Collaboration diagram for SimpleSAML\Utils\Crypto:
Collaboration diagram for SimpleSAML\Utils\Crypto:Static Public Member Functions | |
| static | aesDecrypt ($ciphertext) |
| Decrypt data using AES-256-CBC and the system-wide secret salt as key. More... | |
| static | aesEncrypt ($data) |
| Encrypt data using AES-256-CBC and the system-wide secret salt as key. More... | |
| static | der2pem ($der, $type='CERTIFICATE') |
| Convert data from DER to PEM encoding. More... | |
| static | loadPrivateKey (\SimpleSAML_Configuration $metadata, $required=false, $prefix='', $full_path=false) |
| Load a private key from metadata. More... | |
| static | loadPublicKey (\SimpleSAML_Configuration $metadata, $required=false, $prefix='') |
| Get public key or certificate from metadata. More... | |
| static | pem2der ($pem) |
| Convert from PEM to DER encoding. More... | |
| static | pwHash ($password, $algorithm, $salt=null) |
| This function hashes a password with a given algorithm. More... | |
| static | secureCompare ($known, $user) |
| Compare two strings securely. More... | |
| static | pwValid ($hash, $password) |
| This function checks if a password is valid. More... | |
Detailed Description
Definition at line 10 of file Crypto.php.
Member Function Documentation
◆ aesDecrypt()
|
static |
Decrypt data using AES-256-CBC and the system-wide secret salt as key.
- Parameters
-
string $ciphertext The HMAC of the encrypted data, the IV used and the encrypted data, concatenated.
- Returns
- string The decrypted data.
- Exceptions
-
InvalidArgumentException If $ciphertext is not a string.
- Exceptions
-
SimpleSAML_Error_Exception If the openssl module is not loaded.
Definition at line 81 of file Crypto.php.
References SimpleSAML\Utils\Config\getSecretSalt().
Referenced by SimpleSAML_Utilities\aesDecrypt().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ aesEncrypt()
|
static |
Encrypt data using AES-256-CBC and the system-wide secret salt as key.
- Parameters
-
string $data The data to encrypt.
- Returns
- string An HMAC of the encrypted data, the IV and the encrypted data, concatenated.
- Exceptions
-
InvalidArgumentException If $data is not a string.
- Exceptions
-
SimpleSAML_Error_Exception If the openssl module is not loaded.
Definition at line 146 of file Crypto.php.
References $data, and SimpleSAML\Utils\Config\getSecretSalt().
Referenced by SimpleSAML_Utilities\aesEncrypt(), and SimpleSAML\Utils\HTTP\getSecurePOSTRedirectURL().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ der2pem()
|
static |
Convert data from DER to PEM encoding.
- Parameters
-
string $der Data encoded in DER format. string $type The type of data we are encoding, as expressed by the PEM header. Defaults to "CERTIFICATE".
- Returns
- string The same data encoded in PEM format.
- See also
- RFC7648 for known types and PEM format specifics.
Definition at line 160 of file Crypto.php.
Referenced by sspmod_authX509_Auth_Source_X509userCert\authenticate().
 Here is the caller graph for this function:
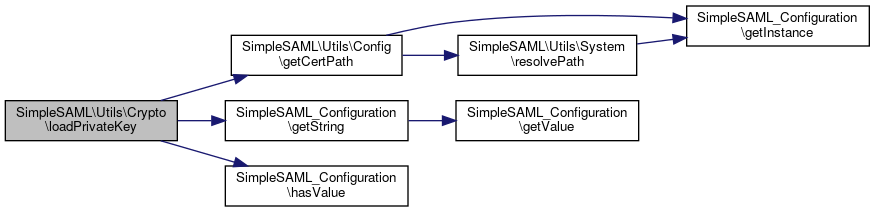
Here is the caller graph for this function:◆ loadPrivateKey()
|
static |
Load a private key from metadata.
This function loads a private key from a metadata array. It looks for the following elements:
- 'privatekey': Name of a private key file in the cert-directory.
- 'privatekey_pass': Password for the private key.
It returns and array with the following elements:
- 'PEM': Data for the private key, in PEM-format.
- 'password': Password for the private key.
- Parameters
-
\SimpleSAML_Configuration $metadata The metadata array the private key should be loaded from. bool $required Whether the private key is required. If this is true, a missing key will cause an exception. Defaults to false. string $prefix The prefix which should be used when reading from the metadata array. Defaults to ''. bool $full_path Whether the filename found in the configuration contains the full path to the private key or not. Default to false.
- Returns
- array|NULL Extracted private key, or NULL if no private key is present.
- Exceptions
-
InvalidArgumentException If $required is not boolean or $prefix is not a string.
- Exceptions
-
SimpleSAML_Error_Exception If no private key is found in the metadata, or it was not possible to load it.
Definition at line 195 of file Crypto.php.
References $data, $file, $metadata, $ret, and SimpleSAML\Utils\Config\getCertPath().
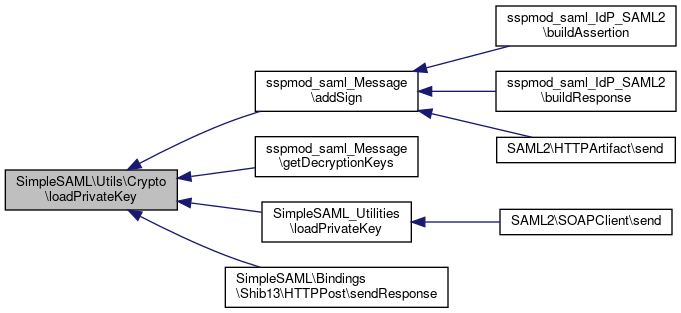
Referenced by sspmod_saml_Message\addSign(), sspmod_saml_Message\getDecryptionKeys(), SimpleSAML_Utilities\loadPrivateKey(), and SimpleSAML\Bindings\Shib13\HTTPPost\sendResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ loadPublicKey()
|
static |
Get public key or certificate from metadata.
This function implements a function to retrieve the public key or certificate from a metadata array.
It will search for the following elements in the metadata:
- 'certData': The certificate as a base64-encoded string.
- 'certificate': A file with a certificate or public key in PEM-format.
- 'certFingerprint': The fingerprint of the certificate. Can be a single fingerprint, or an array of multiple valid fingerprints. (deprecated)
This function will return an array with these elements:
- 'PEM': The public key/certificate in PEM-encoding.
- 'certData': The certificate data, base64 encoded, on a single line. (Only present if this is a certificate.)
- 'certFingerprint': Array of valid certificate fingerprints. (Deprecated. Only present if this is a certificate.)
- Parameters
-
\SimpleSAML_Configuration $metadata The metadata. bool $required Whether the private key is required. If this is TRUE, a missing key will cause an exception. Default is FALSE. string $prefix The prefix which should be used when reading from the metadata array. Defaults to ''.
- Returns
- array|NULL Public key or certificate data, or NULL if no public key or certificate was found.
- Exceptions
-
InvalidArgumentException If $metadata is not an instance of \SimpleSAML_Configuration, $required is not boolean or $prefix is not a string.
- Exceptions
-
SimpleSAML_Error_Exception If no private key is found in the metadata, or it was not possible to load it.
Definition at line 265 of file Crypto.php.
References $key, $keys, and $metadata.
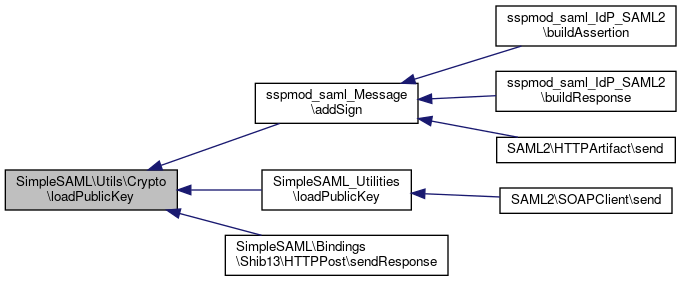
Referenced by sspmod_saml_Message\addSign(), SimpleSAML_Utilities\loadPublicKey(), and SimpleSAML\Bindings\Shib13\HTTPPost\sendResponse().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ pem2der()
|
static |
Convert from PEM to DER encoding.
- Parameters
-
string $pem Data encoded in PEM format.
- Returns
- string The same data encoded in DER format.
- Exceptions
-
InvalidArgumentException If $pem is not encoded in PEM format.
- See also
- RFC7648 for PEM format specifics.
Definition at line 327 of file Crypto.php.
References $end.
◆ pwHash()
|
static |
This function hashes a password with a given algorithm.
- Parameters
-
string $password The password to hash. string $algorithm The hashing algorithm, uppercase, optionally prepended with 'S' (salted). See hash_algos() for a complete list of hashing algorithms. string $salt An optional salt to use.
- Returns
- string The hashed password.
- Exceptions
-
InvalidArgumentException If the input parameters are not strings.
- Exceptions
-
SimpleSAML_Error_Exception If the algorithm specified is not supported.
- See also
- hash_algos()
Definition at line 365 of file Crypto.php.
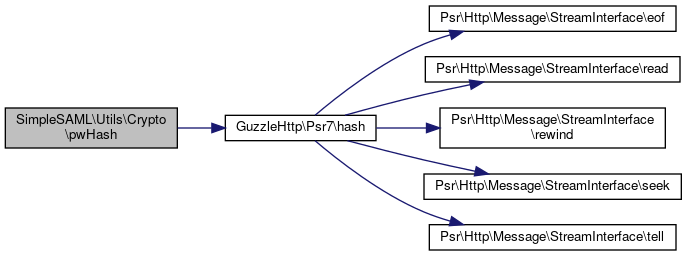
References $password, and GuzzleHttp\Psr7\hash().
 Here is the call graph for this function:
Here is the call graph for this function:◆ pwValid()
|
static |
This function checks if a password is valid.
- Parameters
-
string $hash The password as it appears in password file, optionally prepended with algorithm. string $password The password to check in clear.
- Returns
- boolean True if the hash corresponds with the given password, false otherwise.
- Exceptions
-
InvalidArgumentException If the input parameters are not strings.
- Exceptions
-
SimpleSAML_Error_Exception If the algorithm specified is not supported.
Definition at line 440 of file Crypto.php.
◆ secureCompare()
|
static |
Compare two strings securely.
This method checks if two strings are equal in constant time, avoiding timing attacks. Use it every time we need to compare a string with a secret that shouldn't be leaked, i.e. when verifying passwords, one-time codes, etc.
- Parameters
-
string $known A known string. string $user A user-provided string to compare with the known string.
- Returns
- bool True if both strings are equal, false otherwise.
Definition at line 407 of file Crypto.php.
The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/lib/SimpleSAML/Utils/Crypto.php