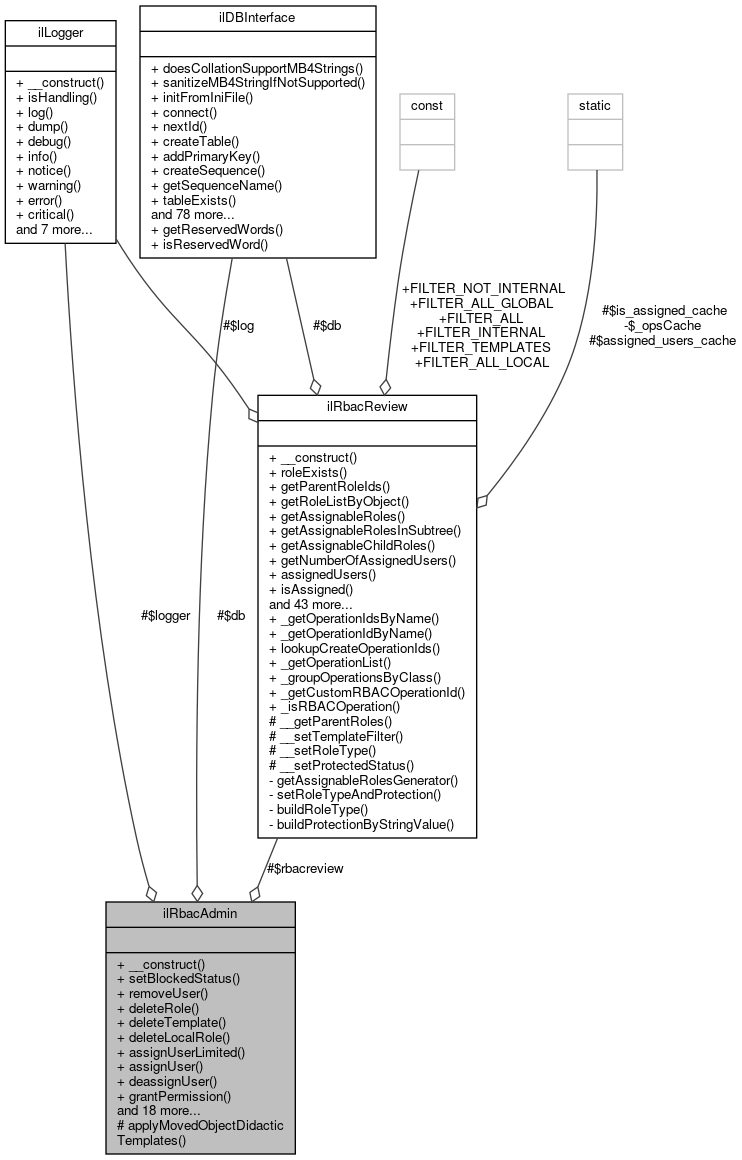
Class ilRbacAdmin Core functions for role based access control. More...
 Collaboration diagram for ilRbacAdmin:
Collaboration diagram for ilRbacAdmin:Public Member Functions | |
| __construct () | |
| Constructor @access public. More... | |
| setBlockedStatus (int $a_role_id, int $a_ref_id, bool $a_blocked_status) | |
| removeUser (int $a_usr_id) | |
| deletes a user from rbac_ua all user <-> role relations are deleted More... | |
| deleteRole (int $a_rol_id, int $a_ref_id) | |
| Deletes a role and deletes entries in rbac_pa, rbac_templates, rbac_ua, rbac_fa. More... | |
| deleteTemplate (int $a_obj_id) | |
| Deletes a template from role folder and deletes all entries in rbac_templates, rbac_fa. More... | |
| deleteLocalRole (int $a_rol_id, int $a_ref_id=0) | |
| Deletes a local role and entries in rbac_fa and rbac_templates. More... | |
| assignUserLimited (int $a_role_id, int $a_usr_id, int $a_limit, array $a_limited_roles=[]) | |
| assignUser (int $a_rol_id, int $a_usr_id) | |
| Assigns an user to a role. More... | |
| deassignUser (int $a_rol_id, int $a_usr_id) | |
| Deassigns a user from a role. More... | |
| grantPermission (int $a_rol_id, array $a_ops, int $a_ref_id) | |
| Grants a permission to an object and a specific role. More... | |
| revokePermission (int $a_ref_id, int $a_rol_id=0, bool $a_keep_protected=true) | |
| Revokes permissions of an object of one role. More... | |
| revokeSubtreePermissions (int $a_ref_id, int $a_role_id) | |
| Revoke subtree permissions. More... | |
| deleteSubtreeTemplates (int $a_ref_id, int $a_rol_id) | |
| Delete all template permissions of subtree nodes. More... | |
| revokePermissionList (array $a_ref_ids, int $a_rol_id) | |
| Revokes permissions of a LIST of objects of ONE role. More... | |
| copyRolePermissions (int $a_source_id, int $a_source_parent, int $a_dest_parent, int $a_dest_id, bool $a_consider_protected=true) | |
| Copies template permissions and permission of one role to another. More... | |
| copyRoleTemplatePermissions (int $a_source_id, int $a_source_parent, int $a_dest_parent, int $a_dest_id, bool $a_consider_protected=true) | |
| Copies template permissions of one role to another. More... | |
| copyRolePermissionIntersection (int $a_source1_id, int $a_source1_parent, int $a_source2_id, int $a_source2_parent, int $a_dest_parent, int $a_dest_id) | |
| Copies the intersection of the template permissions of two roles to a third role. More... | |
| copyRolePermissionUnion (int $a_source1_id, int $a_source1_parent, int $a_source2_id, int $a_source2_parent, int $a_dest_id, int $a_dest_parent) | |
| copyRolePermissionSubtract (int $a_source_id, int $a_source_parent, int $a_dest_id, int $a_dest_parent) | |
| Subtract role permissions. More... | |
| deleteRolePermission (int $a_rol_id, int $a_ref_id, ?string $a_type=null) | |
| Deletes all entries of a template. More... | |
| setRolePermission (int $a_rol_id, string $a_type, array $a_ops, int $a_ref_id) | |
| Inserts template permissions in rbac_templates for an specific object type. More... | |
| assignRoleToFolder (int $a_rol_id, int $a_parent, string $a_assign="y") | |
| Assigns a role to a role folder A role folder is an object to store roles. More... | |
| assignOperationToObject (int $a_type_id, int $a_ops_id) | |
| Assign an existing operation to an object Update of rbac_ta. More... | |
| deassignOperationFromObject (int $a_type_id, int $a_ops_id) | |
| Deassign an existing operation from an object Update of rbac_ta. More... | |
| setProtected (int $a_ref_id, int $a_role_id, string $a_value) | |
| Set protected. More... | |
| copyLocalRoles (int $a_source_id, int $a_target_id) | |
| Copy local roles This method creates a copy of all local role. More... | |
| initIntersectionPermissions (int $a_ref_id, int $a_role_id, int $a_role_parent, int $a_template_id, int $a_template_parent) | |
| adjustMovedObjectPermissions (int $ref_id, int $old_parent) | |
| Adjust permissions of moved objects. More... | |
Protected Member Functions | |
| applyMovedObjectDidacticTemplates (int $a_ref_id, int $a_old_parent) | |
| Apply didactic templates after object movement. More... | |
Protected Attributes | |
| ilDBInterface | $db |
| ilRbacReview | $rbacreview |
| ilLogger | $logger |
Detailed Description
Class ilRbacAdmin Core functions for role based access control.
Creation and maintenance of Relations. The main relations of Rbac are user <-> role (UR) assignment relation and the permission <-> role (PR) assignment relation. This class contains methods to 'create' and 'delete' instances of the (UR) relation e.g.: assignUser(), deassignUser() Required methods for the PR relation are grantPermission(), revokePermission()
Definition at line 31 of file class.ilRbacAdmin.php.
Constructor & Destructor Documentation
◆ __construct()
| ilRbacAdmin::__construct | ( | ) |
Constructor @access public.
Definition at line 41 of file class.ilRbacAdmin.php.
References $DIC, and ILIAS\Repository\logger().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ adjustMovedObjectPermissions()
| ilRbacAdmin::adjustMovedObjectPermissions | ( | int | $ref_id, |
| int | $old_parent | ||
| ) |
Adjust permissions of moved objects.
- Delete permissions of parent roles that do not exist in new context
- Delete role templates of parent roles that do not exist in new context
- Add permissions for parent roles that did not exist in old context
2023-08-15 sk: We need to switch off the cache here, as otherwise there seems to be no way to get an adequate reading of the new path. We switch it back on again at the end of this function.
We switch the cache back on again. See above.
Definition at line 868 of file class.ilRbacAdmin.php.
References $DIC, $log, $ref_id, ilRbacLog\add(), ilRbacLog\diffFaPa(), ilRbacLog\gatherFaPa(), ILIAS\Repository\int(), ilRbacLog\isActive(), ilObjCourse\lookupCourseNonMemberTemplatesId(), ilObjGroup\lookupGroupStatusTemplateId(), ilRbacLog\MOVE_OBJECT, and ROLE_FOLDER_ID.
 Here is the call graph for this function:
Here is the call graph for this function:◆ applyMovedObjectDidacticTemplates()
|
protected |
Apply didactic templates after object movement.
- Deprecated:
- since version 5.1.0 will be removed with 5.4 and implemented using event handler
- Todo:
- implement using event handler
Definition at line 847 of file class.ilRbacAdmin.php.
References ilDidacticTemplateActionFactory\getActionsByTemplateId(), and ilDidacticTemplateObjSettings\lookupTemplateId().
 Here is the call graph for this function:
Here is the call graph for this function:◆ assignOperationToObject()
| ilRbacAdmin::assignOperationToObject | ( | int | $a_type_id, |
| int | $a_ops_id | ||
| ) |
Assign an existing operation to an object Update of rbac_ta.
Definition at line 714 of file class.ilRbacAdmin.php.
References $res.
◆ assignRoleToFolder()
| ilRbacAdmin::assignRoleToFolder | ( | int | $a_rol_id, |
| int | $a_parent, | ||
| string | $a_assign = "y" |
||
| ) |
Assigns a role to a role folder A role folder is an object to store roles.
Every role is assigned to minimum one role folder If the inheritance of a role is stopped, a new role template will created, and the role is assigned to minimum two role folders. All roles with stopped inheritance need the flag '$a_assign = false'
Definition at line 677 of file class.ilRbacAdmin.php.
◆ assignUser()
| ilRbacAdmin::assignUser | ( | int | $a_rol_id, |
| int | $a_usr_id | ||
| ) |
Assigns an user to a role.
Update of table rbac_ua
Definition at line 188 of file class.ilRbacAdmin.php.
References $GLOBALS, $ref_id, $res, ilLDAPRoleGroupMapping\_getInstance(), ilObject\_lookupObjId(), ilObject\_lookupType(), and ilLoggerFactory\getInstance().
 Here is the call graph for this function:
Here is the call graph for this function:◆ assignUserLimited()
| ilRbacAdmin::assignUserLimited | ( | int | $a_role_id, |
| int | $a_usr_id, | ||
| int | $a_limit, | ||
| array | $a_limited_roles = [] |
||
| ) |
Definition at line 144 of file class.ilRbacAdmin.php.
References $ilDB, $res, and ilDBConstants\FETCHMODE_OBJECT.
◆ copyLocalRoles()
| ilRbacAdmin::copyLocalRoles | ( | int | $a_source_id, |
| int | $a_target_id | ||
| ) |
Copy local roles This method creates a copy of all local role.
Note: auto generated roles are excluded
Definition at line 751 of file class.ilRbacAdmin.php.
References ilObject\_lookupTitle().
 Here is the call graph for this function:
Here is the call graph for this function:◆ copyRolePermissionIntersection()
| ilRbacAdmin::copyRolePermissionIntersection | ( | int | $a_source1_id, |
| int | $a_source1_parent, | ||
| int | $a_source2_id, | ||
| int | $a_source2_parent, | ||
| int | $a_dest_parent, | ||
| int | $a_dest_id | ||
| ) |
Copies the intersection of the template permissions of two roles to a third role.
Definition at line 492 of file class.ilRbacAdmin.php.
References ilLogLevel\DEBUG, and ILIAS\Repository\logger().
 Here is the call graph for this function:
Here is the call graph for this function:◆ copyRolePermissions()
| ilRbacAdmin::copyRolePermissions | ( | int | $a_source_id, |
| int | $a_source_parent, | ||
| int | $a_dest_parent, | ||
| int | $a_dest_id, | ||
| bool | $a_consider_protected = true |
||
| ) |
Copies template permissions and permission of one role to another.
Definition at line 414 of file class.ilRbacAdmin.php.
◆ copyRolePermissionSubtract()
| ilRbacAdmin::copyRolePermissionSubtract | ( | int | $a_source_id, |
| int | $a_source_parent, | ||
| int | $a_dest_id, | ||
| int | $a_dest_parent | ||
| ) |
Subtract role permissions.
Definition at line 594 of file class.ilRbacAdmin.php.
References ilLogLevel\DEBUG, and ILIAS\Repository\logger().
 Here is the call graph for this function:
Here is the call graph for this function:◆ copyRolePermissionUnion()
| ilRbacAdmin::copyRolePermissionUnion | ( | int | $a_source1_id, |
| int | $a_source1_parent, | ||
| int | $a_source2_id, | ||
| int | $a_source2_parent, | ||
| int | $a_dest_id, | ||
| int | $a_dest_parent | ||
| ) |
Definition at line 542 of file class.ilRbacAdmin.php.
References ilLogLevel\DEBUG, and ILIAS\Repository\logger().
 Here is the call graph for this function:
Here is the call graph for this function:◆ copyRoleTemplatePermissions()
| ilRbacAdmin::copyRoleTemplatePermissions | ( | int | $a_source_id, |
| int | $a_source_parent, | ||
| int | $a_dest_parent, | ||
| int | $a_dest_id, | ||
| bool | $a_consider_protected = true |
||
| ) |
Copies template permissions of one role to another.
It's also possible to copy template permissions from/to RoleTemplateObject
Definition at line 439 of file class.ilRbacAdmin.php.
References ilLogLevel\DEBUG, and ILIAS\Repository\logger().
 Here is the call graph for this function:
Here is the call graph for this function:◆ deassignOperationFromObject()
| ilRbacAdmin::deassignOperationFromObject | ( | int | $a_type_id, |
| int | $a_ops_id | ||
| ) |
Deassign an existing operation from an object Update of rbac_ta.
Definition at line 725 of file class.ilRbacAdmin.php.
References $res.
◆ deassignUser()
| ilRbacAdmin::deassignUser | ( | int | $a_rol_id, |
| int | $a_usr_id | ||
| ) |
Deassigns a user from a role.
Update of table rbac_ua
Definition at line 230 of file class.ilRbacAdmin.php.
References $GLOBALS, $ref_id, $res, ilLDAPRoleGroupMapping\_getInstance(), ilObject\_lookupObjId(), ilObject\_lookupType(), and ilLoggerFactory\getInstance().
Referenced by ilObjBlogGUI\removeContributor(), and removeUser().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ deleteLocalRole()
| ilRbacAdmin::deleteLocalRole | ( | int | $a_rol_id, |
| int | $a_ref_id = 0 |
||
| ) |
Deletes a local role and entries in rbac_fa and rbac_templates.
Definition at line 119 of file class.ilRbacAdmin.php.
References $res, ILIAS\Repository\logger(), ilLogLevel\NOTICE, and SYSTEM_ROLE_ID.
Referenced by deleteRole().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ deleteRole()
| ilRbacAdmin::deleteRole | ( | int | $a_rol_id, |
| int | $a_ref_id | ||
| ) |
Deletes a role and deletes entries in rbac_pa, rbac_templates, rbac_ua, rbac_fa.
Definition at line 75 of file class.ilRbacAdmin.php.
References $res, ilLDAPRoleGroupMapping\_getInstance(), ilLogLevel\DEBUG, deleteLocalRole(), ILIAS\Repository\logger(), and SYSTEM_ROLE_ID.
 Here is the call graph for this function:
Here is the call graph for this function:◆ deleteRolePermission()
| ilRbacAdmin::deleteRolePermission | ( | int | $a_rol_id, |
| int | $a_ref_id, | ||
| ?string | $a_type = null |
||
| ) |
Deletes all entries of a template.
If an object type is given for third parameter only the entries for that object type are deleted Update of table rbac_templates.
Definition at line 626 of file class.ilRbacAdmin.php.
References ilLogLevel\DEBUG, and ILIAS\Repository\logger().
 Here is the call graph for this function:
Here is the call graph for this function:◆ deleteSubtreeTemplates()
| ilRbacAdmin::deleteSubtreeTemplates | ( | int | $a_ref_id, |
| int | $a_rol_id | ||
| ) |
Delete all template permissions of subtree nodes.
Definition at line 378 of file class.ilRbacAdmin.php.
References $GLOBALS.
◆ deleteTemplate()
| ilRbacAdmin::deleteTemplate | ( | int | $a_obj_id | ) |
Deletes a template from role folder and deletes all entries in rbac_templates, rbac_fa.
Definition at line 105 of file class.ilRbacAdmin.php.
References $res.
◆ grantPermission()
| ilRbacAdmin::grantPermission | ( | int | $a_rol_id, |
| array | $a_ops, | ||
| int | $a_ref_id | ||
| ) |
Grants a permission to an object and a specific role.
Update of table rbac_pa
Definition at line 260 of file class.ilRbacAdmin.php.
References $res, ilLogLevel\DEBUG, ILIAS\Repository\int(), ILIAS\Repository\logger(), and SYSTEM_ROLE_ID.
 Here is the call graph for this function:
Here is the call graph for this function:◆ initIntersectionPermissions()
| ilRbacAdmin::initIntersectionPermissions | ( | int | $a_ref_id, |
| int | $a_role_id, | ||
| int | $a_role_parent, | ||
| int | $a_template_id, | ||
| int | $a_template_parent | ||
| ) |
Definition at line 780 of file class.ilRbacAdmin.php.
References ilObject\_lookupType().
 Here is the call graph for this function:
Here is the call graph for this function:◆ removeUser()
| ilRbacAdmin::removeUser | ( | int | $a_usr_id | ) |
deletes a user from rbac_ua all user <-> role relations are deleted
Definition at line 63 of file class.ilRbacAdmin.php.
References $res, and deassignUser().
 Here is the call graph for this function:
Here is the call graph for this function:◆ revokePermission()
| ilRbacAdmin::revokePermission | ( | int | $a_ref_id, |
| int | $a_rol_id = 0, |
||
| bool | $a_keep_protected = true |
||
| ) |
Revokes permissions of an object of one role.
Update of table rbac_pa. Revokes all permission for all roles for that object (with this reference). When a role_id is given this applies only to that role
Definition at line 302 of file class.ilRbacAdmin.php.
References $res, ilLogLevel\DEBUG, ILIAS\Repository\logger(), and SYSTEM_ROLE_ID.
Referenced by ilObject\delete().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ revokePermissionList()
| ilRbacAdmin::revokePermissionList | ( | array | $a_ref_ids, |
| int | $a_rol_id | ||
| ) |
Revokes permissions of a LIST of objects of ONE role.
Update of table rbac_pa.
Definition at line 398 of file class.ilRbacAdmin.php.
References $res, ilLogLevel\DEBUG, ILIAS\Repository\logger(), and SYSTEM_ROLE_ID.
 Here is the call graph for this function:
Here is the call graph for this function:◆ revokeSubtreePermissions()
| ilRbacAdmin::revokeSubtreePermissions | ( | int | $a_ref_id, |
| int | $a_role_id | ||
| ) |
Revoke subtree permissions.
Definition at line 365 of file class.ilRbacAdmin.php.
References $GLOBALS.
◆ setBlockedStatus()
| ilRbacAdmin::setBlockedStatus | ( | int | $a_role_id, |
| int | $a_ref_id, | ||
| bool | $a_blocked_status | ||
| ) |
Definition at line 50 of file class.ilRbacAdmin.php.
References ilLoggerFactory\getLogger().
 Here is the call graph for this function:
Here is the call graph for this function:◆ setProtected()
| ilRbacAdmin::setProtected | ( | int | $a_ref_id, |
| int | $a_role_id, | ||
| string | $a_value | ||
| ) |
Set protected.
Definition at line 736 of file class.ilRbacAdmin.php.
References $res.
◆ setRolePermission()
| ilRbacAdmin::setRolePermission | ( | int | $a_rol_id, |
| string | $a_type, | ||
| array | $a_ops, | ||
| int | $a_ref_id | ||
| ) |
Inserts template permissions in rbac_templates for an specific object type.
Update of table rbac_templates
Definition at line 650 of file class.ilRbacAdmin.php.
References ILIAS\Repository\logger(), and SYSTEM_ROLE_ID.
 Here is the call graph for this function:
Here is the call graph for this function:Field Documentation
◆ $db
|
protected |
Definition at line 33 of file class.ilRbacAdmin.php.
◆ $logger
|
protected |
Definition at line 35 of file class.ilRbacAdmin.php.
◆ $rbacreview
|
protected |
Definition at line 34 of file class.ilRbacAdmin.php.
The documentation for this class was generated from the following file:
- components/ILIAS/AccessControl/classes/class.ilRbacAdmin.php