This is class for parsing of SAML 1.x and SAML 2.0 metadata. More...
 Collaboration diagram for SimpleSAML_Metadata_SAMLParser:
Collaboration diagram for SimpleSAML_Metadata_SAMLParser:Public Member Functions | |
| getEntityId () | |
| This function returns the entity id of this parsed entity. More... | |
| getMetadata1xSP () | |
| This function returns the metadata for SAML 1.x SPs in the format SimpleSAMLphp expects. More... | |
| getMetadata1xIdP () | |
| This function returns the metadata for SAML 1.x IdPs in the format SimpleSAMLphp expects. More... | |
| getMetadata20SP () | |
| This function returns the metadata for SAML 2.0 SPs in the format SimpleSAMLphp expects. More... | |
| getMetadata20IdP () | |
| This function returns the metadata for SAML 2.0 IdPs in the format SimpleSAMLphp expects. More... | |
| getAttributeAuthorities () | |
| Retrieve AttributeAuthorities from the metadata. More... | |
| validateSignature ($certificates) | |
| If this EntityDescriptor was signed this function use the public key to check the signature. More... | |
| validateFingerprint ($fingerprint) | |
| This function checks if this EntityDescriptor was signed with a certificate with the given fingerprint. More... | |
Static Public Member Functions | |
| static | parseFile ($file) |
| This function parses a file which contains XML encoded metadata. More... | |
| static | parseString ($metadata) |
| This function parses a string which contains XML encoded metadata. More... | |
| static | parseDocument ($document) |
| This function parses a DOMDocument which is assumed to contain a single EntityDescriptor element. More... | |
| static | parseElement ($entityElement) |
| This function parses a \SAML2\XML\md\EntityDescriptor object which represents a EntityDescriptor element. More... | |
| static | parseDescriptorsFile ($file) |
| This function parses a file where the root node is either an EntityDescriptor element or an EntitiesDescriptor element. More... | |
| static | parseDescriptorsString ($string) |
| This function parses a string with XML data. More... | |
| static | parseDescriptorsElement (DOMElement $element=null) |
| This function parses a DOMElement which represents either an EntityDescriptor element or an EntitiesDescriptor element. More... | |
Private Member Functions | |
| __construct (\SAML2\XML\md\EntityDescriptor $entityElement, $maxExpireTime, array $validators=array(), array $parentExtensions=null) | |
| This is the constructor for the SAMLParser class. More... | |
| getMetadataCommon () | |
| addExtensions (array &$metadata, array $roleDescriptor) | |
| Add data parsed from extensions to metadata. More... | |
| processSPSSODescriptor (\SAML2\XML\md\SPSSODescriptor $element, $expireTime) | |
| This function extracts metadata from a SPSSODescriptor element. More... | |
| processIDPSSODescriptor (\SAML2\XML\md\IDPSSODescriptor $element, $expireTime) | |
| This function extracts metadata from a IDPSSODescriptor element. More... | |
| processAttributeAuthorityDescriptor (\SAML2\XML\md\AttributeAuthorityDescriptor $element, $expireTime) | |
| This function extracts metadata from a AttributeAuthorityDescriptor element. More... | |
| processOrganization (\SAML2\XML\md\Organization $element) | |
| Parse and process a Organization element. More... | |
| processContactPerson (\SAML2\XML\md\ContactPerson $element) | |
| Parse and process a ContactPerson element. More... | |
| getSPDescriptors ($protocols) | |
| This function finds SP descriptors which supports one of the given protocols. More... | |
| getIdPDescriptors ($protocols) | |
| This function finds IdP descriptors which supports one of the given protocols. More... | |
Static Private Member Functions | |
| static | getExpireTime ($element, $maxExpireTime) |
| Determine how long a given element can be cached. More... | |
| static | parseRoleDescriptorType (\SAML2\XML\md\RoleDescriptor $element, $expireTime) |
| Parse a RoleDescriptorType element. More... | |
| static | parseSSODescriptor (\SAML2\XML\md\SSODescriptorType $element, $expireTime) |
| This function extracts metadata from a SSODescriptor element. More... | |
| static | processExtensions ($element, $parentExtensions=array()) |
| Parse an Extensions element. More... | |
| static | parseAttributeConsumerService (\SAML2\XML\md\AttributeConsumingService $element, &$sp) |
| This function parses AttributeConsumerService elements. More... | |
| static | parseGenericEndpoint (\SAML2\XML\md\EndpointType $element) |
| This function is a generic endpoint element parser. More... | |
| static | extractEndpoints (array $endpoints) |
| Extract generic endpoints. More... | |
| static | parseKeyDescriptor (\SAML2\XML\md\KeyDescriptor $kd) |
| This function parses a KeyDescriptor element. More... | |
| static | findEntityDescriptor ($doc) |
| This function locates the EntityDescriptor node in a DOMDocument. More... | |
Private Attributes | |
| $entityId | |
| $spDescriptors | |
| $idpDescriptors | |
| $attributeAuthorityDescriptors = array() | |
| $organizationName = array() | |
| $organizationDisplayName = array() | |
| $organizationURL = array() | |
| $contacts = array() | |
| $scopes | |
| $entityAttributes | |
| $registrationInfo | |
| $tags | |
| $validators = array() | |
| $entityDescriptor | |
Static Private Attributes | |
| static | $SAML1xProtocols |
| static | $SAML20Protocols |
Detailed Description
This is class for parsing of SAML 1.x and SAML 2.0 metadata.
Metadata is loaded by calling the static methods parseFile, parseString or parseElement. These functions returns an instance of SimpleSAML_Metadata_SAMLParser. To get metadata from this object, use the methods getMetadata1xSP or getMetadata20SP.
To parse a file which can contain a collection of EntityDescriptor or EntitiesDescriptor elements, use the parseDescriptorsFile, parseDescriptorsString or parseDescriptorsElement methods. These functions will return an array of SAMLParser elements where each element represents an EntityDescriptor-element.
Definition at line 15 of file SAMLParser.php.
Constructor & Destructor Documentation
◆ __construct()
|
private |
This is the constructor for the SAMLParser class.
- Parameters
-
\SAML2\XML\md\EntityDescriptor $entityElement The EntityDescriptor. int | NULL $maxExpireTime The unix timestamp for when this entity should expire, or NULL if unknown. array $validators An array of parent elements that may validate this element. array $parentExtensions An optional array of extensions from the parent element.
Definition at line 164 of file SAMLParser.php.
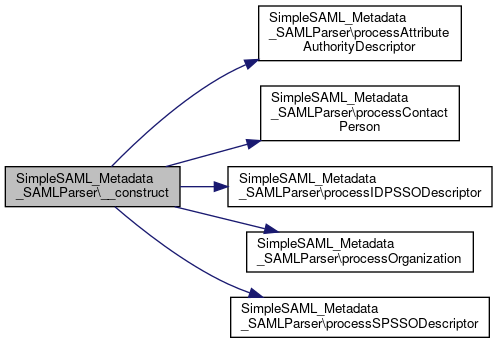
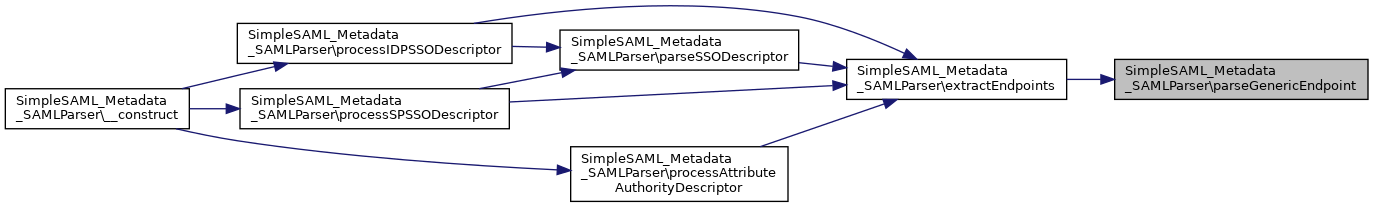
References $validators, getExpireTime(), processAttributeAuthorityDescriptor(), processContactPerson(), processExtensions(), processIDPSSODescriptor(), processOrganization(), and processSPSSODescriptor().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ addExtensions()
|
private |
Add data parsed from extensions to metadata.
- Parameters
-
array &$metadata The metadata that should be updated. array $roleDescriptor The parsed role descriptor.
Definition at line 487 of file SAMLParser.php.
References $entityAttributes, $metadata, $registrationInfo, $scopes, and $tags.
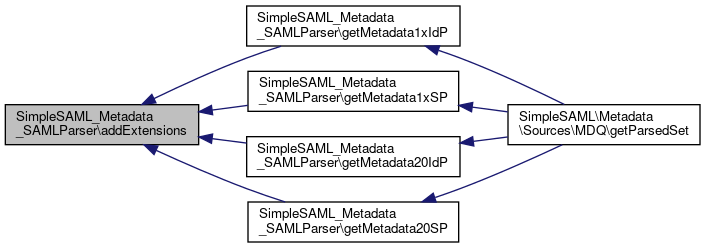
Referenced by getMetadata1xIdP(), getMetadata1xSP(), getMetadata20IdP(), and getMetadata20SP().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ extractEndpoints()
|
staticprivate |
Extract generic endpoints.
- Parameters
-
array $endpoints The endpoints we should parse.
- Returns
- array Array of parsed endpoints.
Definition at line 1293 of file SAMLParser.php.
References $ret, and parseGenericEndpoint().
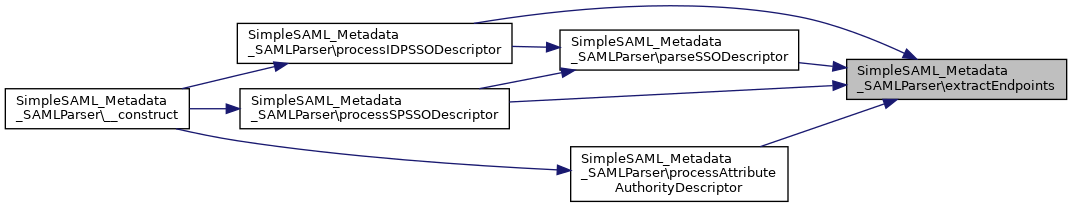
Referenced by parseSSODescriptor(), processAttributeAuthorityDescriptor(), processIDPSSODescriptor(), and processSPSSODescriptor().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ findEntityDescriptor()
|
staticprivate |
This function locates the EntityDescriptor node in a DOMDocument.
This node should be the first (and only) node in the document.
This function will throw an exception if it is unable to locate the node.
- Parameters
-
DOMDocument $doc The DOMDocument where we should find the EntityDescriptor node.
- Returns
- \SAML2\XML\md\EntityDescriptor The DOMEntity which represents the EntityDescriptor.
- Exceptions
-
Exception If the document is empty or the first element is not an EntityDescriptor element.
Definition at line 1410 of file SAMLParser.php.
Referenced by parseDocument().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getAttributeAuthorities()
| SimpleSAML_Metadata_SAMLParser::getAttributeAuthorities | ( | ) |
Retrieve AttributeAuthorities from the metadata.
- Returns
- array Array of AttributeAuthorityDescriptor entries.
Definition at line 823 of file SAMLParser.php.
References $attributeAuthorityDescriptors.
Referenced by SimpleSAML\Metadata\Sources\MDQ\getParsedSet().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getEntityId()
| SimpleSAML_Metadata_SAMLParser::getEntityId | ( | ) |
This function returns the entity id of this parsed entity.
- Returns
- string The entity id of this parsed entity.
Definition at line 448 of file SAMLParser.php.
References $entityId.
◆ getExpireTime()
|
staticprivate |
Determine how long a given element can be cached.
This function looks for the 'validUntil' attribute to determine how long a given XML-element is valid. It returns this as a unix timestamp.
- Parameters
-
mixed $element The element we should determine the expiry time of. int | NULL $maxExpireTime The maximum expiration time.
- Returns
- int The unix timestamp for when the element should expire. Will be NULL if no limit is set for the element.
Definition at line 430 of file SAMLParser.php.
References $expire.
Referenced by __construct(), and parseRoleDescriptorType().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getIdPDescriptors()
|
private |
This function finds IdP descriptors which supports one of the given protocols.
- Parameters
-
$protocols Array with the protocols we accept.
- Returns
- Array with IdP descriptors which supports one of the given protocols.
Definition at line 1382 of file SAMLParser.php.
References $ret.
Referenced by getMetadata1xIdP(), and getMetadata20IdP().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getMetadata1xIdP()
| SimpleSAML_Metadata_SAMLParser::getMetadata1xIdP | ( | ) |
This function returns the metadata for SAML 1.x IdPs in the format SimpleSAMLphp expects.
This is an associative array with the following fields:
- 'entityid': The entity id of the entity described in the metadata.
- 'name': Auto generated name for this entity. Currently set to the entity id.
- 'SingleSignOnService': String with the URL of the SSO service which supports the redirect binding.
- 'SingleLogoutService': String with the URL where we should send logout requests/responses.
- 'certData': X509Certificate for entity (if present).
- 'certFingerprint': Fingerprint of the X509Certificate from the metadata. (deprecated)
Metadata must be loaded with one of the parse functions before this function can be called.
- Returns
- array An associative array with metadata or NULL if we are unable to generate metadata for a SAML 1.x IdP.
Definition at line 612 of file SAMLParser.php.
References $idp, $ret, addExtensions(), getIdPDescriptors(), and getMetadataCommon().
Referenced by SimpleSAML\Metadata\Sources\MDQ\getParsedSet().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getMetadata1xSP()
| SimpleSAML_Metadata_SAMLParser::getMetadata1xSP | ( | ) |
This function returns the metadata for SAML 1.x SPs in the format SimpleSAMLphp expects.
This is an associative array with the following fields:
- 'entityid': The entity id of the entity described in the metadata.
- 'AssertionConsumerService': String with the URL of the assertion consumer service which supports the browser-post binding.
- 'certData': X509Certificate for entity (if present).
Metadata must be loaded with one of the parse functions before this function can be called.
- Returns
- array An associative array with metadata or NULL if we are unable to generate metadata for a SAML 1.x SP.
Definition at line 538 of file SAMLParser.php.
References $ret, addExtensions(), getMetadataCommon(), and getSPDescriptors().
Referenced by SimpleSAML\Metadata\Sources\MDQ\getParsedSet().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getMetadata20IdP()
| SimpleSAML_Metadata_SAMLParser::getMetadata20IdP | ( | ) |
This function returns the metadata for SAML 2.0 IdPs in the format SimpleSAMLphp expects.
This is an associative array with the following fields:
- 'entityid': The entity id of the entity described in the metadata.
- 'name': Auto generated name for this entity. Currently set to the entity id.
- 'SingleSignOnService': String with the URL of the SSO service which supports the redirect binding.
- 'SingleLogoutService': String with the URL where we should send logout requests(/responses).
- 'SingleLogoutServiceResponse': String where we should send logout responses (if this is different from the 'SingleLogoutService' endpoint.
- 'NameIDFormats': The name ID formats this IdP supports.
- 'certData': X509Certificate for entity (if present).
- 'certFingerprint': Fingerprint of the X509Certificate from the metadata. (deprecated)
Metadata must be loaded with one of the parse functions before this function can be called.
- Returns
- array An associative array with metadata or NULL if we are unable to generate metadata for a SAML 2.0 IdP.
Definition at line 765 of file SAMLParser.php.
References $idp, $ret, addExtensions(), getIdPDescriptors(), and getMetadataCommon().
Referenced by SimpleSAML\Metadata\Sources\MDQ\getParsedSet().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getMetadata20SP()
| SimpleSAML_Metadata_SAMLParser::getMetadata20SP | ( | ) |
This function returns the metadata for SAML 2.0 SPs in the format SimpleSAMLphp expects.
This is an associative array with the following fields:
- 'entityid': The entity id of the entity described in the metadata.
- 'AssertionConsumerService': String with the URL of the assertion consumer service which supports the browser-post binding.
- 'SingleLogoutService': String with the URL where we should send logout requests/responses.
- 'NameIDFormat': The name ID format this SP expects. This may be unset.
- 'certData': X509Certificate for entity (if present).
Metadata must be loaded with one of the parse functions before this function can be called.
- Returns
- array An associative array with metadata or NULL if we are unable to generate metadata for a SAML 2.x SP.
Definition at line 668 of file SAMLParser.php.
References $ret, addExtensions(), getMetadataCommon(), and getSPDescriptors().
Referenced by SimpleSAML\Metadata\Sources\MDQ\getParsedSet().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getMetadataCommon()
|
private |
Definition at line 454 of file SAMLParser.php.
References $contacts, $entityDescriptor, $entityId, $organizationDisplayName, $organizationName, $organizationURL, and $ret.
Referenced by getMetadata1xIdP(), getMetadata1xSP(), getMetadata20IdP(), and getMetadata20SP().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getSPDescriptors()
|
private |
This function finds SP descriptors which supports one of the given protocols.
- Parameters
-
$protocols Array with the protocols we accept.
- Returns
- Array with SP descriptors which supports one of the given protocols.
Definition at line 1358 of file SAMLParser.php.
References $ret.
Referenced by getMetadata1xSP(), and getMetadata20SP().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseAttributeConsumerService()
|
staticprivate |
This function parses AttributeConsumerService elements.
- Parameters
-
\SAML2\XML\md\AttributeConsumingService $element The AttributeConsumingService to parse. array $sp The array with the SP's metadata.
Definition at line 1204 of file SAMLParser.php.
References $format, and SAML2\Constants\NAMEFORMAT_UNSPECIFIED.
Referenced by processSPSSODescriptor().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseDescriptorsElement()
|
static |
This function parses a DOMElement which represents either an EntityDescriptor element or an EntitiesDescriptor element.
It will return an associative array of SAMLParser instances in both cases.
- Parameters
-
DOMElement | NULL $element The DOMElement which contains the EntityDescriptor element or the EntitiesDescriptor element.
- Returns
- SimpleSAML_Metadata_SAMLParser[] An associative array of SAMLParser instances. The key of the array will be the entity id.
- Exceptions
-
Exception if the document is empty or the root is an unexpected node.
Definition at line 359 of file SAMLParser.php.
Referenced by sspmod_metarefresh_MetaLoader\loadXML(), parseDescriptorsFile(), and parseDescriptorsString().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseDescriptorsFile()
|
static |
This function parses a file where the root node is either an EntityDescriptor element or an EntitiesDescriptor element.
In both cases it will return an associative array of SAMLParser instances. If the file contains a single EntityDescriptorElement, then the array will contain a single SAMLParser instance.
- Parameters
-
string $file The path to the file which contains the EntityDescriptor or EntitiesDescriptor element.
- Returns
- SimpleSAML_Metadata_SAMLParser[] An array of SAMLParser instances.
- Exceptions
-
Exception If the file does not parse as XML.
Definition at line 302 of file SAMLParser.php.
References $data, $file, SimpleSAML\Utils\HTTP\fetch(), SAML2\DOMDocumentFactory\fromString(), and parseDescriptorsElement().
Referenced by SimpleSAML_Metadata_MetaDataStorageHandlerXML\__construct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseDescriptorsString()
|
static |
This function parses a string with XML data.
The root node of the XML data is expected to be either an EntityDescriptor element or an EntitiesDescriptor element. It will return an associative array of SAMLParser instances.
- Parameters
-
string $string The string with XML data.
- Returns
- SimpleSAML_Metadata_SAMLParser[] An associative array of SAMLParser instances. The key of the array will be the entity id.
- Exceptions
-
Exception If the string does not parse as XML.
Definition at line 336 of file SAMLParser.php.
References SAML2\DOMDocumentFactory\fromString(), and parseDescriptorsElement().
 Here is the call graph for this function:
Here is the call graph for this function:◆ parseDocument()
|
static |
This function parses a DOMDocument which is assumed to contain a single EntityDescriptor element.
- Parameters
-
DOMDocument $document The DOMDocument which contains the EntityDescriptor element.
- Returns
- SimpleSAML_Metadata_SAMLParser An instance of this class with the metadata loaded.
Definition at line 265 of file SAMLParser.php.
References findEntityDescriptor(), and parseElement().
Referenced by parseFile(), and parseString().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseElement()
|
static |
This function parses a \SAML2\XML\md\EntityDescriptor object which represents a EntityDescriptor element.
- Parameters
-
\SAML2\XML\md\EntityDescriptor $entityElement A \SAML2\XML\md\EntityDescriptor object which represents a EntityDescriptor element.
- Returns
- SimpleSAML_Metadata_SAMLParser An instance of this class with the metadata loaded.
Definition at line 283 of file SAMLParser.php.
Referenced by parseDocument().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseFile()
|
static |
This function parses a file which contains XML encoded metadata.
- Parameters
-
string $file The path to the file which contains the metadata.
- Returns
- SimpleSAML_Metadata_SAMLParser An instance of this class with the metadata loaded.
- Exceptions
-
Exception If the file does not parse as XML.
Definition at line 224 of file SAMLParser.php.
References $data, $file, SimpleSAML\Utils\HTTP\fetch(), SAML2\DOMDocumentFactory\fromString(), and parseDocument().
 Here is the call graph for this function:
Here is the call graph for this function:◆ parseGenericEndpoint()
|
staticprivate |
This function is a generic endpoint element parser.
The returned associative array has the following elements:
- 'Binding': The binding this endpoint uses.
- 'Location': The URL to this endpoint.
- 'ResponseLocation': The URL where responses should be sent. This may not exist.
- 'index': The index of this endpoint. This attribute is only for indexed endpoints.
- 'isDefault': Whether this endpoint is the default endpoint for this type. This attribute may not exist.
- Parameters
-
\SAML2\XML\md\EndpointType $element The element which should be parsed.
- Returns
- array An associative array with the data we have extracted from the element.
Definition at line 1263 of file SAMLParser.php.
Referenced by extractEndpoints().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseKeyDescriptor()
|
staticprivate |
This function parses a KeyDescriptor element.
It currently only supports keys with a single X509 certificate.
The associative array for a key can contain:
- 'encryption': Indicates whether this key can be used for encryption.
- 'signing': Indicates whether this key can be used for signing.
- 'type: The type of the key. 'X509Certificate' is the only key type we support.
- 'X509Certificate': The contents of the first X509Certificate element (if the type is 'X509Certificate ').
- Parameters
-
\SAML2\XML\md\KeyDescriptor $kd The KeyDescriptor element.
- Returns
- array|null An associative array describing the key, or null if this is an unsupported key.
Definition at line 1318 of file SAMLParser.php.
Referenced by parseRoleDescriptorType().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseRoleDescriptorType()
|
staticprivate |
Parse a RoleDescriptorType element.
The returned associative array has the following elements:
- 'protocols': Array with the protocols supported.
- 'expire': Timestamp for when this descriptor expires.
- 'keys': Array of associative arrays with the elements from parseKeyDescriptor.
- Parameters
-
\SAML2\XML\md\RoleDescriptor $element The element we should extract metadata from. int | NULL $expireTime The unix timestamp for when this element should expire, or NULL if unknown.
- Returns
- array An associative array with metadata we have extracted from this element.
Definition at line 843 of file SAMLParser.php.
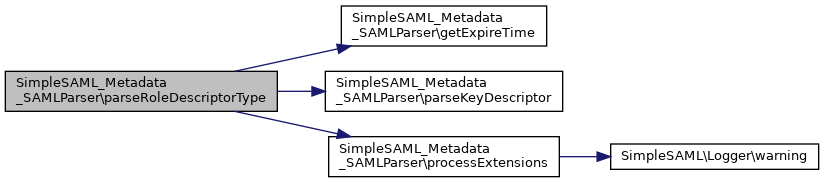
References $key, $ret, getExpireTime(), parseKeyDescriptor(), and processExtensions().
Referenced by parseSSODescriptor(), and processAttributeAuthorityDescriptor().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseSSODescriptor()
|
staticprivate |
This function extracts metadata from a SSODescriptor element.
The returned associative array has the following elements:
- 'protocols': Array with the protocols this SSODescriptor supports.
- 'SingleLogoutService': Array with the single logout service endpoints. Each endpoint is stored as an associative array with the elements that parseGenericEndpoint returns.
- 'nameIDFormats': The NameIDFormats supported by this SSODescriptor. This may be an empty array.
- 'keys': Array of associative arrays with the elements from parseKeyDescriptor:
- Parameters
-
\SAML2\XML\md\SSODescriptorType $element The element we should extract metadata from. int | NULL $expireTime The unix timestamp for when this element should expire, or NULL if unknown.
- Returns
- array An associative array with metadata we have extracted from this element.
Definition at line 894 of file SAMLParser.php.
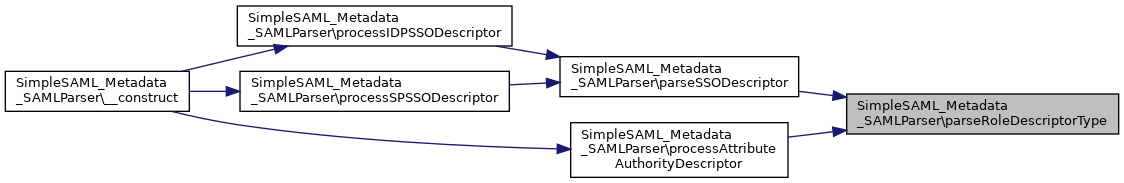
References extractEndpoints(), and parseRoleDescriptorType().
Referenced by processIDPSSODescriptor(), and processSPSSODescriptor().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseString()
|
static |
This function parses a string which contains XML encoded metadata.
- Parameters
-
string $metadata A string which contains XML encoded metadata.
- Returns
- SimpleSAML_Metadata_SAMLParser An instance of this class with the metadata loaded.
- Exceptions
-
Exception If the string does not parse as XML.
Definition at line 246 of file SAMLParser.php.
References $metadata, SAML2\DOMDocumentFactory\fromString(), and parseDocument().
 Here is the call graph for this function:
Here is the call graph for this function:◆ processAttributeAuthorityDescriptor()
|
private |
This function extracts metadata from a AttributeAuthorityDescriptor element.
- Parameters
-
\SAML2\XML\md\AttributeAuthorityDescriptor $element The element which should be parsed. int | NULL $expireTime The unix timestamp for when this element should expire, or NULL if unknown.
Definition at line 983 of file SAMLParser.php.
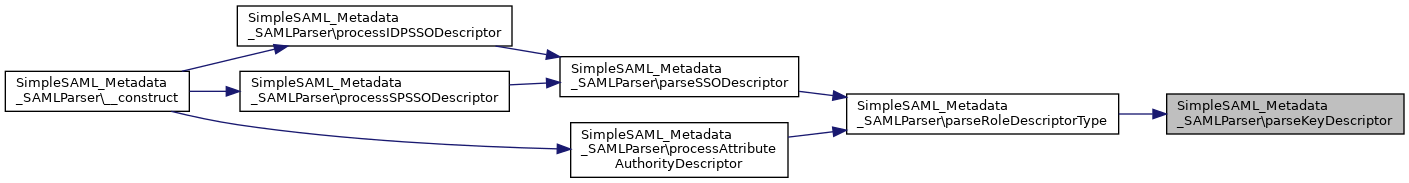
References $entityId, extractEndpoints(), and parseRoleDescriptorType().
Referenced by __construct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ processContactPerson()
|
private |
Parse and process a ContactPerson element.
- Parameters
-
\SAML2\XML\md\ContactPerson $element The ContactPerson element.
Definition at line 1171 of file SAMLParser.php.
Referenced by __construct().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ processExtensions()
|
staticprivate |
Parse an Extensions element.
Extensions may appear in multiple elements and certain extension may get inherited from a parent element.
- Parameters
-
mixed $element The element which contains the Extensions element. array $parentExtensions An optional array of extensions from the parent element.
- Returns
- array An associative array with the extensions parsed.
Definition at line 1010 of file SAMLParser.php.
References $name, $ret, and SimpleSAML\Logger\warning().
Referenced by __construct(), and parseRoleDescriptorType().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ processIDPSSODescriptor()
|
private |
This function extracts metadata from a IDPSSODescriptor element.
- Parameters
-
\SAML2\XML\md\IDPSSODescriptor $element The element which should be parsed. int | NULL $expireTime The unix timestamp for when this element should expire, or NULL if unknown.
Definition at line 957 of file SAMLParser.php.
References $idp, extractEndpoints(), and parseSSODescriptor().
Referenced by __construct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ processOrganization()
|
private |
Parse and process a Organization element.
- Parameters
-
\SAML2\XML\md\Organization $element The Organization element.
Definition at line 1157 of file SAMLParser.php.
Referenced by __construct().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ processSPSSODescriptor()
|
private |
This function extracts metadata from a SPSSODescriptor element.
- Parameters
-
\SAML2\XML\md\SPSSODescriptor $element The element which should be parsed. int | NULL $expireTime The unix timestamp for when this element should expire, or NULL if unknown.
Definition at line 921 of file SAMLParser.php.
References extractEndpoints(), parseAttributeConsumerService(), and parseSSODescriptor().
Referenced by __construct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ validateFingerprint()
| SimpleSAML_Metadata_SAMLParser::validateFingerprint | ( | $fingerprint | ) |
This function checks if this EntityDescriptor was signed with a certificate with the given fingerprint.
- Parameters
-
string $fingerprint Fingerprint of the certificate which should have been used to sign this EntityDescriptor.
- Returns
- boolean True if it was signed with the certificate with the given fingerprint, false otherwise.
Definition at line 1476 of file SAMLParser.php.
References SimpleSAML\Logger\debug().
 Here is the call graph for this function:
Here is the call graph for this function:◆ validateSignature()
| SimpleSAML_Metadata_SAMLParser::validateSignature | ( | $certificates | ) |
If this EntityDescriptor was signed this function use the public key to check the signature.
- Parameters
-
array $certificates One ore more certificates with the public key. This makes it possible to do a key rollover.
- Returns
- boolean True if it is possible to check the signature with the certificate, false otherwise.
- Exceptions
-
Exception If the certificate file cannot be found.
Definition at line 1438 of file SAMLParser.php.
References $certificates, $key, SimpleSAML\Logger\debug(), and SimpleSAML\Utils\Config\getCertPath().
 Here is the call graph for this function:
Here is the call graph for this function:Field Documentation
◆ $attributeAuthorityDescriptors
|
private |
Definition at line 76 of file SAMLParser.php.
Referenced by getAttributeAuthorities().
◆ $contacts
|
private |
Definition at line 113 of file SAMLParser.php.
Referenced by getMetadataCommon().
◆ $entityAttributes
|
private |
Definition at line 125 of file SAMLParser.php.
Referenced by addExtensions().
◆ $entityDescriptor
|
private |
Definition at line 152 of file SAMLParser.php.
Referenced by getMetadataCommon().
◆ $entityId
|
private |
Definition at line 44 of file SAMLParser.php.
Referenced by getEntityId(), getMetadataCommon(), and processAttributeAuthorityDescriptor().
◆ $idpDescriptors
|
private |
Definition at line 68 of file SAMLParser.php.
◆ $organizationDisplayName
|
private |
Definition at line 96 of file SAMLParser.php.
Referenced by getMetadataCommon().
◆ $organizationName
|
private |
Definition at line 86 of file SAMLParser.php.
Referenced by getMetadataCommon().
◆ $organizationURL
|
private |
Definition at line 105 of file SAMLParser.php.
Referenced by getMetadataCommon().
◆ $registrationInfo
|
private |
Definition at line 131 of file SAMLParser.php.
Referenced by addExtensions().
◆ $SAML1xProtocols
|
staticprivate |
Definition at line 23 of file SAMLParser.php.
◆ $SAML20Protocols
|
staticprivate |
Definition at line 34 of file SAMLParser.php.
◆ $scopes
|
private |
Definition at line 119 of file SAMLParser.php.
Referenced by addExtensions().
◆ $spDescriptors
|
private |
Definition at line 57 of file SAMLParser.php.
◆ $tags
|
private |
Definition at line 136 of file SAMLParser.php.
Referenced by addExtensions().
◆ $validators
|
private |
Definition at line 144 of file SAMLParser.php.
Referenced by __construct().
The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/lib/SimpleSAML/Metadata/SAMLParser.php