Collaboration diagram for sspmod_adfs_IdP_ADFS:
Collaboration diagram for sspmod_adfs_IdP_ADFS:Static Public Member Functions | |
| static | receiveAuthnRequest (SimpleSAML_IdP $idp) |
| static | sendResponse (array $state) |
| static | sendLogoutResponse (SimpleSAML_IdP $idp, array $state) |
| static | receiveLogoutMessage (SimpleSAML_IdP $idp) |
| static | getLogoutURL (SimpleSAML_IdP $idp, array $association, $relayState) |
Static Private Member Functions | |
| static | generateResponse ($issuer, $target, $nameid, $attributes) |
| static | signResponse ($response, $key, $cert) |
| static | postResponse ($url, $wresult, $wctx) |
Detailed Description
Member Function Documentation
◆ generateResponse()
|
staticprivate |
Definition at line 31 of file ADFS.php.
References $attributes, $name, $nameid, $namespace, $result, $target, SimpleSAML\Utils\Random\generateID(), SimpleSAML\Utils\Time\generateTimestamp(), SimpleSAML\Utils\Attributes\getAttributeNamespace(), and NotOnOrAfter.
Referenced by sendResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getLogoutURL()
|
static |
Definition at line 209 of file ADFS.php.
References $association, $idp, $idpMetadata, $metadata, $relayState, $returnTo, $spMetadata, SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), and SimpleSAML\Module\getModuleURL().
 Here is the call graph for this function:
Here is the call graph for this function:◆ postResponse()
|
staticprivate |
Definition at line 120 of file ADFS.php.
Referenced by sendResponse().
 Here is the caller graph for this function:
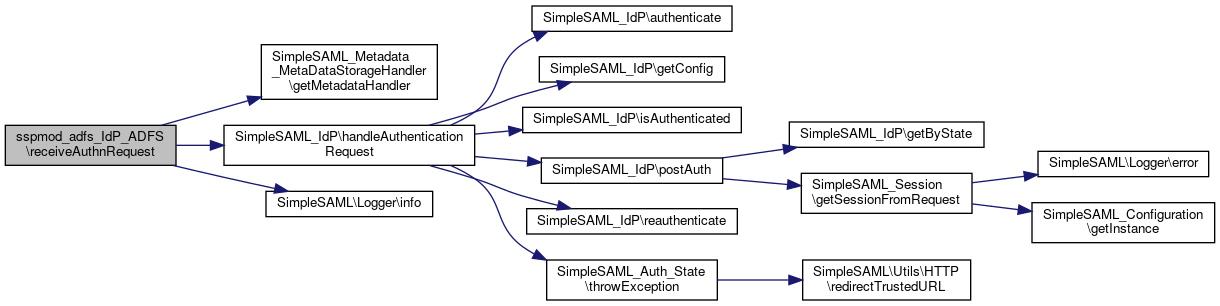
Here is the caller graph for this function:◆ receiveAuthnRequest()
|
static |
Definition at line 5 of file ADFS.php.
References $_SERVER, $idp, $issuer, $metadata, $query, $spMetadata, $state, SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), and SimpleSAML\Logger\info().
 Here is the call graph for this function:
Here is the call graph for this function:◆ receiveLogoutMessage()
|
static |
Definition at line 189 of file ADFS.php.
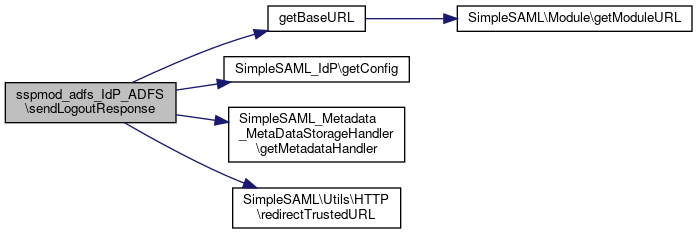
◆ sendLogoutResponse()
|
static |
Definition at line 181 of file ADFS.php.
References $idp, $idpMetadata, $metadata, getBaseURL(), SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), and SimpleSAML\Utils\HTTP\redirectTrustedURL().
 Here is the call graph for this function:
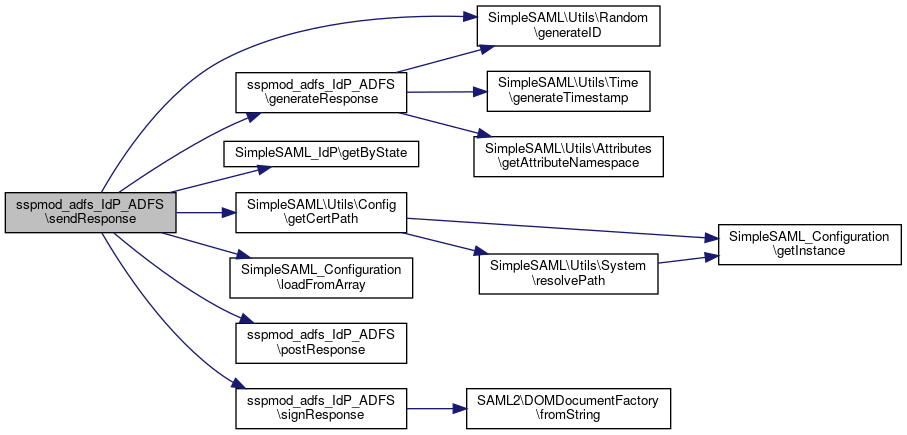
Here is the call graph for this function:◆ sendResponse()
|
static |
Definition at line 142 of file ADFS.php.
References $attributes, $idp, $idpEntityId, $idpMetadata, $nameid, $response, $spEntityId, $spMetadata, $state, SimpleSAML\Utils\Random\generateID(), generateResponse(), SimpleSAML_IdP\getByState(), SimpleSAML\Utils\Config\getCertPath(), SimpleSAML_Configuration\loadFromArray(), postResponse(), and signResponse().
 Here is the call graph for this function:
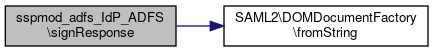
Here is the call graph for this function:◆ signResponse()
|
staticprivate |
Definition at line 96 of file ADFS.php.
References $key, $response, and SAML2\DOMDocumentFactory\fromString().
Referenced by sendResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/modules/adfs/lib/IdP/ADFS.php