Collaboration diagram for Sanitizer:
Collaboration diagram for Sanitizer:Static Public Member Functions | |
| static | removeHTMLtags ($text, $processCallback=null, $args=array()) |
| Cleans up HTML, removes dangerous tags and attributes, and removes HTML comments. More... | |
| static | removeHTMLcomments ($text) |
| Remove '', and everything between. More... | |
| static | validateTagAttributes ($attribs, $element) |
| Take an array of attribute names and values and normalize or discard illegal values for the given element type. More... | |
| static | checkCss ($value) |
| Pick apart some CSS and check it for forbidden or unsafe structures. More... | |
| static | fixTagAttributes ($text, $element) |
| Take a tag soup fragment listing an HTML element's attributes and normalize it to well-formed XML, discarding unwanted attributes. More... | |
| static | encodeAttribute ($text) |
| Encode an attribute value for HTML output. More... | |
| static | safeEncodeAttribute ($text) |
| Encode an attribute value for HTML tags, with extra armoring against further wiki processing. More... | |
| static | escapeId ($id) |
| Given a value escape it so that it can be used in an id attribute and return it, this does not validate the value however (see first link) More... | |
| static | escapeClass ($class) |
| Given a value, escape it so that it can be used as a CSS class and return it. More... | |
| static | decodeTagAttributes ($text) |
| Return an associative array of attribute names and values from a partial tag string. More... | |
| static | normalizeCharReferences ($text) |
| Ensure that any entities and character references are legal for XML and XHTML specifically. More... | |
| static | normalizeCharReferencesCallback ($matches) |
| static | normalizeEntity ($name) |
| If the named entity is defined in the HTML 4.0/XHTML 1.0 DTD, return the named entity reference as is. More... | |
| static | decCharReference ($codepoint) |
| static | hexCharReference ($codepoint) |
| static | decodeCharReferences ($text) |
| Decode any character references, numeric or named entities, in the text and return a UTF-8 string. More... | |
| static | decodeCharReferencesCallback ($matches) |
| static | decodeChar ($codepoint) |
| Return UTF-8 string for a codepoint if that is a valid character reference, otherwise U+FFFD REPLACEMENT CHARACTER. More... | |
| static | decodeEntity ($name) |
| If the named entity is defined in the HTML 4.0/XHTML 1.0 DTD, return the UTF-8 encoding of that character. More... | |
| static | attributeWhitelist ($element) |
| Fetch the whitelist of acceptable attributes for a given element name. More... | |
| static | setupAttributeWhitelist () |
| static | stripAllTags ($text) |
| Take a fragment of (potentially invalid) HTML and return a version with any tags removed, encoded as plain text. More... | |
| static | hackDocType () |
| Hack up a private DOCTYPE with HTML's standard entity declarations. More... | |
| static | cleanUrl ($url, $hostname=true) |
Static Private Member Functions | |
| static | armorLinksCallback ($matches) |
| Regex replace callback for armoring links against further processing. More... | |
| static | getTagAttributeCallback ($set) |
| Pick the appropriate attribute value from a match set from the MW_ATTRIBS_REGEX matches. More... | |
| static | normalizeAttributeValue ($text) |
| Normalize whitespace and character references in an XML source- encoded text for an attribute value. More... | |
| static | normalizeWhitespace ($text) |
| static | validateCodepoint ($codepoint) |
| Returns true if a given Unicode codepoint is a valid character in XML. More... | |
Detailed Description
Definition at line 332 of file Sanitizer.php.
Member Function Documentation
◆ armorLinksCallback()
|
staticprivate |
Regex replace callback for armoring links against further processing.
- Parameters
-
array $matches
- Returns
- string
Definition at line 799 of file Sanitizer.php.
◆ attributeWhitelist()
|
static |
Fetch the whitelist of acceptable attributes for a given element name.
- Parameters
-
string $element
- Returns
- array
Definition at line 1091 of file Sanitizer.php.
◆ checkCss()
|
static |
Pick apart some CSS and check it for forbidden or unsafe structures.
Returns a sanitized string, or false if it was just too evil.
Currently URL references, 'expression', 'tps' are forbidden.
- Parameters
-
string $value
- Returns
- mixed
Definition at line 621 of file Sanitizer.php.
◆ cleanUrl()
|
static |
NOTE: The original preg_replace/e IMPLICITLY adds a forward-slash on double quotes This could be a bug, but we will just mimic this behaviour 1:1 for now.
Definition at line 1288 of file Sanitizer.php.
◆ decCharReference()
|
static |
Definition at line 974 of file Sanitizer.php.
◆ decodeChar()
|
static |
Return UTF-8 string for a codepoint if that is a valid character reference, otherwise U+FFFD REPLACEMENT CHARACTER.
- Parameters
-
int $codepoint
- Returns
- string
Definition at line 1053 of file Sanitizer.php.
◆ decodeCharReferences()
|
static |
Decode any character references, numeric or named entities, in the text and return a UTF-8 string.
- Parameters
-
string $text
- Returns
- string
Definition at line 1018 of file Sanitizer.php.
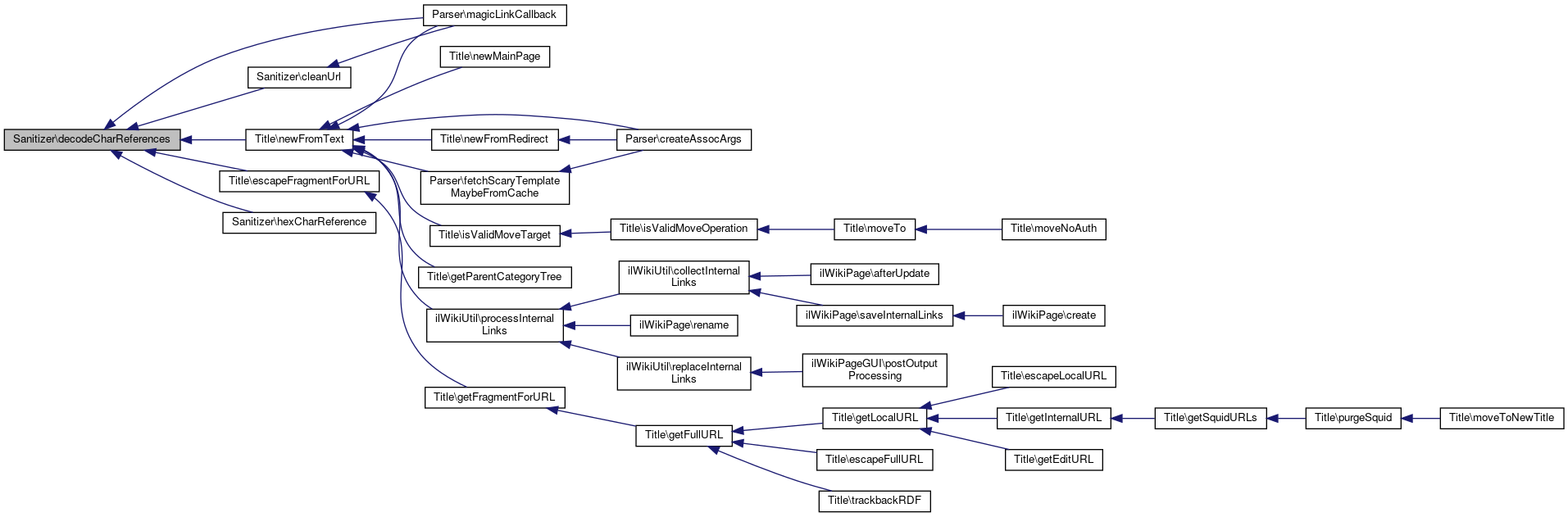
Referenced by Title\escapeFragmentForURL(), and Title\newFromText().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ decodeCharReferencesCallback()
|
static |
- Parameters
-
string $matches
- Returns
- string
Definition at line 1031 of file Sanitizer.php.
◆ decodeEntity()
|
static |
If the named entity is defined in the HTML 4.0/XHTML 1.0 DTD, return the UTF-8 encoding of that character.
Otherwise, returns pseudo-entity source (eg &foo;)
- Parameters
-
string $name
- Returns
- string
Definition at line 1070 of file Sanitizer.php.
◆ decodeTagAttributes()
|
static |
Return an associative array of attribute names and values from a partial tag string.
Attribute names are forces to lowercase, character references are decoded to UTF-8 text.
- Parameters
-
string
- Returns
- array
Definition at line 812 of file Sanitizer.php.
◆ encodeAttribute()
|
static |
Encode an attribute value for HTML output.
- Parameters
-
$text
- Returns
- HTML-encoded text fragment
Definition at line 695 of file Sanitizer.php.
◆ escapeClass()
|
static |
Given a value, escape it so that it can be used as a CSS class and return it.
- Todo:
- For extra validity, input should be validated UTF-8.
- See also
- http://www.w3.org/TR/CSS21/syndata.html Valid characters/format
- Parameters
-
string $class
- Returns
- string
Definition at line 783 of file Sanitizer.php.
◆ escapeId()
|
static |
Given a value escape it so that it can be used in an id attribute and return it, this does not validate the value however (see first link)
- See also
- http://www.w3.org/TR/html401/types.html#type-name Valid characters in the id and name attributes
- http://www.w3.org/TR/html401/struct/links.html#h-12.2.3 Anchors with the id attribute
- Parameters
-
string $id
- Returns
- string
Definition at line 760 of file Sanitizer.php.
◆ fixTagAttributes()
|
static |
Take a tag soup fragment listing an HTML element's attributes and normalize it to well-formed XML, discarding unwanted attributes.
Output is safe for further wikitext processing, with escaping of values that could trigger problems.
- Normalizes attribute names to lowercase
- Discards attributes not on a whitelist for the given element
- Turns broken or invalid entities into plaintext
- Double-quotes all attribute values
- Attributes without values are given the name as attribute
- Double attributes are discarded
- Unsafe style attributes are discarded
- Prepends space if there are attributes.
- Parameters
-
string $text string $element
- Returns
- string
Definition at line 669 of file Sanitizer.php.
◆ getTagAttributeCallback()
|
staticprivate |
Pick the appropriate attribute value from a match set from the MW_ATTRIBS_REGEX matches.
- Parameters
-
array $set
- Returns
- string
Definition at line 852 of file Sanitizer.php.
◆ hackDocType()
|
static |
Hack up a private DOCTYPE with HTML's standard entity declarations.
PHP 4 seemed to know these if you gave it an HTML doctype, but PHP 5.1 doesn't.
Use for passing XHTML fragments to PHP's XML parsing functions
- Returns
- string
Definition at line 1277 of file Sanitizer.php.
◆ hexCharReference()
|
static |
Definition at line 984 of file Sanitizer.php.
◆ normalizeAttributeValue()
|
staticprivate |
Normalize whitespace and character references in an XML source- encoded text for an attribute value.
See http://www.w3.org/TR/REC-xml/#AVNormalize for background, but note that we're not returning the value, but are returning XML source fragments that will be slapped into output.
- Parameters
-
string $text
- Returns
- string
Definition at line 887 of file Sanitizer.php.
◆ normalizeCharReferences()
|
static |
Ensure that any entities and character references are legal for XML and XHTML specifically.
Any stray bits will be &-escaped to result in a valid text fragment.
a. any named char refs must be known in XHTML b. any numeric char refs must be legal chars, not invalid or forbidden c. use &#x, not &#X d. fix or reject non-valid attributes
- Parameters
-
string $text
- Returns
- string
Definition at line 921 of file Sanitizer.php.
◆ normalizeCharReferencesCallback()
|
static |
- Parameters
-
string $matches
- Returns
- string
Definition at line 933 of file Sanitizer.php.
◆ normalizeEntity()
|
static |
If the named entity is defined in the HTML 4.0/XHTML 1.0 DTD, return the named entity reference as is.
If the entity is a MediaWiki-specific alias, returns the HTML equivalent. Otherwise, returns HTML-escaped text of pseudo-entity source (eg &foo;)
- Parameters
-
string $name
- Returns
- string
Definition at line 962 of file Sanitizer.php.
◆ normalizeWhitespace()
|
staticprivate |
Definition at line 898 of file Sanitizer.php.
◆ removeHTMLcomments()
|
static |
Remove '', and everything between.
To avoid leaving blank lines, when a comment is both preceded and followed by a newline (ignoring spaces), trim leading and trailing spaces and one of the newlines.
- Parameters
-
string $text
- Returns
- string
Definition at line 533 of file Sanitizer.php.
◆ removeHTMLtags()
|
static |
Cleans up HTML, removes dangerous tags and attributes, and removes HTML comments.
- Parameters
-
string $text callback $processCallback to do any variable or parameter replacements in HTML attribute values array $args for the processing callback
- Returns
- string
Definition at line 343 of file Sanitizer.php.
◆ safeEncodeAttribute()
|
static |
Encode an attribute value for HTML tags, with extra armoring against further wiki processing.
- Parameters
-
$text
- Returns
- HTML-encoded text fragment
Definition at line 717 of file Sanitizer.php.
◆ setupAttributeWhitelist()
|
static |
- Todo:
- Document it a bit
- Returns
- array
Definition at line 1106 of file Sanitizer.php.
◆ stripAllTags()
|
static |
Take a fragment of (potentially invalid) HTML and return a version with any tags removed, encoded as plain text.
Warning: this return value must be further escaped for literal inclusion in HTML output as of 1.10!
- Parameters
-
string $text HTML fragment
- Returns
- string
Definition at line 1255 of file Sanitizer.php.
◆ validateCodepoint()
|
staticprivate |
Returns true if a given Unicode codepoint is a valid character in XML.
- Parameters
-
int $codepoint
- Returns
- bool
Definition at line 999 of file Sanitizer.php.
◆ validateTagAttributes()
|
static |
Take an array of attribute names and values and normalize or discard illegal values for the given element type.
- Discards attributes not on a whitelist for the given element
- Unsafe style attributes are discarded
- Parameters
-
array $attribs string $element
- Returns
- array
- Todo:
Check for legal values where the DTD limits things.
Check for unique id attribute :P
Definition at line 583 of file Sanitizer.php.
The documentation for this class was generated from the following file:
- Services/Utilities/classes/Sanitizer.php