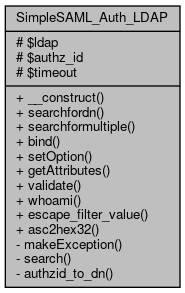
Collaboration diagram for SimpleSAML_Auth_LDAP:
Collaboration diagram for SimpleSAML_Auth_LDAP:Public Member Functions | |
| __construct ($hostname, $enable_tls=true, $debug=false, $timeout=0, $port=389, $referrals=true) | |
| Private constructor restricts instantiation to getInstance(). More... | |
| searchfordn ($base, $attribute, $value, $allowZeroHits=false, $searchFilter=null, $scope='subtree') | |
| Search for a DN. More... | |
| searchformultiple ($bases, $filters, $attributes=array(), $and=true, $escape=true, $scope='subtree') | |
| This method was created specifically for the ldap:AttributeAddUsersGroups->searchActiveDirectory() method, but could be used for other LDAP search needs. More... | |
| bind ($dn, $password, array $sasl_args=null) | |
| Bind to LDAP with a specific DN and password. More... | |
| setOption ($option, $value) | |
| Applies an LDAP option to the current connection. More... | |
| getAttributes ($dn, $attributes=null, $maxsize=null) | |
| Search a given DN for attributes, and return the resulting associative array. More... | |
| validate ($config, $username, $password=null) | |
| Enter description here... More... | |
| whoami ($searchBase, $searchAttributes) | |
| ldap_exop_whoami accessor, if available. More... | |
Static Public Member Functions | |
| static | escape_filter_value ($values=array(), $singleValue=true) |
| Borrowed function from PEAR:LDAP. More... | |
| static | asc2hex32 ($string) |
| Borrowed function from PEAR:LDAP. More... | |
Protected Attributes | |
| $ldap = null | |
| $authz_id = null | |
| LDAP user: authz_id if SASL is in use, binding dn otherwise. More... | |
| $timeout = 0 | |
Private Member Functions | |
| makeException ($description, $type=null) | |
| Convenience method to create an LDAPException as well as log the description. More... | |
| search ($base, $attribute, $value, $searchFilter=null, $scope="subtree") | |
| Search for DN from a single base. More... | |
| authzid_to_dn ($searchBase, $searchAttributes, $authz_id) | |
| Convert SASL authz_id into a DN. More... | |
Detailed Description
Constructor & Destructor Documentation
◆ __construct()
| SimpleSAML_Auth_LDAP::__construct | ( | $hostname, | |
$enable_tls = true, |
|||
$debug = false, |
|||
$timeout = 0, |
|||
$port = 389, |
|||
$referrals = true |
|||
| ) |
Private constructor restricts instantiation to getInstance().
- Parameters
-
string $hostname bool $enable_tls bool $debug int $timeout int $port bool $referrals
Definition at line 56 of file LDAP.php.
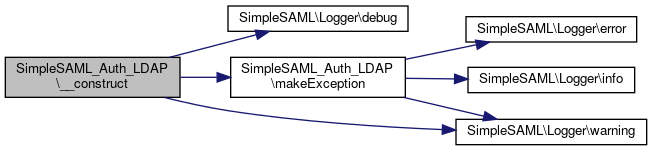
References $timeout, __construct(), SimpleSAML\Logger\debug(), ERR_INTERNAL, makeException(), and SimpleSAML\Logger\warning().
Referenced by __construct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:Member Function Documentation
◆ asc2hex32()
|
static |
Borrowed function from PEAR:LDAP.
Converts all ASCII chars < 32 to "\HEX"
- Parameters
-
string $string String to convert
- Returns
- string
Definition at line 704 of file LDAP.php.
References $i.
◆ authzid_to_dn()
|
private |
Convert SASL authz_id into a DN.
Definition at line 722 of file LDAP.php.
◆ bind()
| SimpleSAML_Auth_LDAP::bind | ( | $dn, | |
| $password, | |||
| array | $sasl_args = null |
||
| ) |
Bind to LDAP with a specific DN and password.
Simple wrapper around ldap_bind() with some additional logging.
- Parameters
-
string $dn The DN used. string $password The password used. array $sasl_args Array of SASL options for SASL bind
- Returns
- bool Returns TRUE if successful, FALSE if LDAP_INVALID_CREDENTIALS, LDAP_X_PROXY_AUTHZ_FAILURE, LDAP_INAPPROPRIATE_AUTH, LDAP_INSUFFICIENT_ACCESS
- Exceptions
-
SimpleSAML_Error_Exception on other errors
Definition at line 446 of file LDAP.php.
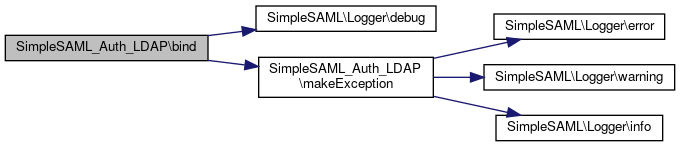
References $password, and SimpleSAML\Logger\debug().
 Here is the call graph for this function:
Here is the call graph for this function:◆ escape_filter_value()
|
static |
Borrowed function from PEAR:LDAP.
Escapes the given VALUES according to RFC 2254 so that they can be safely used in LDAP filters.
Any control characters with an ACII code < 32 as well as the characters with special meaning in LDAP filters "*", "(", ")", and "\" (the backslash) are converted into the representation of a backslash followed by two hex digits representing the hexadecimal value of the character.
- Parameters
-
string | array $values Array of values to escape
- Returns
- array Array $values, but escaped
Definition at line 666 of file LDAP.php.
References $key, $values, and SimpleSAML\Utils\Arrays\arrayize().
Referenced by sspmod_ldap_Auth_Process_AttributeAddFromLDAP\process().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getAttributes()
| SimpleSAML_Auth_LDAP::getAttributes | ( | $dn, | |
$attributes = null, |
|||
$maxsize = null |
|||
| ) |
Search a given DN for attributes, and return the resulting associative array.
- Parameters
-
string $dn The DN of an element. string | array $attributes The names of the attribute(s) to retrieve. Defaults to NULL; that is, all available attributes. Note that this is not very effective. int $maxsize The maximum size of any attribute's value(s). If exceeded, the attribute will not be returned.
- Returns
- array The array of attributes and their values.
Definition at line 545 of file LDAP.php.
References $attributes, $description, $i, $name, $result, $values, SimpleSAML\Logger\debug(), size, and SimpleSAML\Logger\warning().
 Here is the call graph for this function:
Here is the call graph for this function:◆ makeException()
|
private |
Convenience method to create an LDAPException as well as log the description.
- Parameters
-
string $description The exception's description
- Returns
- Exception
Definition at line 124 of file LDAP.php.
References $description, $type, SimpleSAML\Logger\error(), SimpleSAML\Logger\info(), and SimpleSAML\Logger\warning().
Referenced by __construct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ search()
|
private |
Search for DN from a single base.
- Parameters
-
string $base Indication of root of subtree to search string | array $attribute The attribute name(s) to search for. string $value The attribute value to search for. Additional search filter string | null $searchFilter The scope of the search string $scope
- Returns
- string The DN of the resulting found element.
- Exceptions
-
SimpleSAML_Error_Exception if: - Attribute parameter is wrong type
SimpleSAML_Error_AuthSource if: - Not able to connect to LDAP server
- False search result
- Count return false
- Searche found more than one result
- Failed to get first entry from result
- Failed to get DN for entry
SimpleSAML_Error_UserNotFound if: - Zero entries were found
Definition at line 208 of file LDAP.php.
References $base, $result, SimpleSAML\Logger\debug(), ERR_AS_DATA_INCONSIST, and ERR_NO_USER.
 Here is the call graph for this function:
Here is the call graph for this function:◆ searchfordn()
| SimpleSAML_Auth_LDAP::searchfordn | ( | $base, | |
| $attribute, | |||
| $value, | |||
$allowZeroHits = false, |
|||
$searchFilter = null, |
|||
$scope = 'subtree' |
|||
| ) |
Search for a DN.
- Parameters
-
string | array $base The base, or bases, which to search from. string | array $attribute The attribute name(s) searched for. string $value The attribute value searched for. bool $allowZeroHits Determines if the method will throw an exception if no hits are found. Defaults to FALSE. string | null $searchFilter Additional searchFilter to be added to the (attribute=value) filter string $scope The scope of the search
- Returns
- string The DN of the matching element, if found. If no element was found and $allowZeroHits is set to FALSE, an exception will be thrown; otherwise NULL will be returned.
- Exceptions
-
SimpleSAML_Error_AuthSource if: - LDAP search encounter some problems when searching cataloge
- Not able to connect to LDAP server
SimpleSAML_Error_UserNotFound if: - $allowZeroHits is FALSE and no result is found
Definition at line 291 of file LDAP.php.
References $base, $current, $result, SimpleSAML\Utils\Arrays\arrayize(), and SimpleSAML\Logger\debug().
 Here is the call graph for this function:
Here is the call graph for this function:◆ searchformultiple()
| SimpleSAML_Auth_LDAP::searchformultiple | ( | $bases, | |
| $filters, | |||
$attributes = array(), |
|||
$and = true, |
|||
$escape = true, |
|||
$scope = 'subtree' |
|||
| ) |
This method was created specifically for the ldap:AttributeAddUsersGroups->searchActiveDirectory() method, but could be used for other LDAP search needs.
It will search LDAP and return all the entries.
- Exceptions
-
Exception
- Parameters
-
string | array $bases string | array $filters Array of 'attribute' => 'values' to be combined into the filter, or a raw filter string string | array $attributes Array of attributes requested from LDAP bool $and If multiple filters defined, then either bind them with & or | bool $escape Weather to escape the filter values or not string $scope The scope of the search
- Returns
- array
Definition at line 335 of file LDAP.php.
References $attributes, $base, $i, $name, $result, $results, ERR_INTERNAL, and ERR_NO_USER.
◆ setOption()
| SimpleSAML_Auth_LDAP::setOption | ( | $option, | |
| $value | |||
| ) |
Applies an LDAP option to the current connection.
- Exceptions
-
Exception
- Parameters
-
$option $value
- Returns
- void
Definition at line 510 of file LDAP.php.
References SimpleSAML\Logger\debug(), and ERR_INTERNAL.
 Here is the call graph for this function:
Here is the call graph for this function:◆ validate()
| SimpleSAML_Auth_LDAP::validate | ( | $config, | |
| $username, | |||
$password = null |
|||
| ) |
Enter description here...
- Parameters
-
array $config string $username string $password
- Returns
- array|bool
Definition at line 618 of file LDAP.php.
References $attributes, $config, $password, and SimpleSAML\Logger\info().
 Here is the call graph for this function:
Here is the call graph for this function:◆ whoami()
| SimpleSAML_Auth_LDAP::whoami | ( | $searchBase, | |
| $searchAttributes | |||
| ) |
ldap_exop_whoami accessor, if available.
Use requested authz_id otherwise.
ldap_exop_whoami() has been provided as a third party patch that waited several years to get its way upstream: http://cvsweb.netbsd.org/bsdweb.cgi/pkgsrc/databases/php-ldap/files
When it was integrated into PHP repository, the function prototype was changed, The new prototype was used in third party patch for PHP 7.0 and 7.1, hence the version test below.
Definition at line 750 of file LDAP.php.
Field Documentation
◆ $authz_id
|
protected |
◆ $ldap
◆ $timeout
|
protected |
Definition at line 44 of file LDAP.php.
Referenced by __construct().
The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/lib/SimpleSAML/Auth/LDAP.php