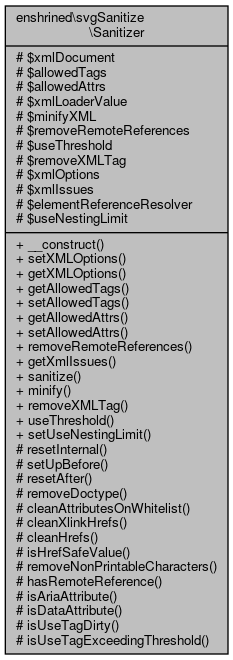
Collaboration diagram for enshrined\svgSanitize\Sanitizer:
Collaboration diagram for enshrined\svgSanitize\Sanitizer:Public Member Functions | |
| __construct () | |
| setXMLOptions ($xmlOptions) | |
| Set XML options to use when saving XML See: DOMDocument::saveXML. More... | |
| getXMLOptions () | |
| Get XML options to use when saving XML See: DOMDocument::saveXML. More... | |
| getAllowedTags () | |
| Get the array of allowed tags. More... | |
| setAllowedTags (TagInterface $allowedTags) | |
| Set custom allowed tags. More... | |
| getAllowedAttrs () | |
| Get the array of allowed attributes. More... | |
| setAllowedAttrs (AttributeInterface $allowedAttrs) | |
| Set custom allowed attributes. More... | |
| removeRemoteReferences ($removeRemoteRefs=false) | |
| Should we remove references to remote files? More... | |
| getXmlIssues () | |
| Get XML issues. More... | |
| sanitize ($dirty) | |
| Sanitize the passed string. More... | |
| minify ($shouldMinify=false) | |
| Should we minify the output? More... | |
| removeXMLTag ($removeXMLTag=false) | |
| Should we remove the XML tag in the header? More... | |
| useThreshold ($useThreshold=1000) | |
Whether <use ... xlink:href="#identifier"> elements shall be removed in case expansion would exceed this threshold. More... | |
| setUseNestingLimit ($limit) | |
| Set the nesting limit for <use> tags. More... | |
Protected Member Functions | |
| resetInternal () | |
| Set up the DOMDocument. More... | |
| setUpBefore () | |
| Set up libXML before we start. More... | |
| resetAfter () | |
| Reset the class after use. More... | |
| removeDoctype () | |
| Remove the XML Doctype It may be caught later on output but that seems to be buggy, so we need to make sure it's gone. More... | |
| cleanAttributesOnWhitelist (\DOMElement $element) | |
| Only allow attributes that are on the whitelist. More... | |
| cleanXlinkHrefs (\DOMElement $element) | |
| Clean the xlink:hrefs of script and data embeds. More... | |
| cleanHrefs (\DOMElement $element) | |
| Clean the hrefs of script and data embeds. More... | |
| isHrefSafeValue ($value) | |
| Only allow whitelisted starts to be within the href. More... | |
| removeNonPrintableCharacters ($value) | |
| Removes non-printable ASCII characters from string & trims it. More... | |
| hasRemoteReference ($value) | |
| Does this attribute value have a remote reference? More... | |
| isAriaAttribute ($attributeName) | |
| Check to see if an attribute is an aria attribute or not. More... | |
| isDataAttribute ($attributeName) | |
| Check to see if an attribute is an data attribute or not. More... | |
| isUseTagDirty (\DOMElement $element) | |
| Make sure our use tag is only referencing internal resources. More... | |
| isUseTagExceedingThreshold (\DOMElement $element) | |
Determines whether <use ... xlink:href="#identifier"> is expanded recursively in order to create DoS scenarios. More... | |
Protected Attributes | |
| $xmlDocument | |
| $allowedTags | |
| $allowedAttrs | |
| $xmlLoaderValue | |
| $minifyXML = false | |
| $removeRemoteReferences = false | |
| $useThreshold = 1000 | |
| $removeXMLTag = false | |
| $xmlOptions = LIBXML_NOEMPTYTAG | |
| $xmlIssues = array() | |
| $elementReferenceResolver | |
| $useNestingLimit = 15 | |
Detailed Description
Definition at line 18 of file Sanitizer.php.
Constructor & Destructor Documentation
◆ __construct()
| enshrined\svgSanitize\Sanitizer::__construct | ( | ) |
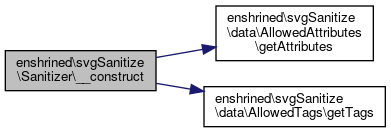
Definition at line 84 of file Sanitizer.php.
References enshrined\svgSanitize\data\AllowedAttributes\getAttributes(), and enshrined\svgSanitize\data\AllowedTags\getTags().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ cleanAttributesOnWhitelist()
|
protected |
Only allow attributes that are on the whitelist.
- Parameters
-
\DOMElement $element
This is used for when a namespace isn't imported properly. Such as xlink:href when the xlink namespace isn't imported. We have to do this as the link is still ran in this case.
Definition at line 347 of file Sanitizer.php.
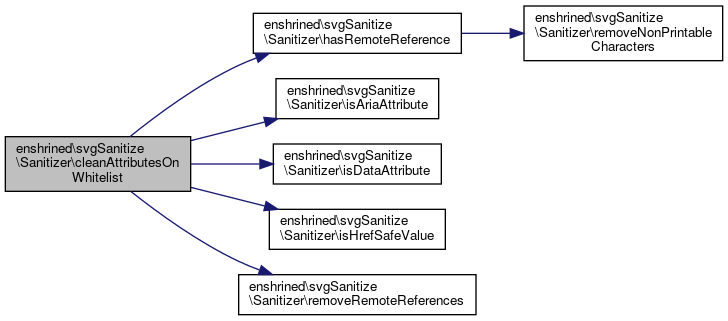
References $x, enshrined\svgSanitize\Sanitizer\isAriaAttribute(), enshrined\svgSanitize\Sanitizer\isDataAttribute(), enshrined\svgSanitize\Sanitizer\isHrefSafeValue(), and enshrined\svgSanitize\Sanitizer\removeRemoteReferences().
 Here is the call graph for this function:
Here is the call graph for this function:◆ cleanHrefs()
|
protected |
Clean the hrefs of script and data embeds.
- Parameters
-
\DOMElement $element
Definition at line 415 of file Sanitizer.php.
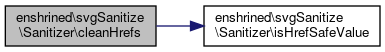
References enshrined\svgSanitize\Sanitizer\isHrefSafeValue().
 Here is the call graph for this function:
Here is the call graph for this function:◆ cleanXlinkHrefs()
|
protected |
Clean the xlink:hrefs of script and data embeds.
- Parameters
-
\DOMElement $element
Definition at line 398 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\isHrefSafeValue().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getAllowedAttrs()
| enshrined\svgSanitize\Sanitizer::getAllowedAttrs | ( | ) |
Get the array of allowed attributes.
- Returns
- array
Definition at line 149 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\$allowedAttrs.
◆ getAllowedTags()
| enshrined\svgSanitize\Sanitizer::getAllowedTags | ( | ) |
Get the array of allowed tags.
- Returns
- array
Definition at line 129 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\$allowedTags.
◆ getXmlIssues()
| enshrined\svgSanitize\Sanitizer::getXmlIssues | ( | ) |
Get XML issues.
- Returns
- array
Definition at line 179 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\$xmlIssues.
◆ getXMLOptions()
| enshrined\svgSanitize\Sanitizer::getXMLOptions | ( | ) |
Get XML options to use when saving XML See: DOMDocument::saveXML.
- Returns
- int
Definition at line 119 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\$xmlOptions.
◆ hasRemoteReference()
|
protected |
Does this attribute value have a remote reference?
- Parameters
-
$value
- Returns
- bool
Definition at line 500 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\removeNonPrintableCharacters().
 Here is the call graph for this function:
Here is the call graph for this function:◆ isAriaAttribute()
|
protected |
Check to see if an attribute is an aria attribute or not.
- Parameters
-
$attributeName
- Returns
- bool
Definition at line 552 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\cleanAttributesOnWhitelist().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ isDataAttribute()
|
protected |
Check to see if an attribute is an data attribute or not.
- Parameters
-
$attributeName
- Returns
- bool
Definition at line 564 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\cleanAttributesOnWhitelist().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ isHrefSafeValue()
|
protected |
Only allow whitelisted starts to be within the href.
This will stop scripts etc from being passed through, with or without attempting to hide bypasses. This stops the need for us to use a complicated script regex.
- Parameters
-
$value
- Returns
- bool
Definition at line 436 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\cleanAttributesOnWhitelist(), enshrined\svgSanitize\Sanitizer\cleanHrefs(), and enshrined\svgSanitize\Sanitizer\cleanXlinkHrefs().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ isUseTagDirty()
|
protected |
Make sure our use tag is only referencing internal resources.
- Parameters
-
\DOMElement $element
- Returns
- bool
Definition at line 575 of file Sanitizer.php.
◆ isUseTagExceedingThreshold()
|
protected |
Determines whether <use ... xlink:href="#identifier"> is expanded recursively in order to create DoS scenarios.
The amount of a actually used element needs to be below $this->useThreshold.
- Parameters
-
\DOMElement $element
- Returns
- bool
Definition at line 589 of file Sanitizer.php.
◆ minify()
| enshrined\svgSanitize\Sanitizer::minify | ( | $shouldMinify = false | ) |
Should we minify the output?
- Parameters
-
bool $shouldMinify
Definition at line 519 of file Sanitizer.php.
◆ removeDoctype()
|
protected |
Remove the XML Doctype It may be caught later on output but that seems to be buggy, so we need to make sure it's gone.
Definition at line 271 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ removeNonPrintableCharacters()
|
protected |
Removes non-printable ASCII characters from string & trims it.
- Parameters
-
string $value
- Returns
- bool
Definition at line 489 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\hasRemoteReference().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ removeRemoteReferences()
| enshrined\svgSanitize\Sanitizer::removeRemoteReferences | ( | $removeRemoteRefs = false | ) |
Should we remove references to remote files?
- Parameters
-
bool $removeRemoteRefs
Definition at line 169 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\removeRemoteReferences().
Referenced by enshrined\svgSanitize\Sanitizer\cleanAttributesOnWhitelist(), and enshrined\svgSanitize\Sanitizer\removeRemoteReferences().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ removeXMLTag()
| enshrined\svgSanitize\Sanitizer::removeXMLTag | ( | $removeXMLTag = false | ) |
Should we remove the XML tag in the header?
- Parameters
-
bool $removeXMLTag
Definition at line 529 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ resetAfter()
|
protected |
Reset the class after use.
Definition at line 261 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ resetInternal()
|
protected |
Set up the DOMDocument.
Definition at line 94 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\$minifyXML.
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ sanitize()
| enshrined\svgSanitize\Sanitizer::sanitize | ( | $dirty | ) |
Sanitize the passed string.
- Parameters
-
string $dirty
- Returns
- string
Definition at line 190 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\removeDoctype(), enshrined\svgSanitize\Sanitizer\removeXMLTag(), enshrined\svgSanitize\Sanitizer\resetAfter(), enshrined\svgSanitize\Sanitizer\resetInternal(), and enshrined\svgSanitize\Sanitizer\setUpBefore().
 Here is the call graph for this function:
Here is the call graph for this function:◆ setAllowedAttrs()
| enshrined\svgSanitize\Sanitizer::setAllowedAttrs | ( | AttributeInterface | $allowedAttrs | ) |
Set custom allowed attributes.
- Parameters
-
AttributeInterface $allowedAttrs
Definition at line 159 of file Sanitizer.php.
◆ setAllowedTags()
| enshrined\svgSanitize\Sanitizer::setAllowedTags | ( | TagInterface | $allowedTags | ) |
Set custom allowed tags.
- Parameters
-
TagInterface $allowedTags
Definition at line 139 of file Sanitizer.php.
◆ setUpBefore()
|
protected |
Set up libXML before we start.
Definition at line 246 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\sanitize().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ setUseNestingLimit()
| enshrined\svgSanitize\Sanitizer::setUseNestingLimit | ( | $limit | ) |
Set the nesting limit for <use> tags.
- Parameters
-
$limit
Definition at line 613 of file Sanitizer.php.
◆ setXMLOptions()
| enshrined\svgSanitize\Sanitizer::setXMLOptions | ( | $xmlOptions | ) |
Set XML options to use when saving XML See: DOMDocument::saveXML.
- Parameters
-
int $xmlOptions
Definition at line 108 of file Sanitizer.php.
References enshrined\svgSanitize\Sanitizer\$xmlOptions.
◆ useThreshold()
| enshrined\svgSanitize\Sanitizer::useThreshold | ( | $useThreshold = 1000 | ) |
Whether <use ... xlink:href="#identifier"> elements shall be removed in case expansion would exceed this threshold.
- Parameters
-
int $useThreshold
Definition at line 540 of file Sanitizer.php.
Field Documentation
◆ $allowedAttrs
|
protected |
Definition at line 34 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\getAllowedAttrs().
◆ $allowedTags
|
protected |
Definition at line 29 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\getAllowedTags().
◆ $elementReferenceResolver
|
protected |
Definition at line 74 of file Sanitizer.php.
◆ $minifyXML
|
protected |
Definition at line 44 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\resetInternal().
◆ $removeRemoteReferences
|
protected |
Definition at line 49 of file Sanitizer.php.
◆ $removeXMLTag
|
protected |
Definition at line 59 of file Sanitizer.php.
◆ $useNestingLimit
|
protected |
Definition at line 79 of file Sanitizer.php.
◆ $useThreshold
|
protected |
Definition at line 54 of file Sanitizer.php.
◆ $xmlDocument
|
protected |
Definition at line 24 of file Sanitizer.php.
◆ $xmlIssues
|
protected |
Definition at line 69 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\getXmlIssues().
◆ $xmlLoaderValue
|
protected |
Definition at line 39 of file Sanitizer.php.
◆ $xmlOptions
|
protected |
Definition at line 64 of file Sanitizer.php.
Referenced by enshrined\svgSanitize\Sanitizer\getXMLOptions(), and enshrined\svgSanitize\Sanitizer\setXMLOptions().
The documentation for this class was generated from the following file:
- libs/composer/vendor/enshrined/svg-sanitize/src/Sanitizer.php