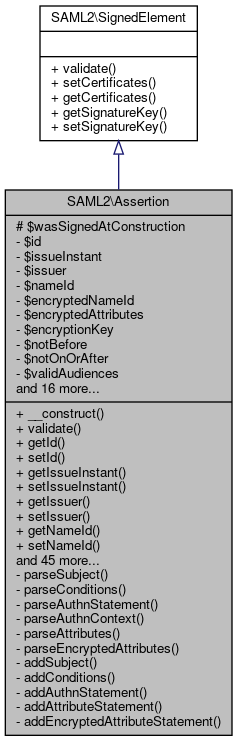
Inheritance diagram for SAML2\Assertion:
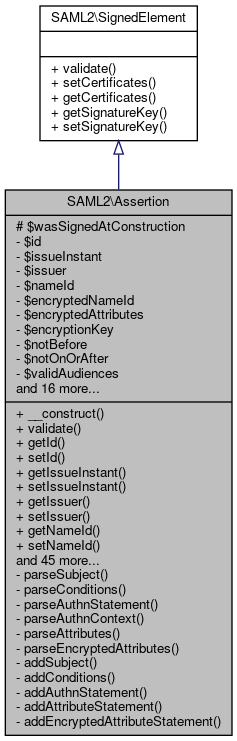
Inheritance diagram for SAML2\Assertion: Collaboration diagram for SAML2\Assertion:
Collaboration diagram for SAML2\Assertion:Public Member Functions | |
| __construct (\DOMElement $xml=null) | |
| Constructor for SAML 2 assertions. More... | |
| validate (XMLSecurityKey $key) | |
| Validate this assertion against a public key. More... | |
| getId () | |
| Retrieve the identifier of this assertion. More... | |
| setId ($id) | |
| Set the identifier of this assertion. More... | |
| getIssueInstant () | |
| Retrieve the issue timestamp of this assertion. More... | |
| setIssueInstant ($issueInstant) | |
| Set the issue timestamp of this assertion. More... | |
| getIssuer () | |
| Retrieve the issuer if this assertion. More... | |
| setIssuer ($issuer) | |
| Set the issuer of this message. More... | |
| getNameId () | |
| Retrieve the NameId of the subject in the assertion. More... | |
| setNameId ($nameId) | |
| Set the NameId of the subject in the assertion. More... | |
| isNameIdEncrypted () | |
| Check whether the NameId is encrypted. More... | |
| encryptNameId (XMLSecurityKey $key) | |
| Encrypt the NameID in the Assertion. More... | |
| decryptNameId (XMLSecurityKey $key, array $blacklist=array()) | |
| Decrypt the NameId of the subject in the assertion. More... | |
| hasEncryptedAttributes () | |
| Did this Assertion contain encrypted Attributes? More... | |
| decryptAttributes (XMLSecurityKey $key, array $blacklist=array()) | |
| Decrypt the assertion attributes. More... | |
| getNotBefore () | |
| Retrieve the earliest timestamp this assertion is valid. More... | |
| setNotBefore ($notBefore) | |
| Set the earliest timestamp this assertion can be used. More... | |
| getNotOnOrAfter () | |
| Retrieve the expiration timestamp of this assertion. More... | |
| setNotOnOrAfter ($notOnOrAfter) | |
| Set the expiration timestamp of this assertion. More... | |
| setEncryptedAttributes ($ea) | |
| Set $EncryptedAttributes if attributes will send encrypted. More... | |
| getValidAudiences () | |
| Retrieve the audiences that are allowed to receive this assertion. More... | |
| setValidAudiences (array $validAudiences=null) | |
| Set the audiences that are allowed to receive this assertion. More... | |
| getAuthnInstant () | |
| Retrieve the AuthnInstant of the assertion. More... | |
| setAuthnInstant ($authnInstant) | |
| Set the AuthnInstant of the assertion. More... | |
| getSessionNotOnOrAfter () | |
| Retrieve the session expiration timestamp. More... | |
| setSessionNotOnOrAfter ($sessionNotOnOrAfter) | |
| Set the session expiration timestamp. More... | |
| getSessionIndex () | |
| Retrieve the session index of the user at the IdP. More... | |
| setSessionIndex ($sessionIndex) | |
| Set the session index of the user at the IdP. More... | |
| getAuthnContext () | |
| Retrieve the authentication method used to authenticate the user. More... | |
| setAuthnContext ($authnContext) | |
| Set the authentication method used to authenticate the user. More... | |
| getAuthnContextClassRef () | |
| Retrieve the authentication method used to authenticate the user. More... | |
| setAuthnContextClassRef ($authnContextClassRef) | |
| Set the authentication method used to authenticate the user. More... | |
| setAuthnContextDecl (Chunk $authnContextDecl) | |
| Set the authentication context declaration. More... | |
| getAuthnContextDecl () | |
| Get the authentication context declaration. More... | |
| setAuthnContextDeclRef ($authnContextDeclRef) | |
| Set the authentication context declaration reference. More... | |
| getAuthnContextDeclRef () | |
| Get the authentication context declaration reference. More... | |
| getAuthenticatingAuthority () | |
| Retrieve the AuthenticatingAuthority. More... | |
| setAuthenticatingAuthority ($authenticatingAuthority) | |
| Set the AuthenticatingAuthority. More... | |
| getAttributes () | |
| Retrieve all attributes. More... | |
| setAttributes (array $attributes) | |
| Replace all attributes. More... | |
| getAttributesValueTypes () | |
| Retrieve all attributes value types. More... | |
| setAttributesValueTypes (array $attributesValueTypes) | |
| Replace all attributes value types. More... | |
| getAttributeNameFormat () | |
| Retrieve the NameFormat used on all attributes. More... | |
| setAttributeNameFormat ($nameFormat) | |
| Set the NameFormat used on all attributes. More... | |
| getSubjectConfirmation () | |
| Retrieve the SubjectConfirmation elements we have in our Subject element. More... | |
| setSubjectConfirmation (array $SubjectConfirmation) | |
| Set the SubjectConfirmation elements that should be included in the assertion. More... | |
| getSignatureKey () | |
| Retrieve the private key we should use to sign the assertion. More... | |
| setSignatureKey (XMLSecurityKey $signatureKey=null) | |
| Set the private key we should use to sign the assertion. More... | |
| getEncryptionKey () | |
| Return the key we should use to encrypt the assertion. More... | |
| setEncryptionKey (XMLSecurityKey $Key=null) | |
| Set the private key we should use to encrypt the attributes. More... | |
| setCertificates (array $certificates) | |
| Set the certificates that should be included in the assertion. More... | |
| getCertificates () | |
| Retrieve the certificates that are included in the assertion. More... | |
| getWasSignedAtConstruction () | |
| getSignatureMethod () | |
| toXML (\DOMNode $parentElement=null) | |
| Convert this assertion to an XML element. More... | |
| validate (XMLSecurityKey $key) | |
| Validate this element against a public key. More... | |
| setCertificates (array $certificates) | |
| Set the certificates that should be included in the element. More... | |
| getCertificates () | |
| Retrieve the certificates that are included in the element (if any). More... | |
| getSignatureKey () | |
| Retrieve the private key we should use to sign the element. More... | |
| setSignatureKey (XMLSecurityKey $signatureKey=null) | |
| Set the private key we should use to sign the element. More... | |
Protected Attributes | |
| $wasSignedAtConstruction = false | |
Private Member Functions | |
| parseSubject (\DOMElement $xml) | |
| Parse subject in assertion. More... | |
| parseConditions (\DOMElement $xml) | |
| Parse conditions in assertion. More... | |
| parseAuthnStatement (\DOMElement $xml) | |
| Parse AuthnStatement in assertion. More... | |
| parseAuthnContext (\DOMElement $authnStatementEl) | |
| Parse AuthnContext in AuthnStatement. More... | |
| parseAttributes (\DOMElement $xml) | |
| Parse attribute statements in assertion. More... | |
| parseEncryptedAttributes (\DOMElement $xml) | |
| Parse encrypted attribute statements in assertion. More... | |
| addSubject (\DOMElement $root) | |
| Add a Subject-node to the assertion. More... | |
| addConditions (\DOMElement $root) | |
| Add a Conditions-node to the assertion. More... | |
| addAuthnStatement (\DOMElement $root) | |
| Add a AuthnStatement-node to the assertion. More... | |
| addAttributeStatement (\DOMElement $root) | |
| Add an AttributeStatement-node to the assertion. More... | |
| addEncryptedAttributeStatement (\DOMElement $root) | |
| Add an EncryptedAttribute Statement-node to the assertion. More... | |
Detailed Description
Definition at line 17 of file Assertion.php.
Constructor & Destructor Documentation
◆ __construct()
| SAML2\Assertion::__construct | ( | \DOMElement | $xml = null | ) |
Constructor for SAML 2 assertions.
- Parameters
-
\DOMElement | null $xml The input assertion.
- Exceptions
-
Definition at line 257 of file Assertion.php.
References $issuer, $xml, and getTime().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ addAttributeStatement()
|
private |
Add an AttributeStatement-node to the assertion.
- Parameters
-
\DOMElement $root The assertion element we should add the subject to.
Definition at line 1537 of file Assertion.php.
◆ addAuthnStatement()
|
private |
Add a AuthnStatement-node to the assertion.
- Parameters
-
\DOMElement $root The assertion element we should add the authentication statement to.
Definition at line 1471 of file Assertion.php.
References $root.
◆ addConditions()
|
private |
Add a Conditions-node to the assertion.
- Parameters
-
\DOMElement $root The assertion element we should add the conditions to.
Definition at line 1443 of file Assertion.php.
References $root.
◆ addEncryptedAttributeStatement()
|
private |
Add an EncryptedAttribute Statement-node to the assertion.
- Parameters
-
\DOMElement $root The assertion element we should add the Encrypted Attribute Statement to.
Definition at line 1638 of file Assertion.php.
◆ addSubject()
|
private |
Add a Subject-node to the assertion.
- Parameters
-
\DOMElement $root The assertion element we should add the subject to.
Definition at line 1413 of file Assertion.php.
◆ decryptAttributes()
| SAML2\Assertion::decryptAttributes | ( | XMLSecurityKey | $key, |
| array | $blacklist = array() |
||
| ) |
Decrypt the assertion attributes.
- Parameters
-
XMLSecurityKey $key array $blacklist
- Exceptions
-
Definition at line 835 of file Assertion.php.
References $attributes, $key, and $name.
◆ decryptNameId()
| SAML2\Assertion::decryptNameId | ( | XMLSecurityKey | $key, |
| array | $blacklist = array() |
||
| ) |
Decrypt the NameId of the subject in the assertion.
- Parameters
-
XMLSecurityKey $key The decryption key. array $blacklist Blacklisted decryption algorithms.
Definition at line 803 of file Assertion.php.
Referenced by SAML2\Assertion\Transformer\NameIdDecryptionTransformer\transform().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ encryptNameId()
| SAML2\Assertion::encryptNameId | ( | XMLSecurityKey | $key | ) |
Encrypt the NameID in the Assertion.
- Parameters
-
XMLSecurityKey $key The encryption key.
Definition at line 771 of file Assertion.php.
◆ getAttributeNameFormat()
| SAML2\Assertion::getAttributeNameFormat | ( | ) |
Retrieve the NameFormat used on all attributes.
If more than one NameFormat is used in the received attributes, this returns the unspecified NameFormat.
- Returns
- string The NameFormat used on all attributes.
Definition at line 1238 of file Assertion.php.
◆ getAttributes()
| SAML2\Assertion::getAttributes | ( | ) |
Retrieve all attributes.
- Returns
- array All attributes, as an associative array.
Definition at line 1195 of file Assertion.php.
References $attributes.
Referenced by SAML2\Assertion\Transformer\DecodeBase64Transformer\transform().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getAttributesValueTypes()
| SAML2\Assertion::getAttributesValueTypes | ( | ) |
Retrieve all attributes value types.
- Returns
- array All attributes value types, as an associative array.
Definition at line 1215 of file Assertion.php.
◆ getAuthenticatingAuthority()
| SAML2\Assertion::getAuthenticatingAuthority | ( | ) |
Retrieve the AuthenticatingAuthority.
- Returns
- array
Definition at line 1174 of file Assertion.php.
◆ getAuthnContext()
| SAML2\Assertion::getAuthnContext | ( | ) |
Retrieve the authentication method used to authenticate the user.
This will return null if no authentication statement was included in the assertion.
Note that this returns either the AuthnContextClassRef or the AuthnConextDeclRef, whose definition overlaps but is slightly different (consult the specification for more information). This was done to work around an old bug of Shibboleth ( https://bugs.internet2.edu/jira/browse/SIDP-187 ). Should no longer be required, please use either getAuthnConextClassRef or getAuthnContextDeclRef.
- Deprecated:
- use getAuthnContextClassRef
- Returns
- string|null The authentication method.
Definition at line 1055 of file Assertion.php.
◆ getAuthnContextClassRef()
| SAML2\Assertion::getAuthnContextClassRef | ( | ) |
Retrieve the authentication method used to authenticate the user.
This will return null if no authentication statement was included in the assertion.
- Returns
- string|null The authentication method.
Definition at line 1088 of file Assertion.php.
◆ getAuthnContextDecl()
| SAML2\Assertion::getAuthnContextDecl | ( | ) |
Get the authentication context declaration.
See: @url http://docs.oasis-open.org/security/saml/v2.0/saml-authn-context-2.0-os.pdf
- Returns
- \SAML2\XML\Chunk|null
Definition at line 1133 of file Assertion.php.
◆ getAuthnContextDeclRef()
| SAML2\Assertion::getAuthnContextDeclRef | ( | ) |
Get the authentication context declaration reference.
URI reference that identifies an authentication context declaration.
The URI reference MAY directly resolve into an XML document containing the referenced declaration.
- Returns
- string
Definition at line 1163 of file Assertion.php.
◆ getAuthnInstant()
| SAML2\Assertion::getAuthnInstant | ( | ) |
Retrieve the AuthnInstant of the assertion.
- Returns
- int|null The timestamp the user was authenticated, or NULL if the user isn't authenticated.
Definition at line 971 of file Assertion.php.
◆ getCertificates()
| SAML2\Assertion::getCertificates | ( | ) |
Retrieve the certificates that are included in the assertion.
- Returns
- array An array of certificates.
Implements SAML2\SignedElement.
Definition at line 1335 of file Assertion.php.
References $certificates.
◆ getEncryptionKey()
| SAML2\Assertion::getEncryptionKey | ( | ) |
Return the key we should use to encrypt the assertion.
- Returns
- XMLSecurityKey|null The key, or NULL if no key is specified..
Definition at line 1303 of file Assertion.php.
◆ getId()
| SAML2\Assertion::getId | ( | ) |
Retrieve the identifier of this assertion.
- Returns
- string The identifier of this assertion.
Definition at line 661 of file Assertion.php.
References $id.
◆ getIssueInstant()
| SAML2\Assertion::getIssueInstant | ( | ) |
Retrieve the issue timestamp of this assertion.
- Returns
- int The issue timestamp of this assertion, as an UNIX timestamp.
Definition at line 683 of file Assertion.php.
◆ getIssuer()
| SAML2\Assertion::getIssuer | ( | ) |
Retrieve the issuer if this assertion.
- Returns
- string|\SAML2\XML\saml\Issuer The issuer of this assertion.
Definition at line 705 of file Assertion.php.
References $issuer.
◆ getNameId()
| SAML2\Assertion::getNameId | ( | ) |
Retrieve the NameId of the subject in the assertion.
- Returns
- \SAML2\XML\saml\NameID|null The name identifier of the assertion.
- Exceptions
-
Definition at line 728 of file Assertion.php.
References $nameId.
◆ getNotBefore()
| SAML2\Assertion::getNotBefore | ( | ) |
Retrieve the earliest timestamp this assertion is valid.
This function returns null if there are no restrictions on how early the assertion can be used.
- Returns
- int|null The earliest timestamp this assertion is valid.
Definition at line 886 of file Assertion.php.
Referenced by SAML2\Assertion\Validation\ConstraintValidator\NotBefore\validate().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getNotOnOrAfter()
| SAML2\Assertion::getNotOnOrAfter | ( | ) |
Retrieve the expiration timestamp of this assertion.
This function returns null if there are no restrictions on how late the assertion can be used.
- Returns
- int|null The latest timestamp this assertion is valid.
Definition at line 913 of file Assertion.php.
Referenced by SAML2\Assertion\Validation\ConstraintValidator\NotOnOrAfter\validate().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getSessionIndex()
| SAML2\Assertion::getSessionIndex | ( | ) |
Retrieve the session index of the user at the IdP.
- Returns
- string|null The session index of the user at the IdP.
Definition at line 1021 of file Assertion.php.
References $sessionIndex.
◆ getSessionNotOnOrAfter()
| SAML2\Assertion::getSessionNotOnOrAfter | ( | ) |
Retrieve the session expiration timestamp.
This function returns null if there are no restrictions on the session lifetime.
- Returns
- int|null The latest timestamp this session is valid.
Definition at line 997 of file Assertion.php.
Referenced by SAML2\Assertion\Validation\ConstraintValidator\SessionNotOnOrAfter\validate().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getSignatureKey()
| SAML2\Assertion::getSignatureKey | ( | ) |
Retrieve the private key we should use to sign the assertion.
- Returns
- XMLSecurityKey|null The key, or NULL if no key is specified.
Implements SAML2\SignedElement.
Definition at line 1280 of file Assertion.php.
◆ getSignatureMethod()
| SAML2\Assertion::getSignatureMethod | ( | ) |
◆ getSubjectConfirmation()
| SAML2\Assertion::getSubjectConfirmation | ( | ) |
Retrieve the SubjectConfirmation elements we have in our Subject element.
- Returns
- array Array of \SAML2\XML\saml\SubjectConfirmation elements.
Definition at line 1260 of file Assertion.php.
Referenced by SAML2\Assertion\Processor\validateAssertion().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getValidAudiences()
| SAML2\Assertion::getValidAudiences | ( | ) |
Retrieve the audiences that are allowed to receive this assertion.
This may be null, in which case all audiences are allowed.
- Returns
- array|null The allowed audiences.
Definition at line 949 of file Assertion.php.
Referenced by SAML2\Assertion\Validation\ConstraintValidator\SpIsValidAudience\validate().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getWasSignedAtConstruction()
| SAML2\Assertion::getWasSignedAtConstruction | ( | ) |
◆ hasEncryptedAttributes()
| SAML2\Assertion::hasEncryptedAttributes | ( | ) |
Did this Assertion contain encrypted Attributes?
- Returns
- bool
Definition at line 823 of file Assertion.php.
◆ isNameIdEncrypted()
| SAML2\Assertion::isNameIdEncrypted | ( | ) |
Check whether the NameId is encrypted.
- Returns
- true if the NameId is encrypted, false if not.
Definition at line 761 of file Assertion.php.
Referenced by SAML2\Assertion\Transformer\NameIdDecryptionTransformer\transform().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ parseAttributes()
|
private |
Parse attribute statements in assertion.
- Parameters
-
\DOMElement $xml The XML element with the assertion.
- Exceptions
-
Definition at line 510 of file Assertion.php.
References $attributes, $name, and $xml.
◆ parseAuthnContext()
|
private |
Parse AuthnContext in AuthnStatement.
- Parameters
-
\DOMElement $authnStatementEl
- Exceptions
-
Definition at line 451 of file Assertion.php.
◆ parseAuthnStatement()
|
private |
Parse AuthnStatement in assertion.
- Parameters
-
\DOMElement $xml The assertion XML element.
- Exceptions
-
Definition at line 417 of file Assertion.php.
References $xml.
◆ parseConditions()
|
private |
Parse conditions in assertion.
- Parameters
-
\DOMElement $xml The assertion XML element.
- Exceptions
-
Definition at line 353 of file Assertion.php.
References $xml.
◆ parseEncryptedAttributes()
|
private |
Parse encrypted attribute statements in assertion.
- Parameters
-
\DOMElement $xml The XML element with the assertion.
Definition at line 605 of file Assertion.php.
References $xml.
◆ parseSubject()
|
private |
Parse subject in assertion.
- Parameters
-
\DOMElement $xml The assertion XML element.
- Exceptions
-
Definition at line 309 of file Assertion.php.
◆ setAttributeNameFormat()
| SAML2\Assertion::setAttributeNameFormat | ( | $nameFormat | ) |
Set the NameFormat used on all attributes.
- Parameters
-
string $nameFormat The NameFormat used on all attributes.
Definition at line 1248 of file Assertion.php.
◆ setAttributes()
| SAML2\Assertion::setAttributes | ( | array | $attributes | ) |
Replace all attributes.
- Parameters
-
array $attributes All new attributes, as an associative array.
Definition at line 1205 of file Assertion.php.
References $attributes.
Referenced by SAML2\Assertion\Transformer\DecodeBase64Transformer\transform().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ setAttributesValueTypes()
| SAML2\Assertion::setAttributesValueTypes | ( | array | $attributesValueTypes | ) |
Replace all attributes value types.
- Parameters
-
array $attributesValueTypes All new attribute value types, as an associative array.
Definition at line 1225 of file Assertion.php.
◆ setAuthenticatingAuthority()
| SAML2\Assertion::setAuthenticatingAuthority | ( | $authenticatingAuthority | ) |
Set the AuthenticatingAuthority.
- Parameters
-
array.
Definition at line 1185 of file Assertion.php.
References $authenticatingAuthority.
◆ setAuthnContext()
| SAML2\Assertion::setAuthnContext | ( | $authnContext | ) |
Set the authentication method used to authenticate the user.
If this is set to null, no authentication statement will be included in the assertion. The default is null.
- Deprecated:
- use setAuthnContextClassRef
- Parameters
-
string | null $authnContext The authentication method.
Definition at line 1075 of file Assertion.php.
◆ setAuthnContextClassRef()
| SAML2\Assertion::setAuthnContextClassRef | ( | $authnContextClassRef | ) |
Set the authentication method used to authenticate the user.
If this is set to null, no authentication statement will be included in the assertion. The default is null.
- Parameters
-
string | null $authnContextClassRef The authentication method.
Definition at line 1101 of file Assertion.php.
◆ setAuthnContextDecl()
| SAML2\Assertion::setAuthnContextDecl | ( | Chunk | $authnContextDecl | ) |
Set the authentication context declaration.
- Parameters
-
\SAML2\XML\Chunk $authnContextDecl
- Exceptions
-
Definition at line 1114 of file Assertion.php.
◆ setAuthnContextDeclRef()
| SAML2\Assertion::setAuthnContextDeclRef | ( | $authnContextDeclRef | ) |
Set the authentication context declaration reference.
- Parameters
-
string $authnContextDeclRef
- Exceptions
-
Definition at line 1144 of file Assertion.php.
◆ setAuthnInstant()
| SAML2\Assertion::setAuthnInstant | ( | $authnInstant | ) |
Set the AuthnInstant of the assertion.
- Parameters
-
int | null $authnInstant Timestamp the user was authenticated, or NULL if we don't want an AuthnStatement.
Definition at line 982 of file Assertion.php.
◆ setCertificates()
| SAML2\Assertion::setCertificates | ( | array | $certificates | ) |
Set the certificates that should be included in the assertion.
The certificates should be strings with the PEM encoded data.
- Parameters
-
array $certificates An array of certificates.
Implements SAML2\SignedElement.
Definition at line 1325 of file Assertion.php.
References $certificates.
◆ setEncryptedAttributes()
| SAML2\Assertion::setEncryptedAttributes | ( | $ea | ) |
Set $EncryptedAttributes if attributes will send encrypted.
- Parameters
-
boolean $ea true to encrypt attributes in the assertion.
Definition at line 937 of file Assertion.php.
◆ setEncryptionKey()
| SAML2\Assertion::setEncryptionKey | ( | XMLSecurityKey | $Key = null | ) |
Set the private key we should use to encrypt the attributes.
- Parameters
-
XMLSecurityKey | null $Key
Definition at line 1313 of file Assertion.php.
◆ setId()
| SAML2\Assertion::setId | ( | $id | ) |
Set the identifier of this assertion.
- Parameters
-
string $id The new identifier of this assertion.
Definition at line 671 of file Assertion.php.
References $id.
◆ setIssueInstant()
| SAML2\Assertion::setIssueInstant | ( | $issueInstant | ) |
Set the issue timestamp of this assertion.
- Parameters
-
int $issueInstant The new issue timestamp of this assertion, as an UNIX timestamp.
Definition at line 693 of file Assertion.php.
◆ setIssuer()
| SAML2\Assertion::setIssuer | ( | $issuer | ) |
◆ setNameId()
| SAML2\Assertion::setNameId | ( | $nameId | ) |
Set the NameId of the subject in the assertion.
The NameId must be a \SAML2\XML\saml\NameID object or an array in the format accepted by \SAML2\Utils::addNameId() (an array, deprecated).
- See also
- \SAML2\Utils::addNameId()
- Parameters
-
\SAML2\XML\saml\NameID | array | null $nameId The name identifier of the assertion.
Definition at line 746 of file Assertion.php.
References $nameId.
◆ setNotBefore()
| SAML2\Assertion::setNotBefore | ( | $notBefore | ) |
Set the earliest timestamp this assertion can be used.
Set this to null if no limit is required.
- Parameters
-
int | null $notBefore The earliest timestamp this assertion is valid.
Definition at line 898 of file Assertion.php.
◆ setNotOnOrAfter()
| SAML2\Assertion::setNotOnOrAfter | ( | $notOnOrAfter | ) |
Set the expiration timestamp of this assertion.
Set this to null if no limit is required.
- Parameters
-
int | null $notOnOrAfter The latest timestamp this assertion is valid.
Definition at line 925 of file Assertion.php.
◆ setSessionIndex()
| SAML2\Assertion::setSessionIndex | ( | $sessionIndex | ) |
Set the session index of the user at the IdP.
Note that the authentication context must be set before the session index can be inluded in the assertion.
- Parameters
-
string | null $sessionIndex The session index of the user at the IdP.
Definition at line 1034 of file Assertion.php.
References $sessionIndex.
◆ setSessionNotOnOrAfter()
| SAML2\Assertion::setSessionNotOnOrAfter | ( | $sessionNotOnOrAfter | ) |
Set the session expiration timestamp.
Set this to null if no limit is required.
- Parameters
-
int | null $sessionNotOnOrAfter The latest timestamp this session is valid.
Definition at line 1009 of file Assertion.php.
◆ setSignatureKey()
| SAML2\Assertion::setSignatureKey | ( | XMLSecurityKey | $signatureKey = null | ) |
Set the private key we should use to sign the assertion.
If the key is null, the assertion will be sent unsigned.
- Parameters
-
XMLSecurityKey | null $signatureKey
Implements SAML2\SignedElement.
Definition at line 1292 of file Assertion.php.
◆ setSubjectConfirmation()
| SAML2\Assertion::setSubjectConfirmation | ( | array | $SubjectConfirmation | ) |
Set the SubjectConfirmation elements that should be included in the assertion.
- Parameters
-
array $SubjectConfirmation Array of \SAML2\XML\saml\SubjectConfirmation elements.
Definition at line 1270 of file Assertion.php.
◆ setValidAudiences()
| SAML2\Assertion::setValidAudiences | ( | array | $validAudiences = null | ) |
Set the audiences that are allowed to receive this assertion.
This may be null, in which case all audiences are allowed.
- Parameters
-
array | null $validAudiences The allowed audiences.
Definition at line 961 of file Assertion.php.
◆ toXML()
| SAML2\Assertion::toXML | ( | \DOMNode | $parentElement = null | ) |
Convert this assertion to an XML element.
- Parameters
-
\DOMNode | null $parentElement The DOM node the assertion should be created in.
- Returns
- \DOMElement This assertion.
Definition at line 1362 of file Assertion.php.
References $issuer, and $root.
Referenced by SAML2\EncryptedAssertion\setAssertion().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ validate()
| SAML2\Assertion::validate | ( | XMLSecurityKey | $key | ) |
Validate this assertion against a public key.
If no signature was present on the assertion, we will return false. Otherwise, true will be returned. An exception is thrown if the signature validation fails.
- Parameters
-
XMLSecurityKey $key The key we should check against.
- Returns
- boolean true if successful, false if it is unsigned.
Implements SAML2\SignedElement.
Definition at line 643 of file Assertion.php.
References $key.
Field Documentation
◆ $attributes
|
private |
Definition at line 174 of file Assertion.php.
Referenced by SAML2\Assertion\Transformer\DecodeBase64Transformer\transform().
◆ $attributesValueTypes
|
private |
Definition at line 191 of file Assertion.php.
◆ $AuthenticatingAuthority
|
private |
Definition at line 156 of file Assertion.php.
◆ $authnContextClassRef
|
private |
Definition at line 130 of file Assertion.php.
◆ $authnContextDecl
|
private |
Definition at line 140 of file Assertion.php.
◆ $authnContextDeclRef
|
private |
Definition at line 149 of file Assertion.php.
◆ $authnInstant
|
private |
Definition at line 123 of file Assertion.php.
◆ $certificates
|
private |
Definition at line 217 of file Assertion.php.
◆ $encryptedAttributes
|
private |
Definition at line 68 of file Assertion.php.
◆ $encryptedNameId
|
private |
Definition at line 59 of file Assertion.php.
◆ $encryptionKey
|
private |
Definition at line 75 of file Assertion.php.
◆ $id
|
private |
Definition at line 24 of file Assertion.php.
◆ $issueInstant
|
private |
Definition at line 31 of file Assertion.php.
◆ $issuer
|
private |
Definition at line 41 of file Assertion.php.
◆ $nameFormat
|
private |
Definition at line 201 of file Assertion.php.
◆ $nameId
|
private |
Definition at line 50 of file Assertion.php.
◆ $notBefore
|
private |
Definition at line 82 of file Assertion.php.
Referenced by SAML2\Assertion\Validation\ConstraintValidator\SubjectConfirmationNotBefore\validate().
◆ $notOnOrAfter
|
private |
Definition at line 89 of file Assertion.php.
Referenced by SAML2\Assertion\Validation\ConstraintValidator\SubjectConfirmationNotOnOrAfter\validate().
◆ $requiredEncAttributes
|
private |
Definition at line 232 of file Assertion.php.
◆ $sessionIndex
|
private |
Definition at line 116 of file Assertion.php.
◆ $sessionNotOnOrAfter
|
private |
Definition at line 107 of file Assertion.php.
◆ $signatureData
|
private |
Definition at line 224 of file Assertion.php.
◆ $signatureKey
|
private |
Definition at line 210 of file Assertion.php.
◆ $signatureMethod
|
private |
Definition at line 249 of file Assertion.php.
◆ $SubjectConfirmation
|
private |
Definition at line 239 of file Assertion.php.
◆ $validAudiences
|
private |
Definition at line 100 of file Assertion.php.
◆ $wasSignedAtConstruction
|
protected |
Definition at line 244 of file Assertion.php.
The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/saml2/src/SAML2/Assertion.php