Collaboration diagram for sspmod_saml_Message:
Collaboration diagram for sspmod_saml_Message:Static Public Member Functions | |
| static | addSign (SimpleSAML_Configuration $srcMetadata, SimpleSAML_Configuration $dstMetadata, \SAML2\SignedElement $element) |
| Add signature key and sender certificate to an element (Message or Assertion). More... | |
| static | checkSign (SimpleSAML_Configuration $srcMetadata, \SAML2\SignedElement $element) |
| Check the signature on a SAML2 message or assertion. More... | |
| static | validateMessage (SimpleSAML_Configuration $srcMetadata, SimpleSAML_Configuration $dstMetadata, \SAML2\Message $message) |
| Check signature on a SAML2 message if enabled. More... | |
| static | getDecryptionKeys (SimpleSAML_Configuration $srcMetadata, SimpleSAML_Configuration $dstMetadata) |
| Retrieve the decryption keys from metadata. More... | |
| static | getBlacklistedAlgorithms (SimpleSAML_Configuration $srcMetadata, SimpleSAML_Configuration $dstMetadata) |
| Retrieve blacklisted algorithms. More... | |
| static | getResponseError (\SAML2\StatusResponse $response) |
| Retrieve the status code of a response as a sspmod_saml_Error. More... | |
| static | buildAuthnRequest (SimpleSAML_Configuration $spMetadata, SimpleSAML_Configuration $idpMetadata) |
| Build an authentication request based on information in the metadata. More... | |
| static | buildLogoutRequest (SimpleSAML_Configuration $srcMetadata, SimpleSAML_Configuration $dstMetadata) |
| Build a logout request based on information in the metadata. More... | |
| static | buildLogoutResponse (SimpleSAML_Configuration $srcMetadata, SimpleSAML_Configuration $dstMetadata) |
| Build a logout response based on information in the metadata. More... | |
| static | processResponse (SimpleSAML_Configuration $spMetadata, SimpleSAML_Configuration $idpMetadata, \SAML2\Response $response) |
| Process a response message. More... | |
| static | getEncryptionKey (SimpleSAML_Configuration $metadata) |
| Retrieve the encryption key for the given entity. More... | |
Static Private Member Functions | |
| static | addRedirectSign (SimpleSAML_Configuration $srcMetadata, SimpleSAML_Configuration $dstMetadata, \SAML2\Message $message) |
| Add signature key and and senders certificate to message. More... | |
| static | findCertificate (array $certFingerprints, array $certificates) |
| Find the certificate used to sign a message or assertion. More... | |
| static | decryptAssertion (SimpleSAML_Configuration $srcMetadata, SimpleSAML_Configuration $dstMetadata, $assertion) |
| Decrypt an assertion. More... | |
| static | processAssertion (SimpleSAML_Configuration $spMetadata, SimpleSAML_Configuration $idpMetadata, \SAML2\Response $response, $assertion, $responseSigned) |
| Process an assertion in a response. More... | |
Detailed Description
Definition at line 10 of file Message.php.
Member Function Documentation
◆ addRedirectSign()
|
staticprivate |
Add signature key and and senders certificate to message.
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender. SimpleSAML_Configuration $dstMetadata The metadata of the recipient. \SAML2\Message $message The message we should add the data to.
Definition at line 79 of file Message.php.
References $message, addSign(), and SimpleSAML_Configuration\getBoolean().
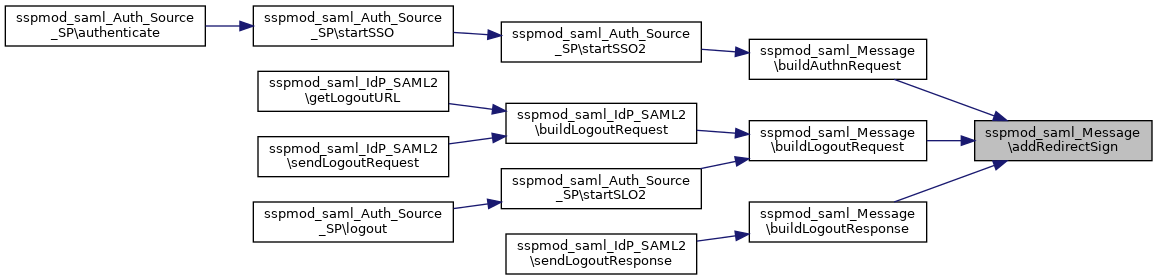
Referenced by buildAuthnRequest(), buildLogoutRequest(), and buildLogoutResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ addSign()
|
static |
Add signature key and sender certificate to an element (Message or Assertion).
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender. SimpleSAML_Configuration $dstMetadata The metadata of the recipient. \SAML2\SignedElement $element The element we should add the data to.
Definition at line 20 of file Message.php.
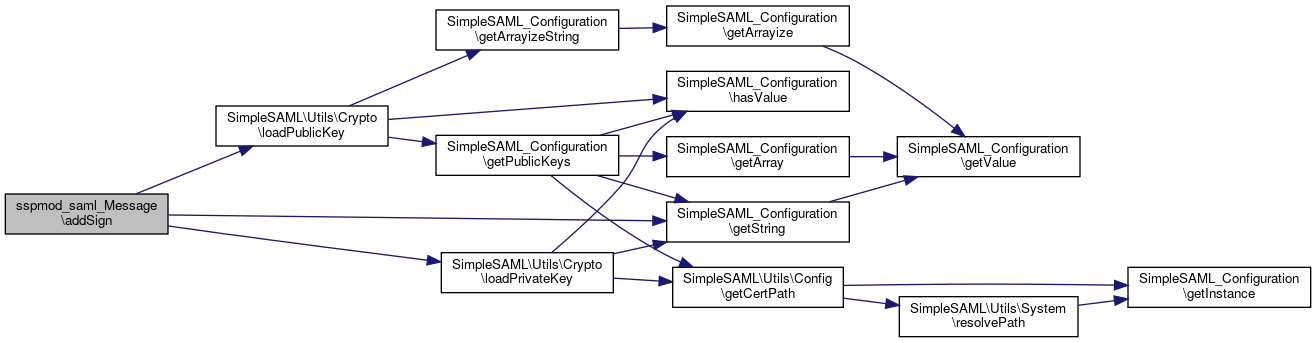
References $algo, SimpleSAML_Configuration\getString(), SimpleSAML\Utils\Crypto\loadPrivateKey(), and SimpleSAML\Utils\Crypto\loadPublicKey().
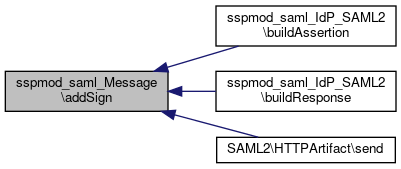
Referenced by addRedirectSign(), sspmod_saml_IdP_SAML2\buildAssertion(), and sspmod_saml_IdP_SAML2\buildResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ buildAuthnRequest()
|
static |
Build an authentication request based on information in the metadata.
- Parameters
-
SimpleSAML_Configuration $spMetadata The metadata of the service provider. SimpleSAML_Configuration $idpMetadata The metadata of the identity provider.
- Returns
- \SAML2\AuthnRequest An authentication request object.
Definition at line 431 of file Message.php.
References $idpMetadata, $spMetadata, addRedirectSign(), and SimpleSAML_Configuration\loadFromArray().
Referenced by sspmod_saml_Auth_Source_SP\startSSO2().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ buildLogoutRequest()
|
static |
Build a logout request based on information in the metadata.
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender. SimpleSAML_Configuration $dstMetadata The metadata of the recipient.
- Returns
- \SAML2\LogoutRequest A logout request object.
Definition at line 501 of file Message.php.
References $lr, addRedirectSign(), and SimpleSAML_Configuration\getString().
Referenced by sspmod_saml_IdP_SAML2\buildLogoutRequest(), and sspmod_saml_Auth_Source_SP\startSLO2().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ buildLogoutResponse()
|
static |
Build a logout response based on information in the metadata.
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender. SimpleSAML_Configuration $dstMetadata The metadata of the recipient.
- Returns
- \SAML2\LogoutResponse A logout response object.
Definition at line 521 of file Message.php.
References $lr, addRedirectSign(), and SimpleSAML_Configuration\getString().
Referenced by sspmod_saml_IdP_SAML2\sendLogoutResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ checkSign()
|
static |
Check the signature on a SAML2 message or assertion.
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender. \SAML2\SignedElement $element Either a \SAML2\Response or a \SAML2\Assertion.
- Returns
- boolean True if the signature is correct, false otherwise.
- Exceptions
-
SimpleSAML_Error_Exception if there is not certificate in the metadata for the entity.
- Exceptions
-
Exception if the signature validation fails with an exception.
Definition at line 159 of file Message.php.
References $certificates, $i, $key, $keys, $res, SimpleSAML\Logger\debug(), findCertificate(), SimpleSAML_Configuration\getArrayizeString(), SimpleSAML_Configuration\getPublicKeys(), SimpleSAML_Configuration\getString(), SimpleSAML_Configuration\hasValue(), and SimpleSAML\Logger\notice().
Referenced by processResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ decryptAssertion()
|
staticprivate |
Decrypt an assertion.
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender (IdP). SimpleSAML_Configuration $dstMetadata The metadata of the recipient (SP). \SAML2\Assertion | \SAML2\EncryptedAssertion $assertion The assertion we are decrypting.
- Returns
- \SAML2\Assertion The assertion.
- Exceptions
-
SimpleSAML_Error_Exception if encryption is enabled but the assertion is not encrypted, or if we cannot get the decryption keys.
- Exceptions
-
Exception if decryption fails for whatever reason.
Definition at line 367 of file Message.php.
References $i, $key, $keys, $ret, SimpleSAML\Logger\debug(), getBlacklistedAlgorithms(), SimpleSAML_Configuration\getBoolean(), and getDecryptionKeys().
Referenced by processAssertion().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ findCertificate()
|
staticprivate |
Find the certificate used to sign a message or assertion.
An exception is thrown if we are unable to locate the certificate.
- Parameters
-
array $certFingerprints The fingerprints we are looking for. array $certificates Array of certificates.
- Returns
- string Certificate, in PEM-format.
- Exceptions
-
SimpleSAML_Error_Exception if we cannot find the certificate matching the fingerprint.
Definition at line 124 of file Message.php.
References $certificates.
Referenced by checkSign().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getBlacklistedAlgorithms()
|
static |
Retrieve blacklisted algorithms.
Remote configuration overrides local configuration.
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender. SimpleSAML_Configuration $dstMetadata The metadata of the recipient.
- Returns
- array Array of blacklisted algorithms.
Definition at line 342 of file Message.php.
References SimpleSAML_Configuration\getArray().
Referenced by decryptAssertion(), and processAssertion().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getDecryptionKeys()
|
static |
Retrieve the decryption keys from metadata.
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender (IdP). SimpleSAML_Configuration $dstMetadata The metadata of the recipient (SP).
- Returns
- array Array of decryption keys.
Definition at line 291 of file Message.php.
References $key, $keys, SimpleSAML_Configuration\getString(), and SimpleSAML\Utils\Crypto\loadPrivateKey().
Referenced by decryptAssertion(), and processAssertion().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getEncryptionKey()
|
static |
Retrieve the encryption key for the given entity.
- Parameters
-
SimpleSAML_Configuration $metadata The metadata of the entity.
- Returns
- \RobRichards\XMLSecLibs\XMLSecurityKey The encryption key.
- Exceptions
-
SimpleSAML_Error_Exception if there is no supported encryption key in the metadata of this entity.
Definition at line 829 of file Message.php.
References $key, $keys, and $metadata.
Referenced by sspmod_saml_IdP_SAML2\buildAssertion(), sspmod_saml_IdP_SAML2\buildLogoutRequest(), and sspmod_saml_Auth_Source_SP\startSLO2().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getResponseError()
|
static |
Retrieve the status code of a response as a sspmod_saml_Error.
- Parameters
-
\SAML2\StatusResponse $response The response.
- Returns
- sspmod_saml_Error The error.
Definition at line 417 of file Message.php.
References $response.
Referenced by processResponse(), and sspmod_saml_IdP_SAML2\receiveLogoutMessage().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ processAssertion()
|
staticprivate |
Process an assertion in a response.
- Parameters
-
SimpleSAML_Configuration $spMetadata The metadata of the service provider. SimpleSAML_Configuration $idpMetadata The metadata of the identity provider. \SAML2\Response $response The response containing the assertion. \SAML2\Assertion | \SAML2\EncryptedAssertion $assertion The assertion. bool $responseSigned Whether the response is signed.
- Returns
- \SAML2\Assertion The assertion, if it is valid.
- Exceptions
-
SimpleSAML_Error_Exception if an error occurs while trying to validate the assertion, or if a assertion is not signed and it should be, or if we are unable to decrypt the NameID due to a local failure (missing or invalid decryption key).
- Exceptions
-
Exception if we couldn't decrypt the NameID for unexpected reasons.
Definition at line 601 of file Message.php.
References $_SERVER, $attributes, $i, $idpMetadata, $key, $keys, $name, $response, $sc, $spEntityId, $spMetadata, data, SimpleSAML\Logger\debug(), decryptAssertion(), getBlacklistedAlgorithms(), getDecryptionKeys(), and SimpleSAML\Utils\HTTP\getSelfURLNoQuery().
Referenced by processResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ processResponse()
|
static |
Process a response message.
If the response is an error response, we will throw a sspmod_saml_Error exception with the error.
- Parameters
-
SimpleSAML_Configuration $spMetadata The metadata of the service provider. SimpleSAML_Configuration $idpMetadata The metadata of the identity provider. \SAML2\Response $response The response.
- Returns
- array Array with \SAML2\Assertion objects, containing valid assertions from the response.
- Exceptions
-
SimpleSAML_Error_Exception if there are no assertions in the response.
- Exceptions
-
Exception if the destination of the response does not match the current URL.
Definition at line 548 of file Message.php.
References $idpMetadata, $response, $ret, $spMetadata, checkSign(), getResponseError(), SimpleSAML\Utils\HTTP\getSelfURLNoQuery(), and processAssertion().
 Here is the call graph for this function:
Here is the call graph for this function:◆ validateMessage()
|
static |
Check signature on a SAML2 message if enabled.
- Parameters
-
SimpleSAML_Configuration $srcMetadata The metadata of the sender. SimpleSAML_Configuration $dstMetadata The metadata of the recipient. \SAML2\Message $message The message we should check the signature on.
- Exceptions
-
SimpleSAML_Error_Exception if message validation is enabled, but there is no signature in the message.
Definition at line 246 of file Message.php.
References $message, and SimpleSAML_Configuration\getBoolean().
Referenced by sspmod_saml_IdP_SAML2\receiveAuthnRequest(), and sspmod_saml_IdP_SAML2\receiveLogoutMessage().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/modules/saml/lib/Message.php