Collaboration diagram for SimpleSAML\XML\Shib13\AuthnResponse:
Collaboration diagram for SimpleSAML\XML\Shib13\AuthnResponse:Public Member Functions | |
| setMessageValidated ($messageValidated) | |
| Set whether this message was validated externally. More... | |
| setXML ($xml) | |
| setRelayState ($relayState) | |
| getRelayState () | |
| validate () | |
| getSessionIndex () | |
| Retrieve the session index of this response. More... | |
| getIssuer () | |
| getNameID () | |
| generate (\SimpleSAML_Configuration $idp, \SimpleSAML_Configuration $sp, $shire, $attributes) | |
| Build a authentication response. More... | |
Data Fields | |
| const | SHIB_PROTOCOL_NS = 'urn:oasis:names:tc:SAML:1.0:protocol' |
| const | SHIB_ASSERT_NS = 'urn:oasis:names:tc:SAML:1.0:assertion' |
Static Protected Member Functions | |
| static | checkDateConditions ($start=null, $end=null) |
| Check if we are currently between the given date & time conditions. More... | |
Private Member Functions | |
| isNodeValidated ($node) | |
| Checks if the given node is validated by the signature on this response. More... | |
| doXPathQuery ($query, $node=null) | |
| This function runs an xPath query on this authentication response. More... | |
| enc_attribute ($name, $values, $base64, $scopedAttributes) | |
| Format a shib13 attribute. More... | |
Private Attributes | |
| $validator = null | |
| $messageValidated = false | |
| $dom | |
| $relayState = null | |
Detailed Description
Definition at line 21 of file AuthnResponse.php.
Member Function Documentation
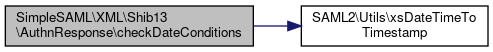
◆ checkDateConditions()
|
staticprotected |
Check if we are currently between the given date & time conditions.
Note that this function allows a 10-minute leap from the initial time as marked by $start.
- Parameters
-
string | null $start A SAML2 timestamp marking the start of the period to check. Defaults to null, in which case there's no limitations in the past. string | null $end A SAML2 timestamp marking the end of the period to check. Defaults to null, in which case there's no limitations in the future.
- Returns
- bool True if the current time belongs to the period specified by $start and $end. False otherwise.
- See also
- \SAML2\Utils::xsDateTimeToTimestamp.
Definition at line 461 of file AuthnResponse.php.
References $end, $start, and SAML2\Utils\xsDateTimeToTimestamp().
 Here is the call graph for this function:
Here is the call graph for this function:◆ doXPathQuery()
|
private |
This function runs an xPath query on this authentication response.
- Parameters
-
string $query The query which should be run. \DOMNode $node The node which this query is relative to. If this node is NULL (the default) then the query will be relative to the root of the response.
- Returns
- \DOMNodeList
Definition at line 166 of file AuthnResponse.php.
References $query.
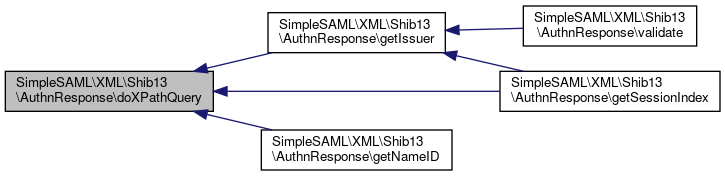
Referenced by SimpleSAML\XML\Shib13\AuthnResponse\getIssuer(), SimpleSAML\XML\Shib13\AuthnResponse\getNameID(), and SimpleSAML\XML\Shib13\AuthnResponse\getSessionIndex().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ enc_attribute()
|
private |
Format a shib13 attribute.
- Parameters
-
string $name Name of the attribute. array $values Values of the attribute (as an array of strings). bool $base64 Whether the attriubte values should be base64-encoded. array $scopedAttributes Array of attributes names which are scoped.
- Returns
- string The attribute encoded as an XML-string.
Definition at line 409 of file AuthnResponse.php.
References $name, and $values.
Referenced by SimpleSAML\XML\Shib13\AuthnResponse\generate().
 Here is the caller graph for this function:
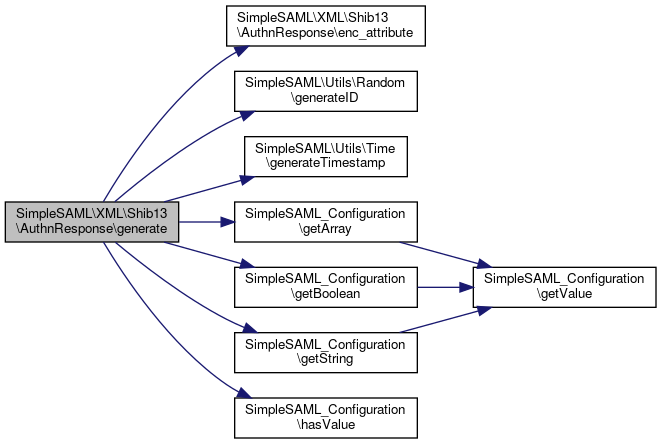
Here is the caller graph for this function:◆ generate()
| SimpleSAML\XML\Shib13\AuthnResponse::generate | ( | \SimpleSAML_Configuration | $idp, |
| \SimpleSAML_Configuration | $sp, | ||
| $shire, | |||
| $attributes | |||
| ) |
Build a authentication response.
- Parameters
-
\SimpleSAML_Configuration $idp Metadata for the IdP the response is sent from. \SimpleSAML_Configuration $sp Metadata for the SP the response is sent to. string $shire The endpoint on the SP the response is sent to. array | null $attributes The attributes which should be included in the response.
- Returns
- string The response.
Definition at line 309 of file AuthnResponse.php.
References $attributes, $id, $idp, $name, $nameid, $response, $spEntityId, SimpleSAML\XML\Shib13\AuthnResponse\enc_attribute(), SimpleSAML\Utils\Random\generateID(), SimpleSAML\Utils\Time\generateTimestamp(), SimpleSAML_Configuration\getArray(), SimpleSAML_Configuration\getBoolean(), SimpleSAML_Configuration\getString(), and SimpleSAML_Configuration\hasValue().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getIssuer()
| SimpleSAML\XML\Shib13\AuthnResponse::getIssuer | ( | ) |
Definition at line 272 of file AuthnResponse.php.
References $query, and SimpleSAML\XML\Shib13\AuthnResponse\doXPathQuery().
Referenced by SimpleSAML\XML\Shib13\AuthnResponse\validate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getNameID()
| SimpleSAML\XML\Shib13\AuthnResponse::getNameID | ( | ) |
Definition at line 284 of file AuthnResponse.php.
References $query, and SimpleSAML\XML\Shib13\AuthnResponse\doXPathQuery().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getRelayState()
| SimpleSAML\XML\Shib13\AuthnResponse::getRelayState | ( | ) |
Definition at line 80 of file AuthnResponse.php.
References SimpleSAML\XML\Shib13\AuthnResponse\$relayState.
◆ getSessionIndex()
| SimpleSAML\XML\Shib13\AuthnResponse::getSessionIndex | ( | ) |
Retrieve the session index of this response.
- Returns
- string|null The session index of this response.
Definition at line 189 of file AuthnResponse.php.
References $query, and SimpleSAML\XML\Shib13\AuthnResponse\doXPathQuery().
 Here is the call graph for this function:
Here is the call graph for this function:◆ isNodeValidated()
|
private |
Checks if the given node is validated by the signature on this response.
- Parameters
-
\DOMElement $node Node to be validated.
- Returns
- bool TRUE if the node is validated or FALSE if not.
Definition at line 136 of file AuthnResponse.php.
◆ setMessageValidated()
| SimpleSAML\XML\Shib13\AuthnResponse::setMessageValidated | ( | $messageValidated | ) |
Set whether this message was validated externally.
- Parameters
-
bool $messageValidated TRUE if the message is already validated, FALSE if not.
Definition at line 56 of file AuthnResponse.php.
References SimpleSAML\XML\Shib13\AuthnResponse\$messageValidated.
◆ setRelayState()
| SimpleSAML\XML\Shib13\AuthnResponse::setRelayState | ( | $relayState | ) |
Definition at line 75 of file AuthnResponse.php.
References SimpleSAML\XML\Shib13\AuthnResponse\$relayState.
◆ setXML()
| SimpleSAML\XML\Shib13\AuthnResponse::setXML | ( | $xml | ) |
Definition at line 64 of file AuthnResponse.php.
References $xml, and SAML2\DOMDocumentFactory\fromString().
 Here is the call graph for this function:
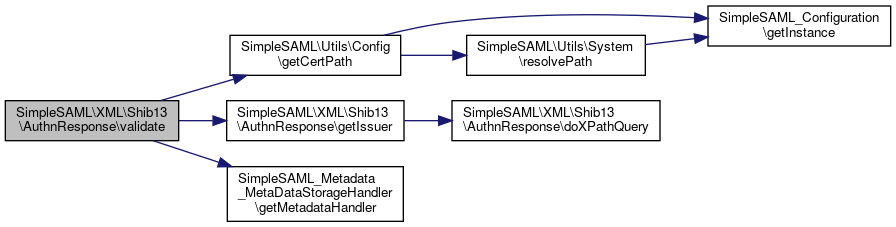
Here is the call graph for this function:◆ validate()
| SimpleSAML\XML\Shib13\AuthnResponse::validate | ( | ) |
Definition at line 85 of file AuthnResponse.php.
References $issuer, $key, $metadata, SimpleSAML\Utils\Config\getCertPath(), SimpleSAML\XML\Shib13\AuthnResponse\getIssuer(), and SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler().
 Here is the call graph for this function:
Here is the call graph for this function:Field Documentation
◆ $dom
|
private |
Definition at line 43 of file AuthnResponse.php.
◆ $messageValidated
|
private |
Definition at line 33 of file AuthnResponse.php.
Referenced by SimpleSAML\XML\Shib13\AuthnResponse\setMessageValidated().
◆ $relayState
|
private |
Definition at line 48 of file AuthnResponse.php.
Referenced by SimpleSAML\XML\Shib13\AuthnResponse\getRelayState(), and SimpleSAML\XML\Shib13\AuthnResponse\setRelayState().
◆ $validator
|
private |
Definition at line 27 of file AuthnResponse.php.
◆ SHIB_ASSERT_NS
| const SimpleSAML\XML\Shib13\AuthnResponse::SHIB_ASSERT_NS = 'urn:oasis:names:tc:SAML:1.0:assertion' |
Definition at line 37 of file AuthnResponse.php.
◆ SHIB_PROTOCOL_NS
| const SimpleSAML\XML\Shib13\AuthnResponse::SHIB_PROTOCOL_NS = 'urn:oasis:names:tc:SAML:1.0:protocol' |
Definition at line 36 of file AuthnResponse.php.
The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/lib/SimpleSAML/XML/Shib13/AuthnResponse.php