the call graph for this function:| ilLDAPRoleGroupMapping::readDN | ( | $ | a_usr_id, | |
| $ | a_server_id | |||
| ) | [private] |
Read DN of user.
private
- Parameters:
-
int user id int server id
- Exceptions:
-
ilLDAPQueryException
Definition at line 507 of file class.ilLDAPRoleGroupMapping.php.
References $data, $res, $server, and getLDAPQueryInstance().
Referenced by assignToGroup(), and deassignFromGroup().
{
if(isset($this->user_dns[$a_usr_id]))
{
return $this->user_dns[$a_usr_id];
}
$external_account = $this->users[$a_usr_id];
try
{
$server = $this->servers[$a_server_id];
$query_obj = $this->getLDAPQueryInstance($a_server_id,$server->getUrl());
if($search_base = $server->getSearchBase())
{
$search_base .= ',';
}
$search_base .= $server->getBaseDN();
$filter = sprintf('(&(%s=%s)%s)',
$server->getUserAttribute(),
$external_account,
$server->getFilter());
$res = $query_obj->query($search_base,$filter,$server->getUserScope(),array('dn'));
if(!$res->numRows())
{
include_once('Services/LDAP/classes/class.ilLDAPQueryException.php');
throw new ilLDAPQueryException(__METHOD__.' cannot find dn for user '.$external_account);
}
if($res->numRows() > 1)
{
include_once('Services/LDAP/classes/class.ilLDAPQueryException.php');
throw new ilLDAPQueryException(__METHOD__.' found multiple distinguished name for: '.$external_account);
}
$data = $res->get();
return $this->user_dns[$a_usr_id] = $data['dn'];
}
catch(ilLDAPQueryException $exc)
{
throw $exc;
}
}
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:| ilLDAPRoleGroupMapping::storeMembers | ( | $ | a_mapping_id, | |
| $ | a_data | |||
| ) | [private] |
Store Members.
private
Definition at line 476 of file class.ilLDAPRoleGroupMapping.php.
Referenced by isMember().
{
$this->mapping_members[$a_mapping_id] = array();
foreach($a_data as $field => $value)
{
if(strtolower($field) == 'dn')
{
continue;
}
if(!is_array($value))
{
$this->mapping_members[$a_mapping_id][] = $value;
continue;
}
foreach($value as $external_account)
{
$this->mapping_members[$a_mapping_id][] = $external_account;
}
}
return true;
}
 Here is the caller graph for this function:
Here is the caller graph for this function:Field Documentation
ilLDAPRoleGroupMapping::$active_servers = false [private] |
Definition at line 42 of file class.ilLDAPRoleGroupMapping.php.
ilLDAPRoleGroupMapping::$instance = null [static, private] |
Definition at line 37 of file class.ilLDAPRoleGroupMapping.php.
ilLDAPRoleGroupMapping::$log = null [private] |
Definition at line 36 of file class.ilLDAPRoleGroupMapping.php.
ilLDAPRoleGroupMapping::$mapping_members = array() [private] |
Definition at line 40 of file class.ilLDAPRoleGroupMapping.php.
ilLDAPRoleGroupMapping::$mappings = array() [private] |
Definition at line 39 of file class.ilLDAPRoleGroupMapping.php.
ilLDAPRoleGroupMapping::$query = array() [private] |
Definition at line 41 of file class.ilLDAPRoleGroupMapping.php.
ilLDAPRoleGroupMapping::$servers = null [private] |
Definition at line 38 of file class.ilLDAPRoleGroupMapping.php.
The documentation for this class was generated from the following file:
- Services/LDAP/classes/class.ilLDAPRoleGroupMapping.php




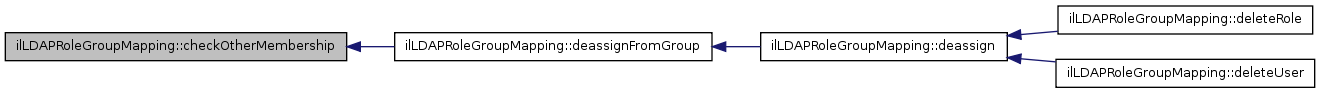







 1.7.1
1.7.1