Inheritance diagram for sspmod_saml_Auth_Source_SP:
Inheritance diagram for sspmod_saml_Auth_Source_SP: Collaboration diagram for sspmod_saml_Auth_Source_SP:
Collaboration diagram for sspmod_saml_Auth_Source_SP:Public Member Functions | |
| __construct ($info, $config) | |
| Constructor for SAML SP authentication source. More... | |
| getMetadataURL () | |
| Retrieve the URL to the metadata of this SP. More... | |
| getEntityId () | |
| Retrieve the entity id of this SP. More... | |
| getMetadata () | |
| Retrieve the metadata of this SP. More... | |
| getIdPMetadata ($entityId) | |
| Retrieve the metadata of an IdP. More... | |
| sendSAML2AuthnRequest (array &$state, \SAML2\Binding $binding, \SAML2\AuthnRequest $ar) | |
| Function to actually send the authentication request. More... | |
| startSSO ($idp, array $state) | |
| Send a SSO request to an IdP. More... | |
| authenticate (&$state) | |
| Start login. More... | |
| reauthenticate (array &$state) | |
| Re-authenticate an user. More... | |
| startSLO2 (&$state) | |
| Start a SAML 2 logout operation. More... | |
| logout (&$state) | |
| Start logout operation. More... | |
| handleResponse (array $state, $idp, array $attributes) | |
| Handle a response from a SSO operation. More... | |
| handleLogout ($idpEntityId) | |
| Handle a logout request from an IdP. More... | |
 Public Member Functions inherited from SimpleSAML_Auth_Source Public Member Functions inherited from SimpleSAML_Auth_Source | |
| __construct ($info, &$config) | |
| Constructor for an authentication source. More... | |
| getAuthId () | |
| Retrieve the ID of this authentication source. More... | |
| authenticate (&$state) | |
| Process a request. More... | |
| reauthenticate (array &$state) | |
| Reauthenticate an user. More... | |
| initLogin ($return, $errorURL=null, array $params=array()) | |
| Start authentication. More... | |
| logout (&$state) | |
| Log out from this authentication source. More... | |
Static Public Member Functions | |
| static | askForIdPChange (array &$state) |
| Ask the user to log out before being able to log in again with a different identity provider. More... | |
| static | reauthLogout (array $state) |
| Log the user out before logging in again. More... | |
| static | reauthPostLogin (array $state) |
| Complete login operation after re-authenticating the user on another IdP. More... | |
| static | handleUnsolicitedAuth ($authId, array $state, $redirectTo) |
| Handle an unsolicited login operations. More... | |
| static | onProcessingCompleted (array $authProcState) |
| Called when we have completed the procssing chain. More... | |
 Static Public Member Functions inherited from SimpleSAML_Auth_Source Static Public Member Functions inherited from SimpleSAML_Auth_Source | |
| static | getSourcesOfType ($type) |
| Get sources of a specific type. More... | |
| static | completeAuth (&$state) |
| Complete authentication. More... | |
| static | loginCompleted ($state) |
| Called when a login operation has finished. More... | |
| static | completeLogout (&$state) |
| Complete logout. More... | |
| static | getById ($authId, $type=null) |
| Retrieve authentication source. More... | |
| static | logoutCallback ($state) |
| Called when the authentication source receives an external logout request. More... | |
| static | getSources () |
| Retrieve list of authentication sources. More... | |
Private Member Functions | |
| startSSO1 (SimpleSAML_Configuration $idpMetadata, array $state) | |
| Send a SAML1 SSO request to an IdP. More... | |
| startSSO2 (SimpleSAML_Configuration $idpMetadata, array $state) | |
| Send a SAML2 SSO request to an IdP. More... | |
| startDisco (array $state) | |
| Start an IdP discovery service operation. More... | |
Private Attributes | |
| $entityId | |
| $metadata | |
| $idp | |
| $discoURL | |
Additional Inherited Members | |
 Protected Member Functions inherited from SimpleSAML_Auth_Source Protected Member Functions inherited from SimpleSAML_Auth_Source | |
| addLogoutCallback ($assoc, $state) | |
| Add a logout callback association. More... | |
| callLogoutCallback ($assoc) | |
| Call a logout callback based on association. More... | |
 Static Protected Member Functions inherited from SimpleSAML_Auth_Source Static Protected Member Functions inherited from SimpleSAML_Auth_Source | |
| static | validateSource ($source, $id) |
| Make sure that the first element of an auth source is its identifier. More... | |
 Protected Attributes inherited from SimpleSAML_Auth_Source Protected Attributes inherited from SimpleSAML_Auth_Source | |
| $authId | |
Detailed Description
Constructor & Destructor Documentation
◆ __construct()
| sspmod_saml_Auth_Source_SP::__construct | ( | $info, | |
| $config | |||
| ) |
Constructor for SAML SP authentication source.
- Parameters
-
array $info Information about this authentication source. array $config Configuration.
Definition at line 43 of file SP.php.
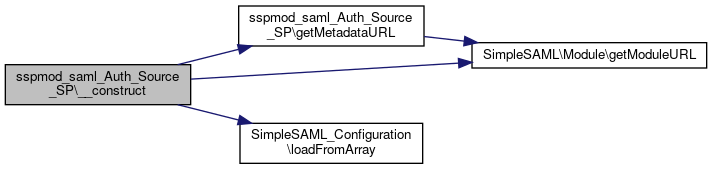
References $config, $info, getMetadataURL(), SimpleSAML\Module\getModuleURL(), and SimpleSAML_Configuration\loadFromArray().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ askForIdPChange()
|
static |
Ask the user to log out before being able to log in again with a different identity provider.
Note that this method is intended for instances of SimpleSAMLphp running as a SAML proxy, and therefore acting both as an SP and an IdP at the same time.
This method will never return.
- Parameters
-
array $state The state array. The following keys must be defined in the array: - 'saml:sp:IdPMetadata': a SimpleSAML_Configuration object containing the metadata of the IdP that authenticated the user in the current session.
- 'saml:sp:AuthId': the identifier of the current authentication source.
- 'core:IdP': the identifier of the local IdP.
- 'SPMetadata': an array with the metadata of this local SP.
- Exceptions
-
SimpleSAML_Error_NoPassive In case the authentication request was passive.
Definition at line 521 of file SP.php.
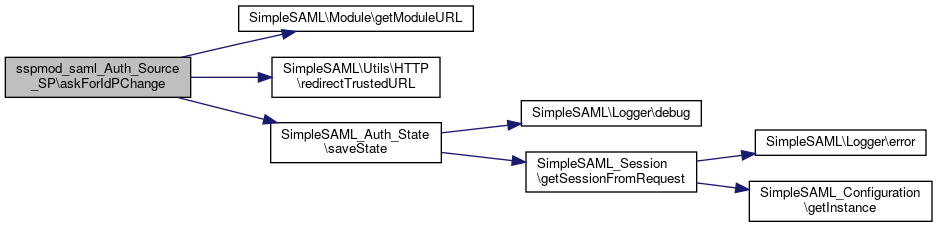
References $id, $state, $url, SimpleSAML\Module\getModuleURL(), SimpleSAML\Utils\HTTP\redirectTrustedURL(), and SimpleSAML_Auth_State\saveState().
Referenced by reauthenticate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ authenticate()
| sspmod_saml_Auth_Source_SP::authenticate | ( | & | $state | ) |
Start login.
This function saves the information about the login, and redirects to the IdP.
- Parameters
-
array &$state Information about the current authentication.
Reimplemented from SimpleSAML_Auth_Source.
Definition at line 392 of file SP.php.
References SimpleSAML_Auth_Source\$authId, $idp, $mdh, $state, SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), startDisco(), and startSSO().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getEntityId()
| sspmod_saml_Auth_Source_SP::getEntityId | ( | ) |
◆ getIdPMetadata()
| sspmod_saml_Auth_Source_SP::getIdPMetadata | ( | $entityId | ) |
Retrieve the metadata of an IdP.
- Parameters
-
string $entityId The entity id of the IdP.
- Returns
- SimpleSAML_Configuration The metadata of the IdP.
Definition at line 108 of file SP.php.
References $entityId, SimpleSAML\Logger\debug(), and SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler().
Referenced by reauthenticate(), startSLO2(), and startSSO().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getMetadata()
| sspmod_saml_Auth_Source_SP::getMetadata | ( | ) |
Retrieve the metadata of this SP.
- Returns
- SimpleSAML_Configuration The metadata of this SP.
Definition at line 95 of file SP.php.
References $metadata.
◆ getMetadataURL()
| sspmod_saml_Auth_Source_SP::getMetadataURL | ( | ) |
Retrieve the URL to the metadata of this SP.
- Returns
- string The metadata URL.
Definition at line 73 of file SP.php.
References SimpleSAML\Module\getModuleURL().
Referenced by __construct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ handleLogout()
| sspmod_saml_Auth_Source_SP::handleLogout | ( | $idpEntityId | ) |
Handle a logout request from an IdP.
- Parameters
-
string $idpEntityId The entity ID of the IdP.
Definition at line 729 of file SP.php.
References $idpEntityId, and SimpleSAML_Auth_Source\callLogoutCallback().
 Here is the call graph for this function:
Here is the call graph for this function:◆ handleResponse()
| sspmod_saml_Auth_Source_SP::handleResponse | ( | array | $state, |
| $idp, | |||
| array | $attributes | ||
| ) |
Handle a response from a SSO operation.
- Parameters
-
array $state The authentication state. string $idp The entity id of the IdP. array $attributes The attributes.
Definition at line 686 of file SP.php.
References $attributes, $idp, $idpMetadata, $state, and onProcessingCompleted().
 Here is the call graph for this function:
Here is the call graph for this function:◆ handleUnsolicitedAuth()
|
static |
Handle an unsolicited login operations.
This method creates a session from the information received. It will then redirect to the given URL. This is used to handle IdP initiated SSO. This method will never return.
- Parameters
-
string $authId The id of the authentication source that received the request. array $state A state array. string $redirectTo The URL we should redirect the user to after updating the session. The function will check if the URL is allowed, so there is no need to manually check the URL on beforehand. Please refer to the 'trusted.url.domains' configuration directive for more information about allowing (or disallowing) URLs.
Definition at line 749 of file SP.php.
References SimpleSAML_Auth_Source\$authId, $session, $state, SimpleSAML_Auth_State\getPersistentAuthData(), SimpleSAML_Session\getSessionFromRequest(), and SimpleSAML\Utils\HTTP\redirectUntrustedURL().
Referenced by SimpleSAML_Auth_Default\handleUnsolicitedAuth(), and onProcessingCompleted().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ logout()
| sspmod_saml_Auth_Source_SP::logout | ( | & | $state | ) |
Start logout operation.
- Parameters
-
array $state The logout state.
Reimplemented from SimpleSAML_Auth_Source.
Definition at line 660 of file SP.php.
References $state, and startSLO2().
 Here is the call graph for this function:
Here is the call graph for this function:◆ onProcessingCompleted()
|
static |
Called when we have completed the procssing chain.
- Parameters
-
array $authProcState The processing chain state.
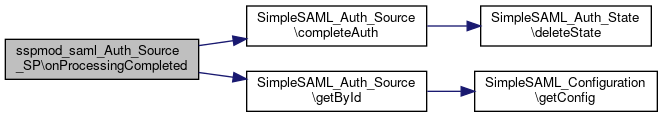
Definition at line 765 of file SP.php.
References $idp, $source, $sourceId, $state, SimpleSAML_Auth_Source\completeAuth(), SimpleSAML_Auth_Source\getById(), and handleUnsolicitedAuth().
Referenced by handleResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ reauthenticate()
| sspmod_saml_Auth_Source_SP::reauthenticate | ( | array & | $state | ) |
Re-authenticate an user.
This function is called by the IdP to give the authentication source a chance to interact with the user even in the case when the user is already authenticated.
- Parameters
-
array &$state Information about the current authentication.
Reimplemented from SimpleSAML_Auth_Source.
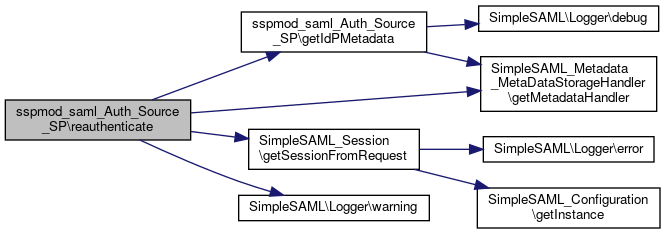
Definition at line 447 of file SP.php.
References SimpleSAML_Auth_Source\$authId, $data, $mdh, $session, $state, askForIdPChange(), getIdPMetadata(), SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), SimpleSAML_Session\getSessionFromRequest(), and SimpleSAML\Logger\warning().
 Here is the call graph for this function:
Here is the call graph for this function:◆ reauthLogout()
|
static |
Log the user out before logging in again.
This method will never return.
- Parameters
-
array $state The state array.
Definition at line 548 of file SP.php.
References $idp, $state, SimpleSAML\Logger\debug(), and SimpleSAML_IdP\getByState().
 Here is the call graph for this function:
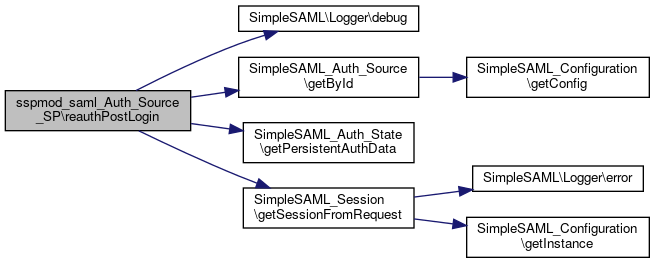
Here is the call graph for this function:◆ reauthPostLogin()
|
static |
Complete login operation after re-authenticating the user on another IdP.
- Parameters
-
array $state The authentication state.
Definition at line 568 of file SP.php.
References SimpleSAML_Auth_Source\$authId, $session, $state, SimpleSAML_Auth_State\getPersistentAuthData(), and SimpleSAML_Session\getSessionFromRequest().
 Here is the call graph for this function:
Here is the call graph for this function:◆ sendSAML2AuthnRequest()
| sspmod_saml_Auth_Source_SP::sendSAML2AuthnRequest | ( | array & | $state, |
| \SAML2\Binding | $binding, | ||
| \SAML2\AuthnRequest | $ar | ||
| ) |
Function to actually send the authentication request.
This function does not return.
- Parameters
-
array &$state The state array. \SAML2\Binding $binding The binding. \SAML2\AuthnRequest $ar The authentication request.
Definition at line 316 of file SP.php.
References $binding.
Referenced by startSSO2().
 Here is the caller graph for this function:
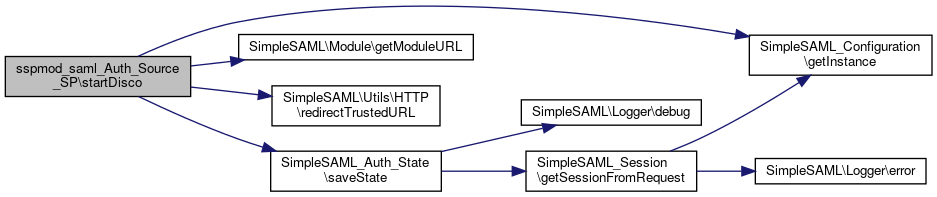
Here is the caller graph for this function:◆ startDisco()
|
private |
Start an IdP discovery service operation.
- Parameters
-
array $state The state array.
Definition at line 353 of file SP.php.
References $config, $discoURL, $id, $params, $returnTo, $state, SimpleSAML_Configuration\getInstance(), SimpleSAML\Module\getModuleURL(), SimpleSAML\Utils\HTTP\redirectTrustedURL(), and SimpleSAML_Auth_State\saveState().
Referenced by authenticate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
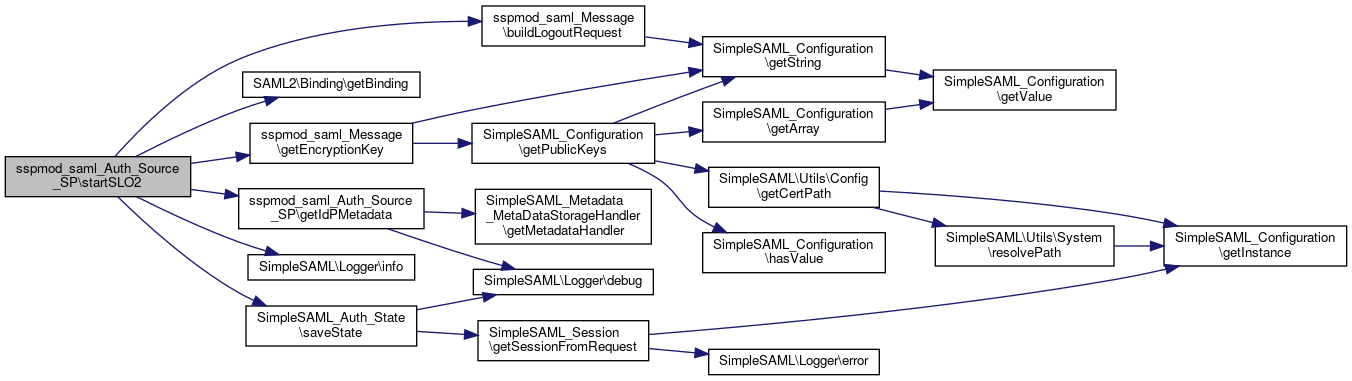
Here is the caller graph for this function:◆ startSLO2()
| sspmod_saml_Auth_Source_SP::startSLO2 | ( | & | $state | ) |
Start a SAML 2 logout operation.
- Parameters
-
array $state The logout state.
Definition at line 612 of file SP.php.
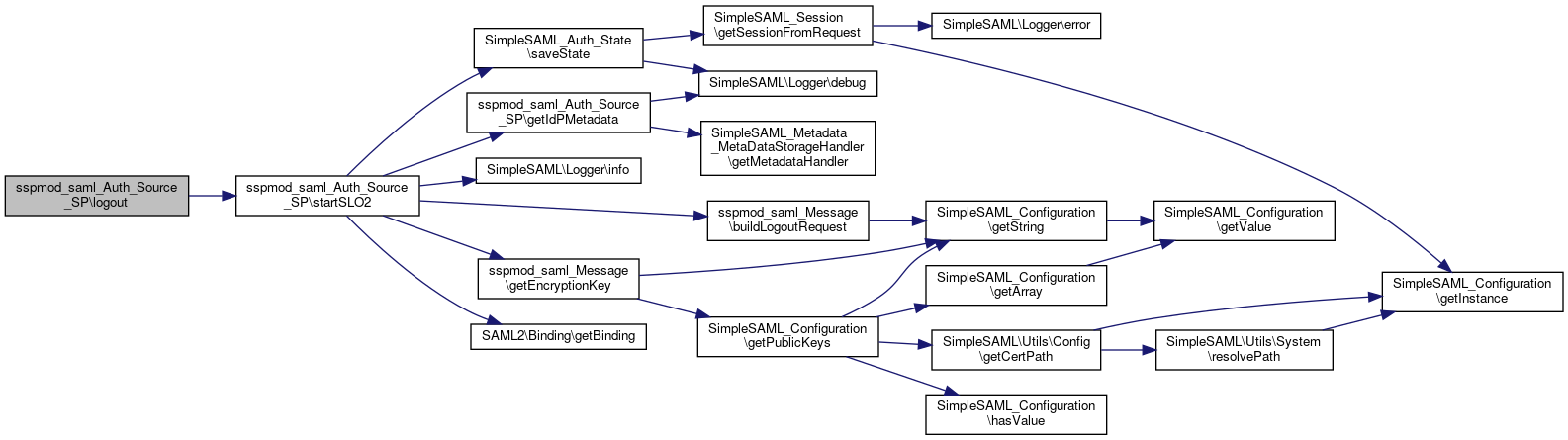
References $encryptNameId, $endpoint, $id, $idp, $idpMetadata, $lr, $nameId, $sessionIndex, $state, sspmod_saml_Message\buildLogoutRequest(), SAML2\Binding\getBinding(), sspmod_saml_Message\getEncryptionKey(), getIdPMetadata(), SimpleSAML\Logger\info(), and SimpleSAML_Auth_State\saveState().
Referenced by logout().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ startSSO()
| sspmod_saml_Auth_Source_SP::startSSO | ( | $idp, | |
| array | $state | ||
| ) |
Send a SSO request to an IdP.
- Parameters
-
string $idp The entity ID of the IdP. array $state The state array for the current authentication.
Definition at line 328 of file SP.php.
References $idp, $idpMetadata, $type, getIdPMetadata(), startSSO1(), and startSSO2().
Referenced by authenticate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ startSSO1()
|
private |
Send a SAML1 SSO request to an IdP.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. array $state The state array for the current authentication.
Definition at line 145 of file SP.php.
References $id, $idpEntityId, $idpMetadata, $state, $url, SimpleSAML\Logger\debug(), SimpleSAML\Module\getModuleURL(), SimpleSAML\Utils\HTTP\redirectTrustedURL(), and SimpleSAML_Auth_State\saveState().
Referenced by startSSO().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ startSSO2()
|
private |
Send a SAML2 SSO request to an IdP.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. array $state The state array for the current authentication.
Definition at line 182 of file SP.php.
References $dst, $id, $idpMetadata, $state, SimpleSAML\Utils\Arrays\arrayize(), sspmod_saml_Message\buildAuthnRequest(), SAML2\Constants\COMPARISON_EXACT, SimpleSAML\Logger\debug(), SAML2\Binding\getBinding(), SimpleSAML_Auth_State\saveState(), sendSAML2AuthnRequest(), and SimpleSAML_Auth_State\throwException().
Referenced by startSSO().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:Field Documentation
◆ $discoURL
|
private |
Definition at line 34 of file SP.php.
Referenced by startDisco().
◆ $entityId
|
private |
Definition at line 10 of file SP.php.
Referenced by getEntityId(), and getIdPMetadata().
◆ $idp
|
private |
Definition at line 26 of file SP.php.
Referenced by authenticate(), handleResponse(), onProcessingCompleted(), reauthLogout(), startSLO2(), and startSSO().
◆ $metadata
|
private |
Definition at line 18 of file SP.php.
Referenced by getMetadata().
The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/modules/saml/lib/Auth/Source/SP.php