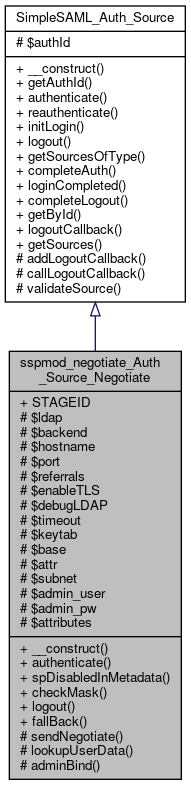
Inheritance diagram for sspmod_negotiate_Auth_Source_Negotiate:
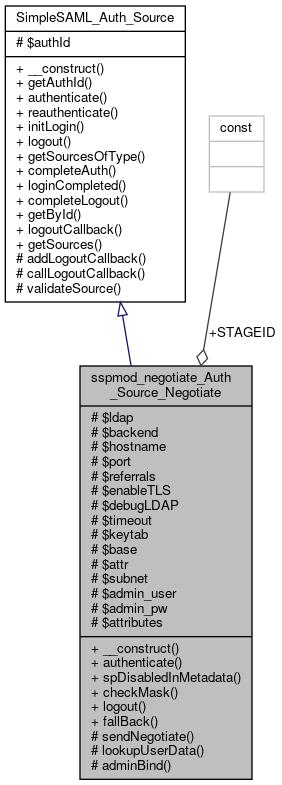
Inheritance diagram for sspmod_negotiate_Auth_Source_Negotiate: Collaboration diagram for sspmod_negotiate_Auth_Source_Negotiate:
Collaboration diagram for sspmod_negotiate_Auth_Source_Negotiate:Public Member Functions | |
| __construct ($info, $config) | |
| Constructor for this authentication source. More... | |
| authenticate (&$state) | |
| The inner workings of the module. More... | |
| spDisabledInMetadata ($spMetadata) | |
| checkMask () | |
| checkMask() looks up the subnet config option and verifies that the client is within that range. More... | |
| logout (&$state) | |
| Log out from this authentication source. More... | |
 Public Member Functions inherited from SimpleSAML_Auth_Source Public Member Functions inherited from SimpleSAML_Auth_Source | |
| __construct ($info, &$config) | |
| Constructor for an authentication source. More... | |
| getAuthId () | |
| Retrieve the ID of this authentication source. More... | |
| authenticate (&$state) | |
| Process a request. More... | |
| reauthenticate (array &$state) | |
| Reauthenticate an user. More... | |
| initLogin ($return, $errorURL=null, array $params=array()) | |
| Start authentication. More... | |
| logout (&$state) | |
| Log out from this authentication source. More... | |
Static Public Member Functions | |
| static | fallBack (&$state) |
| Passes control of the login process to a different module. More... | |
 Static Public Member Functions inherited from SimpleSAML_Auth_Source Static Public Member Functions inherited from SimpleSAML_Auth_Source | |
| static | getSourcesOfType ($type) |
| Get sources of a specific type. More... | |
| static | completeAuth (&$state) |
| Complete authentication. More... | |
| static | loginCompleted ($state) |
| Called when a login operation has finished. More... | |
| static | completeLogout (&$state) |
| Complete logout. More... | |
| static | getById ($authId, $type=null) |
| Retrieve authentication source. More... | |
| static | logoutCallback ($state) |
| Called when the authentication source receives an external logout request. More... | |
| static | getSources () |
| Retrieve list of authentication sources. More... | |
Data Fields | |
| const | STAGEID = 'sspmod_negotiate_Auth_Source_Negotiate.StageId' |
Protected Member Functions | |
| sendNegotiate ($params) | |
| Send the actual headers and body of the 401. More... | |
| lookupUserData ($user) | |
| Strips away the realm of the Kerberos identifier, looks up what attributes to fetch from SP metadata and searches the directory. More... | |
| adminBind () | |
| Elevates the LDAP connection to allow restricted lookups if so configured. More... | |
 Protected Member Functions inherited from SimpleSAML_Auth_Source Protected Member Functions inherited from SimpleSAML_Auth_Source | |
| addLogoutCallback ($assoc, $state) | |
| Add a logout callback association. More... | |
| callLogoutCallback ($assoc) | |
| Call a logout callback based on association. More... | |
Protected Attributes | |
| $ldap = null | |
| $backend = '' | |
| $hostname = '' | |
| $port = 389 | |
| $referrals = true | |
| $enableTLS = false | |
| $debugLDAP = false | |
| $timeout = 30 | |
| $keytab = '' | |
| $base = array() | |
| $attr = 'uid' | |
| $subnet = null | |
| $admin_user = null | |
| $admin_pw = null | |
| $attributes = null | |
 Protected Attributes inherited from SimpleSAML_Auth_Source Protected Attributes inherited from SimpleSAML_Auth_Source | |
| $authId | |
Additional Inherited Members | |
 Static Protected Member Functions inherited from SimpleSAML_Auth_Source Static Protected Member Functions inherited from SimpleSAML_Auth_Source | |
| static | validateSource ($source, $id) |
| Make sure that the first element of an auth source is its identifier. More... | |
Detailed Description
Definition at line 10 of file Negotiate.php.
Constructor & Destructor Documentation
◆ __construct()
| sspmod_negotiate_Auth_Source_Negotiate::__construct | ( | $info, | |
| $config | |||
| ) |
Constructor for this authentication source.
- Parameters
-
array $info Information about this authentication source. array $config The configuration of the module
- Exceptions
-
Exception If the KRB5 extension is not installed or active.
Definition at line 41 of file Negotiate.php.
References $config, $info, base(), and SimpleSAML_Configuration\loadFromArray().
 Here is the call graph for this function:
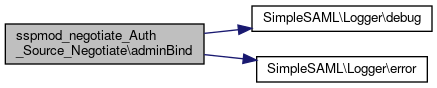
Here is the call graph for this function:Member Function Documentation
◆ adminBind()
|
protected |
Elevates the LDAP connection to allow restricted lookups if so configured.
Does nothing if not.
Definition at line 323 of file Negotiate.php.
References SimpleSAML\Logger\debug(), and SimpleSAML\Logger\error().
Referenced by lookupUserData().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ authenticate()
| sspmod_negotiate_Auth_Source_Negotiate::authenticate | ( | & | $state | ) |
The inner workings of the module.
Checks to see if client is in the defined subnets (if defined in config). Sends the client a 401 Negotiate and responds to the result. If the client fails to provide a proper Kerberos ticket, the login process is handed over to the 'fallback' module defined in the config.
LDAP is used as a user metadata source.
- Parameters
-
array &$state Information about the current authentication.
Reimplemented from SimpleSAML_Auth_Source.
Definition at line 83 of file Negotiate.php.
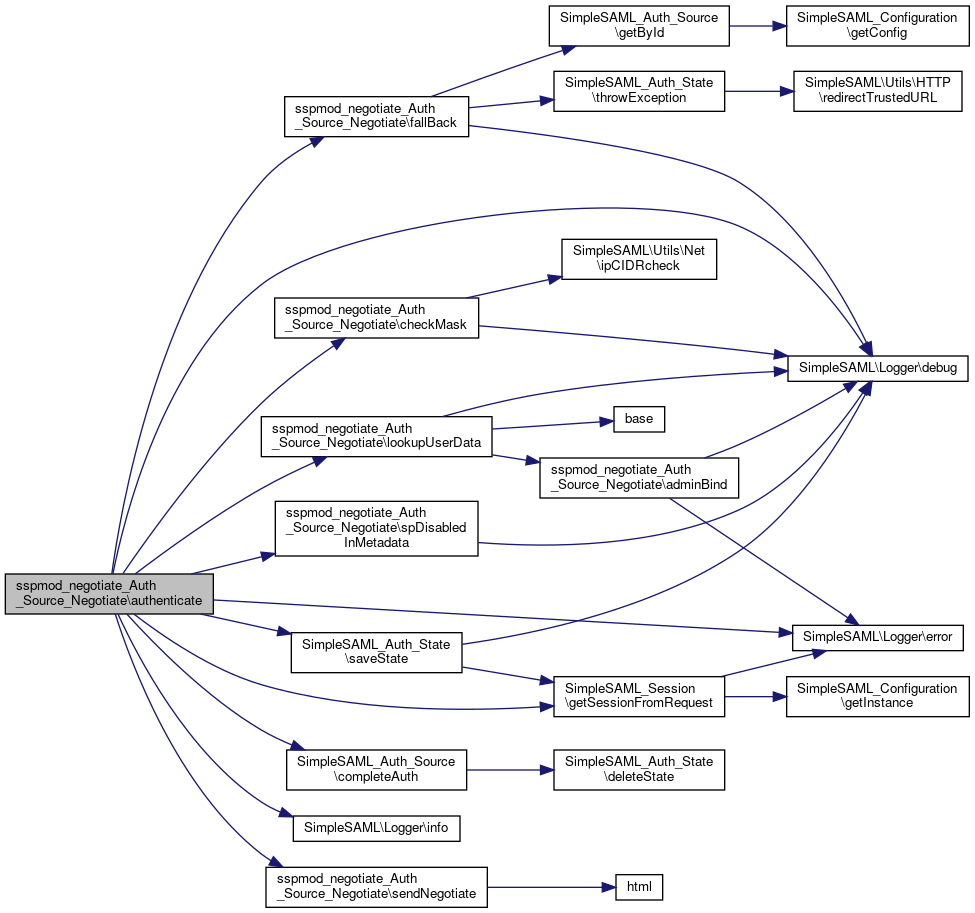
References $_COOKIE, $_SERVER, $auth, SimpleSAML_Auth_Source\$authId, $id, $mask, PHPMailer\PHPMailer\$params, $session, $state, $user, checkMask(), SimpleSAML_Auth_Source\completeAuth(), SimpleSAML\Logger\debug(), SimpleSAML\Logger\error(), exit, fallBack(), SimpleSAML_Session\getSessionFromRequest(), SimpleSAML\Logger\info(), lookupUserData(), SimpleSAML_Auth_State\saveState(), sendNegotiate(), and spDisabledInMetadata().
 Here is the call graph for this function:
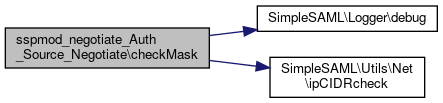
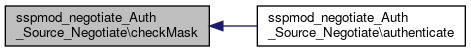
Here is the call graph for this function:◆ checkMask()
| sspmod_negotiate_Auth_Source_Negotiate::checkMask | ( | ) |
checkMask() looks up the subnet config option and verifies that the client is within that range.
Will return TRUE if no subnet option is configured.
- Returns
- boolean
Definition at line 213 of file Negotiate.php.
References $_SERVER, $ret, SimpleSAML\Logger\debug(), and SimpleSAML\Utils\Net\ipCIDRcheck().
Referenced by authenticate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
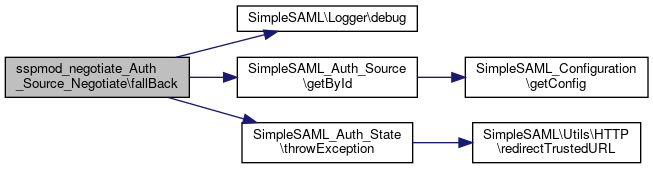
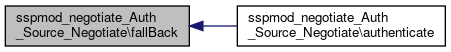
Here is the caller graph for this function:◆ fallBack()
|
static |
Passes control of the login process to a different module.
- Parameters
-
array $state Information about the current authentication.
- Exceptions
-
SimpleSAML_Error_Error If couldn't determine the auth source. SimpleSAML_Error_Exception Exception
Definition at line 268 of file Negotiate.php.
References SimpleSAML_Auth_Source\$authId, $source, $state, SimpleSAML\Logger\debug(), SimpleSAML_Auth_Source\getById(), SimpleSAML_Auth_Source\loginCompleted(), and SimpleSAML_Auth_State\throwException().
Referenced by authenticate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ logout()
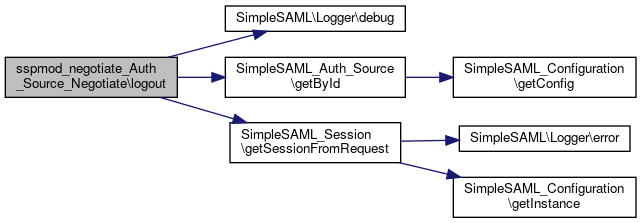
| sspmod_negotiate_Auth_Source_Negotiate::logout | ( | & | $state | ) |
Log out from this authentication source.
This method either logs the user out from Negotiate or passes the logout call to the fallback module.
- Parameters
-
array &$state Information about the current logout operation.
Reimplemented from SimpleSAML_Auth_Source.
Definition at line 349 of file Negotiate.php.
References SimpleSAML_Auth_Source\$authId, $session, $source, $state, SimpleSAML\Logger\debug(), SimpleSAML_Auth_Source\getById(), and SimpleSAML_Session\getSessionFromRequest().
 Here is the call graph for this function:
Here is the call graph for this function:◆ lookupUserData()
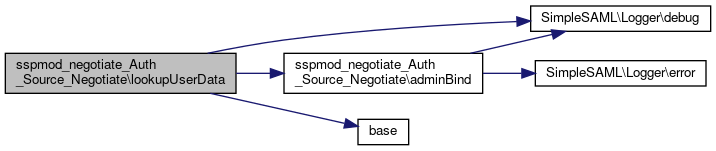
|
protected |
Strips away the realm of the Kerberos identifier, looks up what attributes to fetch from SP metadata and searches the directory.
- Parameters
-
string $user The Kerberos user identifier.
- Returns
- string The DN to the user or NULL if not found.
Definition at line 299 of file Negotiate.php.
References $user, adminBind(), base(), and SimpleSAML\Logger\debug().
Referenced by authenticate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ sendNegotiate()
|
protected |
Send the actual headers and body of the 401.
Embedded in the body is a post that is triggered by JS if the client wants to show the 401 message.
- Parameters
-
array $params additional parameters to the URL in the URL in the body.
Definition at line 238 of file Negotiate.php.
References PHPMailer\PHPMailer\$params, $url, EOF, and html().
Referenced by authenticate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ spDisabledInMetadata()
| sspmod_negotiate_Auth_Source_Negotiate::spDisabledInMetadata | ( | $spMetadata | ) |
Definition at line 189 of file Negotiate.php.
References $spMetadata, and SimpleSAML\Logger\debug().
Referenced by authenticate().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:Field Documentation
◆ $admin_pw
|
protected |
Definition at line 29 of file Negotiate.php.
◆ $admin_user
|
protected |
Definition at line 28 of file Negotiate.php.
◆ $attr
|
protected |
Definition at line 26 of file Negotiate.php.
◆ $attributes
|
protected |
Definition at line 30 of file Negotiate.php.
◆ $backend
|
protected |
Definition at line 17 of file Negotiate.php.
◆ $base
|
protected |
Definition at line 25 of file Negotiate.php.
◆ $debugLDAP
|
protected |
Definition at line 22 of file Negotiate.php.
◆ $enableTLS
|
protected |
Definition at line 21 of file Negotiate.php.
◆ $hostname
|
protected |
Definition at line 18 of file Negotiate.php.
◆ $keytab
|
protected |
Definition at line 24 of file Negotiate.php.
◆ $ldap
|
protected |
Definition at line 16 of file Negotiate.php.
◆ $port
|
protected |
Definition at line 19 of file Negotiate.php.
◆ $referrals
|
protected |
Definition at line 20 of file Negotiate.php.
◆ $subnet
|
protected |
Definition at line 27 of file Negotiate.php.
◆ $timeout
|
protected |
Definition at line 23 of file Negotiate.php.
◆ STAGEID
| const sspmod_negotiate_Auth_Source_Negotiate::STAGEID = 'sspmod_negotiate_Auth_Source_Negotiate.StageId' |
Definition at line 14 of file Negotiate.php.
The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/modules/negotiate/lib/Auth/Source/Negotiate.php