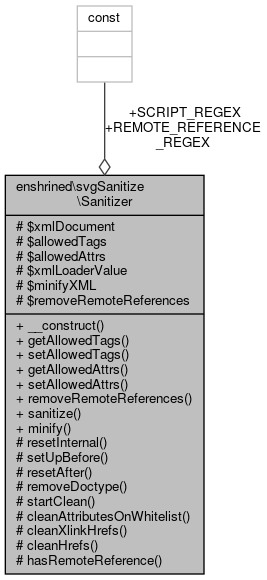
Collaboration diagram for enshrined\svgSanitize\Sanitizer:
Collaboration diagram for enshrined\svgSanitize\Sanitizer:Public Member Functions | |
| __construct () | |
| getAllowedTags () | |
| Get the array of allowed tags. More... | |
| setAllowedTags (TagInterface $allowedTags) | |
| Set custom allowed tags. More... | |
| getAllowedAttrs () | |
| Get the array of allowed attributes. More... | |
| setAllowedAttrs (AttributeInterface $allowedAttrs) | |
| Set custom allowed attributes. More... | |
| removeRemoteReferences ($removeRemoteRefs=false) | |
| Should we remove references to remote files? More... | |
| sanitize ($dirty) | |
| Sanitize the passed string. More... | |
| minify ($shouldMinify=false) | |
| Should we minify the output? More... | |
Data Fields | |
| const | SCRIPT_REGEX = '/(?:\w+script|data):/xi' |
| Regex to catch script and data values in attributes. More... | |
| const | REMOTE_REFERENCE_REGEX = '/url\(([\'"]?(?:http|https):)[\'"]?([^\'"\)]*)[\'"]?\)/xi' |
| Regex to test for remote URLs in linked assets. More... | |
Protected Member Functions | |
| resetInternal () | |
| Set up the DOMDocument. More... | |
| setUpBefore () | |
| Set up libXML before we start. More... | |
| resetAfter () | |
| Reset the class after use. More... | |
| removeDoctype () | |
| Remove the XML Doctype It may be caught later on output but that seems to be buggy, so we need to make sure it's gone. More... | |
| startClean (\DOMNodeList $elements) | |
| Start the cleaning with tags, then we move onto attributes and hrefs later. More... | |
| cleanAttributesOnWhitelist (\DOMElement $element) | |
| Only allow attributes that are on the whitelist. More... | |
| cleanXlinkHrefs (\DOMElement &$element) | |
| Clean the xlink:hrefs of script and data embeds. More... | |
| cleanHrefs (\DOMElement &$element) | |
| Clean the hrefs of script and data embeds. More... | |
| hasRemoteReference ($value) | |
| Does this attribute value have a remote reference? More... | |
Protected Attributes | |
| $xmlDocument | |
| $allowedTags | |
| $allowedAttrs | |
| $xmlLoaderValue | |
| $minifyXML = false | |
| $removeRemoteReferences = false | |
Detailed Description
Definition at line 18 of file Sanitizer.php.
Constructor & Destructor Documentation
◆ __construct()
| enshrined\svgSanitize\Sanitizer::__construct | ( | ) |
Definition at line 64 of file Sanitizer.php.
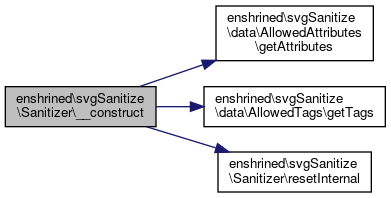
References enshrined\svgSanitize\data\AllowedAttributes\getAttributes(), enshrined\svgSanitize\data\AllowedTags\getTags(), and enshrined\svgSanitize\Sanitizer\resetInternal().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ cleanAttributesOnWhitelist()
|
protected |
Only allow attributes that are on the whitelist.
- Parameters
-
\DOMElement $element
Definition at line 256 of file Sanitizer.php.
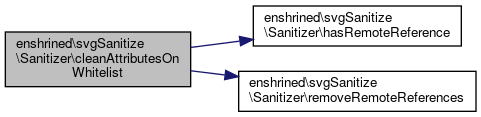
References $x, and enshrined\svgSanitize\Sanitizer\removeRemoteReferences().
Referenced by enshrined\svgSanitize\Sanitizer\startClean().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ cleanHrefs()
|
protected |
Clean the hrefs of script and data embeds.
- Parameters
-
\DOMElement $element
Definition at line 295 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\startClean().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ cleanXlinkHrefs()
|
protected |
Clean the xlink:hrefs of script and data embeds.
- Parameters
-
\DOMElement $element
Definition at line 282 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\startClean().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getAllowedAttrs()
| enshrined\svgSanitize\Sanitizer::getAllowedAttrs | ( | ) |
Get the array of allowed attributes.
- Returns
- array
Definition at line 114 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\$allowedAttrs.
◆ getAllowedTags()
| enshrined\svgSanitize\Sanitizer::getAllowedTags | ( | ) |
Get the array of allowed tags.
- Returns
- array
Definition at line 94 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\$allowedTags.
◆ hasRemoteReference()
|
protected |
Does this attribute value have a remote reference?
- Parameters
-
$value
- Returns
- bool
Definition at line 309 of file Sanitizer.php.
◆ minify()
| enshrined\svgSanitize\Sanitizer::minify | ( | $shouldMinify = false | ) |
Should we minify the output?
- Parameters
-
bool $shouldMinify
Definition at line 323 of file Sanitizer.php.
◆ removeDoctype()
|
protected |
Remove the XML Doctype It may be caught later on output but that seems to be buggy, so we need to make sure it's gone.
Definition at line 215 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ removeRemoteReferences()
| enshrined\svgSanitize\Sanitizer::removeRemoteReferences | ( | $removeRemoteRefs = false | ) |
Should we remove references to remote files?
- Parameters
-
bool $removeRemoteRefs
Definition at line 134 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\removeRemoteReferences().
Referenced by enshrined\svgSanitize\Sanitizer\cleanAttributesOnWhitelist(), and enshrined\svgSanitize\Sanitizer\removeRemoteReferences().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ resetAfter()
|
protected |
Reset the class after use.
Definition at line 202 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\resetInternal().
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ resetInternal()
|
protected |
Set up the DOMDocument.
Definition at line 76 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\__construct(), and enshrined\svgSanitize\Sanitizer\resetAfter().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ sanitize()
| enshrined\svgSanitize\Sanitizer::sanitize | ( | $dirty | ) |
Sanitize the passed string.
- Parameters
-
string $dirty
- Returns
- string
Definition at line 145 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\removeDoctype(), enshrined\svgSanitize\Sanitizer\resetAfter(), enshrined\svgSanitize\Sanitizer\setUpBefore(), and enshrined\svgSanitize\Sanitizer\startClean().
 Here is the call graph for this function:
Here is the call graph for this function:◆ setAllowedAttrs()
| enshrined\svgSanitize\Sanitizer::setAllowedAttrs | ( | AttributeInterface | $allowedAttrs | ) |
Set custom allowed attributes.
- Parameters
-
AttributeInterface $allowedAttrs
Definition at line 124 of file Sanitizer.php.
◆ setAllowedTags()
| enshrined\svgSanitize\Sanitizer::setAllowedTags | ( | TagInterface | $allowedTags | ) |
Set custom allowed tags.
- Parameters
-
TagInterface $allowedTags
Definition at line 104 of file Sanitizer.php.
◆ setUpBefore()
|
protected |
Set up libXML before we start.
Definition at line 190 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ startClean()
|
protected |
Start the cleaning with tags, then we move onto attributes and hrefs later.
- Parameters
-
\DOMNodeList $elements
Definition at line 229 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\cleanAttributesOnWhitelist(), enshrined\svgSanitize\Sanitizer\cleanHrefs(), and enshrined\svgSanitize\Sanitizer\cleanXlinkHrefs().
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:Field Documentation
◆ $allowedAttrs
|
protected |
Definition at line 44 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\getAllowedAttrs().
◆ $allowedTags
|
protected |
Definition at line 39 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\getAllowedTags().
◆ $minifyXML
|
protected |
Definition at line 54 of file Sanitizer.php.
◆ $removeRemoteReferences
|
protected |
Definition at line 59 of file Sanitizer.php.
◆ $xmlDocument
|
protected |
Definition at line 34 of file Sanitizer.php.
◆ $xmlLoaderValue
|
protected |
Definition at line 49 of file Sanitizer.php.
◆ REMOTE_REFERENCE_REGEX
| const enshrined\svgSanitize\Sanitizer::REMOTE_REFERENCE_REGEX = '/url\(([\'"]?(?:http|https):)[\'"]?([^\'"\)]*)[\'"]?\)/xi' |
Regex to test for remote URLs in linked assets.
Definition at line 29 of file Sanitizer.php.
◆ SCRIPT_REGEX
| const enshrined\svgSanitize\Sanitizer::SCRIPT_REGEX = '/(?:\w+script|data):/xi' |
Regex to catch script and data values in attributes.
Definition at line 24 of file Sanitizer.php.
The documentation for this class was generated from the following file:
- Services/MediaObjects/lib/svg-sanitizer-master/src/Sanitizer.php