Collaboration diagram for ilLDAPRoleGroupMapping:
Collaboration diagram for ilLDAPRoleGroupMapping:Public Member Functions | |
| getInfoStrings ($a_obj_id, $a_check_type=false) | |
| Get info string for object If check info type is enabled this function will check if the info string is visible in the repository. More... | |
| assign ($a_role_id, $a_usr_id) | |
| This method is typically called from class RbacAdmin::assignUser() It checks if there is a role mapping and if the user has auth mode LDAP After these checks the user is assigned to the LDAP group. More... | |
| deleteRole ($a_role_id) | |
| Delete role. More... | |
| deassign ($a_role_id, $a_usr_id) | |
| This method is typically called from class RbacAdmin::deassignUser() It checks if there is a role mapping and if the user has auth mode LDAP After these checks the user is deassigned from the LDAP group. More... | |
| deleteUser ($a_usr_id) | |
| Delete user => deassign from all ldap groups. More... | |
Static Public Member Functions | |
| static | _getInstance () |
| Get singleton instance of this class. More... | |
Private Member Functions | |
| __construct () | |
| Singleton contructor. More... | |
| initServers () | |
| Check if there is any active server with. More... | |
| isHandledRole ($a_role_id) | |
| Check if a role is handled or not. More... | |
| isHandledUser ($a_usr_id) | |
| Check if user is ldap user. More... | |
| assignToGroup ($a_role_id, $a_usr_id) | |
| Assign user to group. More... | |
| deassignFromGroup ($a_role_id, $a_usr_id) | |
| Deassign user from group. More... | |
| isMember ($a_uid, $data) | |
| Check if user is member. More... | |
| checkOtherMembership ($a_usr_id, $a_role_id, $a_data) | |
| Check other membership. More... | |
| storeMembers ($a_mapping_id, $a_data) | |
| Store Members. More... | |
| readDN ($a_usr_id, $a_server_id) | |
| Read DN of user. More... | |
| getLDAPQueryInstance ($a_server_id, $a_url) | |
| Get LDAPQueryInstance. More... | |
Private Attributes | |
| $log = null | |
| $servers = null | |
| $mappings = array() | |
| $mapping_members = array() | |
| $query = array() | |
| $active_servers = false | |
Static Private Attributes | |
| static | $instance = null |
Detailed Description
- Version
- $Id$
Definition at line 34 of file class.ilLDAPRoleGroupMapping.php.
Constructor & Destructor Documentation
◆ __construct()
|
private |
Singleton contructor.
@access private
Definition at line 50 of file class.ilLDAPRoleGroupMapping.php.
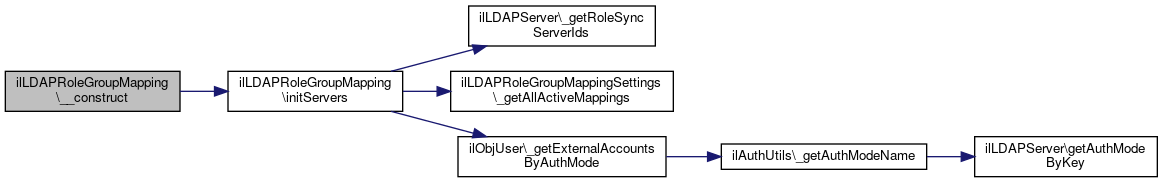
References $ilLog, and initServers().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ _getInstance()
|
static |
Get singleton instance of this class.
@access public
Definition at line 64 of file class.ilLDAPRoleGroupMapping.php.
References $instance.
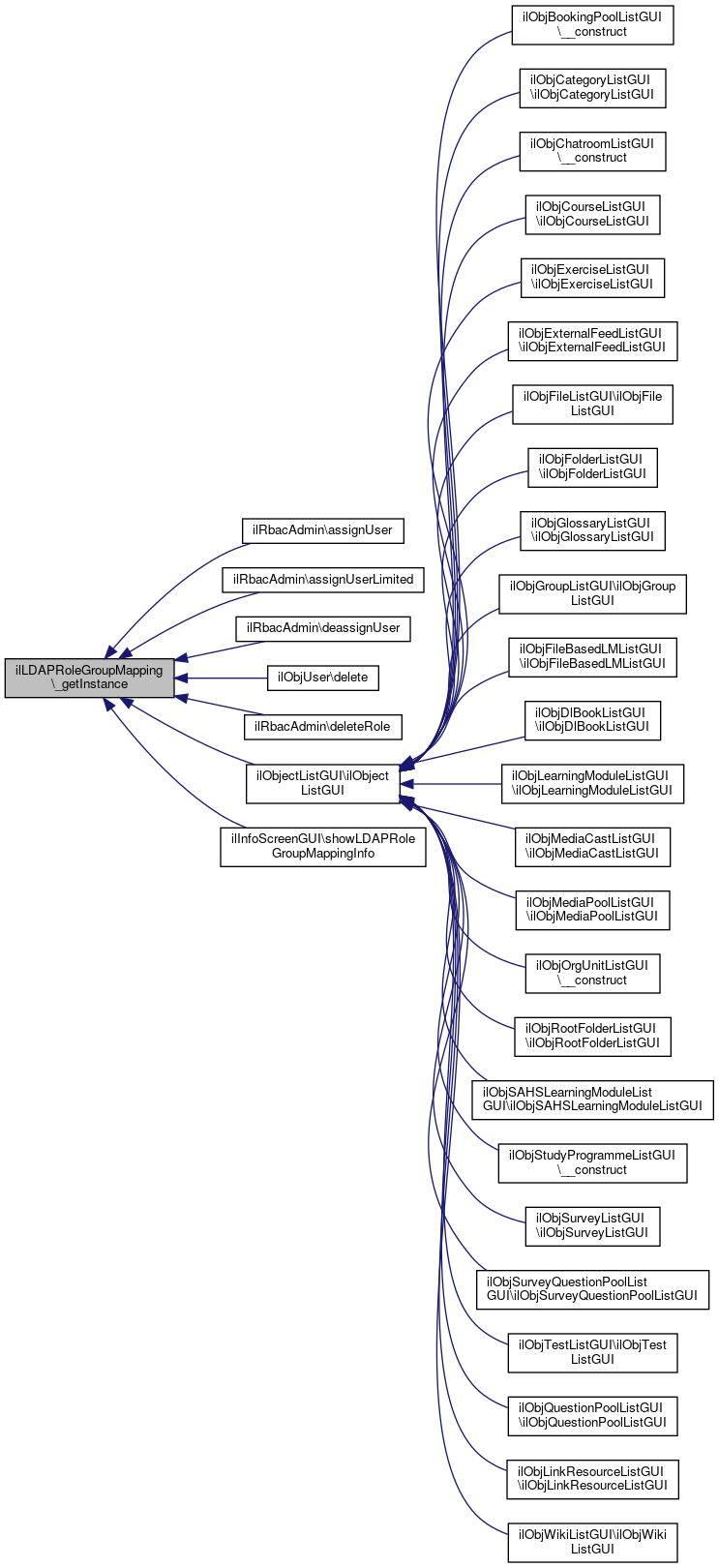
Referenced by ilRbacAdmin\assignUser(), ilRbacAdmin\assignUserLimited(), ilRbacAdmin\deassignUser(), ilObjUser\delete(), ilRbacAdmin\deleteRole(), ilObjectListGUI\ilObjectListGUI(), and ilInfoScreenGUI\showLDAPRoleGroupMappingInfo().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ assign()
| ilLDAPRoleGroupMapping::assign | ( | $a_role_id, | |
| $a_usr_id | |||
| ) |
This method is typically called from class RbacAdmin::assignUser() It checks if there is a role mapping and if the user has auth mode LDAP After these checks the user is assigned to the LDAP group.
@access public
- Parameters
-
Definition at line 116 of file class.ilLDAPRoleGroupMapping.php.
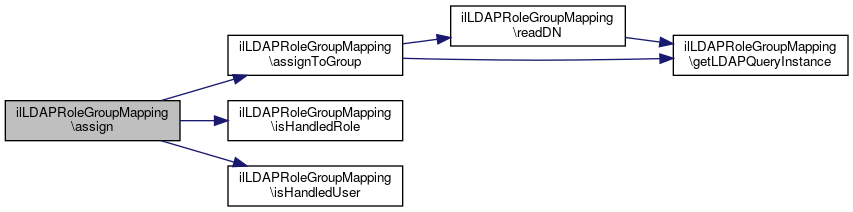
References assignToGroup(), isHandledRole(), and isHandledUser().
 Here is the call graph for this function:
Here is the call graph for this function:◆ assignToGroup()
|
private |
Assign user to group.
@access private
- Parameters
-
int role_id int user_id
Definition at line 295 of file class.ilLDAPRoleGroupMapping.php.
References $data, getLDAPQueryInstance(), and readDN().
Referenced by assign().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ checkOtherMembership()
|
private |
Check other membership.
@access private
- Returns
- string role name
Definition at line 440 of file class.ilLDAPRoleGroupMapping.php.
References $data.
Referenced by deassignFromGroup().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ deassign()
| ilLDAPRoleGroupMapping::deassign | ( | $a_role_id, | |
| $a_usr_id | |||
| ) |
This method is typically called from class RbacAdmin::deassignUser() It checks if there is a role mapping and if the user has auth mode LDAP After these checks the user is deassigned from the LDAP group.
@access public
- Parameters
-
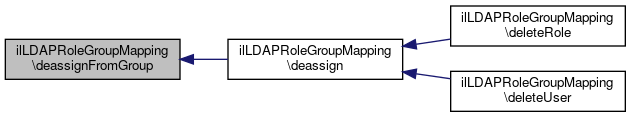
Definition at line 180 of file class.ilLDAPRoleGroupMapping.php.
References deassignFromGroup(), isHandledRole(), and isHandledUser().
Referenced by deleteRole(), and deleteUser().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ deassignFromGroup()
|
private |
Deassign user from group.
@access private
- Parameters
-
int role_id int user_id
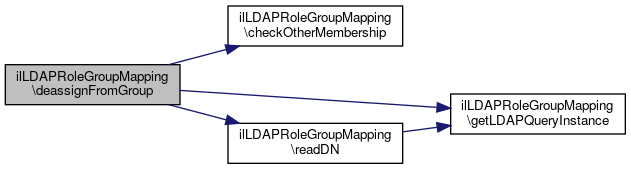
Definition at line 340 of file class.ilLDAPRoleGroupMapping.php.
References $data, checkOtherMembership(), getLDAPQueryInstance(), and readDN().
Referenced by deassign().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ deleteRole()
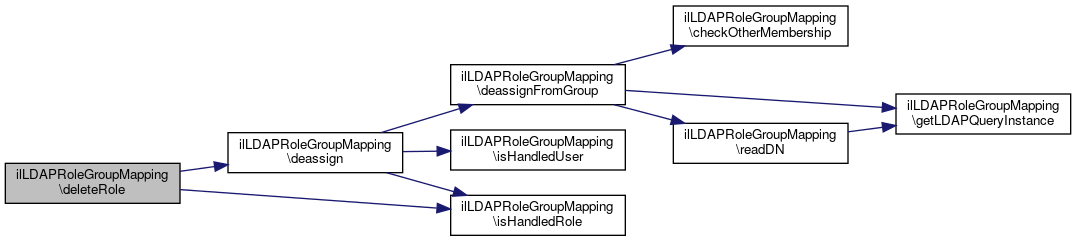
| ilLDAPRoleGroupMapping::deleteRole | ( | $a_role_id | ) |
Delete role.
This function triggered from ilRbacAdmin::deleteRole It deassigns all user from the mapped ldap group.
@access public
- Parameters
-
int role id
Definition at line 148 of file class.ilLDAPRoleGroupMapping.php.
References deassign(), and isHandledRole().
 Here is the call graph for this function:
Here is the call graph for this function:◆ deleteUser()
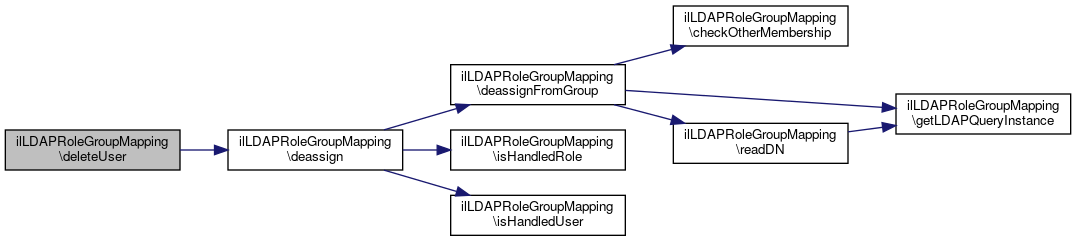
| ilLDAPRoleGroupMapping::deleteUser | ( | $a_usr_id | ) |
Delete user => deassign from all ldap groups.
@access public
- Parameters
-
int user id
Definition at line 207 of file class.ilLDAPRoleGroupMapping.php.
References $data, and deassign().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getInfoStrings()
| ilLDAPRoleGroupMapping::getInfoStrings | ( | $a_obj_id, | |
$a_check_type = false |
|||
| ) |
Get info string for object If check info type is enabled this function will check if the info string is visible in the repository.
@access public
- Parameters
-
int object id bool check info type
Definition at line 82 of file class.ilLDAPRoleGroupMapping.php.
◆ getLDAPQueryInstance()
|
private |
Get LDAPQueryInstance.
@access private
- Parameters
-
throws ilLDAPQueryException
Definition at line 571 of file class.ilLDAPRoleGroupMapping.php.
References IL_LDAP_BIND_ADMIN.
Referenced by assignToGroup(), deassignFromGroup(), isMember(), and readDN().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ initServers()
|
private |
Check if there is any active server with.
@access private
- Parameters
-
Definition at line 224 of file class.ilLDAPRoleGroupMapping.php.
References $data, ilLDAPRoleGroupMappingSettings\_getAllActiveMappings(), ilObjUser\_getExternalAccountsByAuthMode(), ilLDAPServer\_getRoleSyncServerIds(), and ilLDAPRoleGroupMappingSettings\MAPPING_INFO_ALL.
Referenced by __construct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ isHandledRole()
|
private |
Check if a role is handled or not.
@access private
- Parameters
-
int role_id
- Returns
- int server id or 0 if mapping exists
Definition at line 272 of file class.ilLDAPRoleGroupMapping.php.
Referenced by assign(), deassign(), and deleteRole().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ isHandledUser()
|
private |
Check if user is ldap user.
@access private
Definition at line 282 of file class.ilLDAPRoleGroupMapping.php.
Referenced by assign(), and deassign().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ isMember()
|
private |
Check if user is member.
@access private
- Exceptions
-
ilLDAPQueryException
Definition at line 399 of file class.ilLDAPRoleGroupMapping.php.
References $data, $res, $server, getLDAPQueryInstance(), IL_LDAP_SCOPE_BASE, and storeMembers().
 Here is the call graph for this function:
Here is the call graph for this function:◆ readDN()
|
private |
Read DN of user.
@access private
- Parameters
-
int user id int server id
- Exceptions
-
ilLDAPQueryException
Definition at line 507 of file class.ilLDAPRoleGroupMapping.php.
References $data, $res, $server, and getLDAPQueryInstance().
Referenced by assignToGroup(), and deassignFromGroup().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ storeMembers()
|
private |
Store Members.
@access private
Definition at line 476 of file class.ilLDAPRoleGroupMapping.php.
Referenced by isMember().
 Here is the caller graph for this function:
Here is the caller graph for this function:Field Documentation
◆ $active_servers
|
private |
Definition at line 42 of file class.ilLDAPRoleGroupMapping.php.
◆ $instance
|
staticprivate |
Definition at line 37 of file class.ilLDAPRoleGroupMapping.php.
Referenced by _getInstance().
◆ $log
|
private |
Definition at line 36 of file class.ilLDAPRoleGroupMapping.php.
◆ $mapping_members
|
private |
Definition at line 40 of file class.ilLDAPRoleGroupMapping.php.
◆ $mappings
|
private |
Definition at line 39 of file class.ilLDAPRoleGroupMapping.php.
◆ $query
|
private |
Definition at line 41 of file class.ilLDAPRoleGroupMapping.php.
◆ $servers
|
private |
Definition at line 38 of file class.ilLDAPRoleGroupMapping.php.
The documentation for this class was generated from the following file:
- Services/LDAP/classes/class.ilLDAPRoleGroupMapping.php