Inheritance diagram for phpseclib\Net\SSH2:
Inheritance diagram for phpseclib\Net\SSH2: Collaboration diagram for phpseclib\Net\SSH2:
Collaboration diagram for phpseclib\Net\SSH2:Public Member Functions | |
| __construct ($host, $port=22, $timeout=10) | |
| Default Constructor. More... | |
| setCryptoEngine ($engine) | |
| Set Crypto Engine Mode. More... | |
| _connect () | |
| Connect to an SSHv2 server. More... | |
| _generate_identifier () | |
| Generates the SSH identifier. More... | |
| _key_exchange ($kexinit_payload_server) | |
| Key Exchange. More... | |
| _encryption_algorithm_to_key_size ($algorithm) | |
| Maps an encryption algorithm name to the number of key bytes. More... | |
| _encryption_algorithm_to_crypt_instance ($algorithm) | |
| Maps an encryption algorithm name to an instance of a subclass of \phpseclib\Crypt\Base. More... | |
| login ($username) | |
| Login. More... | |
| _login ($username) | |
| Login Helper. More... | |
| _login_helper ($username, $password=null) | |
| Login Helper. More... | |
| _keyboard_interactive_login ($username, $password) | |
| Login via keyboard-interactive authentication. More... | |
| _keyboard_interactive_process () | |
| Handle the keyboard-interactive requests / responses. More... | |
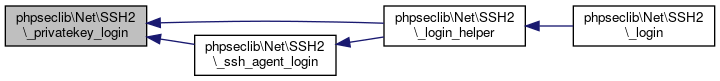
| _ssh_agent_login ($username, $agent) | |
| Login with an ssh-agent provided key. More... | |
| _privatekey_login ($username, $privatekey) | |
| Login with an RSA private key. More... | |
| setTimeout ($timeout) | |
| Set Timeout. More... | |
| getStdError () | |
| Get the output from stdError. More... | |
| exec ($command, $callback=null) | |
| Execute Command. More... | |
| _initShell () | |
| Creates an interactive shell. More... | |
| _get_interactive_channel () | |
| Return the channel to be used with read() / write() More... | |
| _get_open_channel () | |
| Return an available open channel. More... | |
| read ($expect='', $mode=self::READ_SIMPLE) | |
| Returns the output of an interactive shell. More... | |
| write ($cmd) | |
| Inputs a command into an interactive shell. More... | |
| startSubsystem ($subsystem) | |
| Start a subsystem. More... | |
| stopSubsystem () | |
| Stops a subsystem. More... | |
| reset () | |
| Closes a channel. More... | |
| isTimeout () | |
| Is timeout? More... | |
| disconnect () | |
| Disconnect. More... | |
| __destruct () | |
| Destructor. More... | |
| isConnected () | |
| Is the connection still active? More... | |
| isAuthenticated () | |
| Have you successfully been logged in? More... | |
| _get_binary_packet () | |
| Gets Binary Packets. More... | |
| _filter ($payload) | |
| Filter Binary Packets. More... | |
| enableQuietMode () | |
| Enable Quiet Mode. More... | |
| disableQuietMode () | |
| Disable Quiet Mode. More... | |
| isQuietModeEnabled () | |
| Returns whether Quiet Mode is enabled or not. More... | |
| enablePTY () | |
| Enable request-pty when using exec() More... | |
| disablePTY () | |
| Disable request-pty when using exec() More... | |
| isPTYEnabled () | |
| Returns whether request-pty is enabled or not. More... | |
| _get_channel_packet ($client_channel, $skip_extended=false) | |
| Gets channel data. More... | |
| _send_binary_packet ($data, $logged=null) | |
| Sends Binary Packets. More... | |
| _append_log ($message_number, $message) | |
| Logs data packets. More... | |
| _send_channel_packet ($client_channel, $data) | |
| Sends channel data. More... | |
| _close_channel ($client_channel, $want_reply=false) | |
| Closes and flushes a channel. More... | |
| _disconnect ($reason) | |
| Disconnect. More... | |
| _string_shift (&$string, $index=1) | |
| String Shift. More... | |
| _define_array () | |
| Define Array. More... | |
| getLog () | |
| Returns a log of the packets that have been sent and received. More... | |
| _format_log ($message_log, $message_number_log) | |
| Formats a log for printing. More... | |
| _format_log_helper ($matches) | |
| Helper function for _format_log. More... | |
| _on_channel_open () | |
| Helper function for agent->_on_channel_open() More... | |
| _array_intersect_first ($array1, $array2) | |
| Returns the first value of the intersection of two arrays or false if the intersection is empty. More... | |
| getErrors () | |
| Returns all errors. More... | |
| getLastError () | |
| Returns the last error. More... | |
| getServerIdentification () | |
| Return the server identification. More... | |
| getKexAlgorithms () | |
| Return a list of the key exchange algorithms the server supports. More... | |
| getServerHostKeyAlgorithms () | |
| Return a list of the host key (public key) algorithms the server supports. More... | |
| getEncryptionAlgorithmsClient2Server () | |
| Return a list of the (symmetric key) encryption algorithms the server supports, when receiving stuff from the client. More... | |
| getEncryptionAlgorithmsServer2Client () | |
| Return a list of the (symmetric key) encryption algorithms the server supports, when sending stuff to the client. More... | |
| getMACAlgorithmsClient2Server () | |
| Return a list of the MAC algorithms the server supports, when receiving stuff from the client. More... | |
| getMACAlgorithmsServer2Client () | |
| Return a list of the MAC algorithms the server supports, when sending stuff to the client. More... | |
| getCompressionAlgorithmsClient2Server () | |
| Return a list of the compression algorithms the server supports, when receiving stuff from the client. More... | |
| getCompressionAlgorithmsServer2Client () | |
| Return a list of the compression algorithms the server supports, when sending stuff to the client. More... | |
| getLanguagesServer2Client () | |
| Return a list of the languages the server supports, when sending stuff to the client. More... | |
| getLanguagesClient2Server () | |
| Return a list of the languages the server supports, when receiving stuff from the client. More... | |
| getBannerMessage () | |
| Returns the banner message. More... | |
| getServerPublicHostKey () | |
| Returns the server public host key. More... | |
| getExitStatus () | |
| Returns the exit status of an SSH command or false. More... | |
| getWindowColumns () | |
| Returns the number of columns for the terminal window size. More... | |
| getWindowRows () | |
| Returns the number of rows for the terminal window size. More... | |
| setWindowColumns ($value) | |
| Sets the number of columns for the terminal window size. More... | |
| setWindowRows ($value) | |
| Sets the number of rows for the terminal window size. More... | |
| setWindowSize ($columns=80, $rows=24) | |
| Sets the number of columns and rows for the terminal window size. More... | |
Detailed Description
Constructor & Destructor Documentation
◆ __construct()
| phpseclib\Net\SSH2::__construct | ( | $host, | |
$port = 22, |
|||
$timeout = 10 |
|||
| ) |
Default Constructor.
$host can either be a string, representing the host, or a stream resource.
- Parameters
-
mixed $host int $port int $timeout
- See also
- self::login()
- Returns
- \phpseclib\Net\SSH2 @access public
Reimplemented in phpseclib\Net\SFTP.
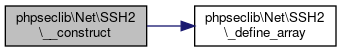
Definition at line 881 of file SSH2.php.
References phpseclib\Net\SSH2\$host, phpseclib\Net\SSH2\$port, phpseclib\Net\SSH2\$timeout, and phpseclib\Net\SSH2\_define_array().
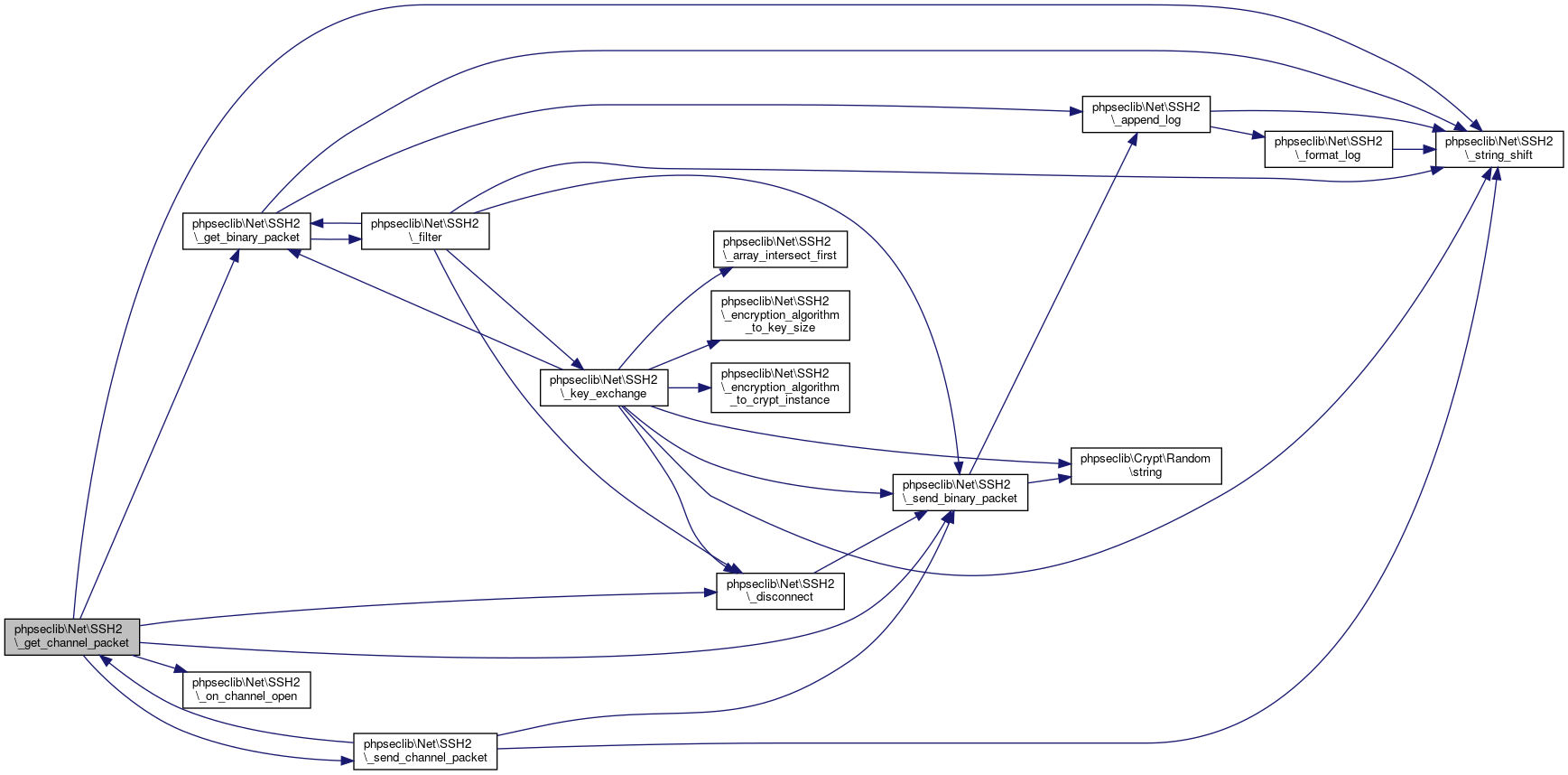
 Here is the call graph for this function:
Here is the call graph for this function:◆ __destruct()
| phpseclib\Net\SSH2::__destruct | ( | ) |
Destructor.
Will be called, automatically, if you're supporting just PHP5. If you're supporting PHP4, you'll need to call disconnect().
@access public
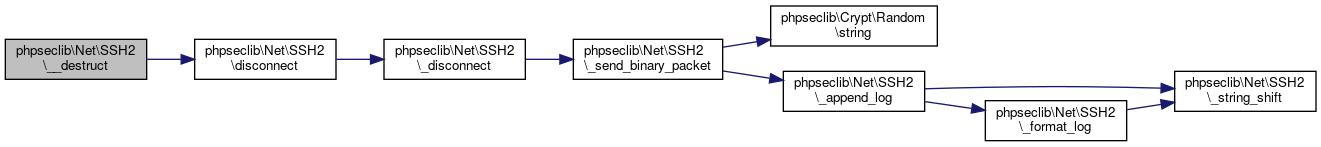
Definition at line 2849 of file SSH2.php.
References phpseclib\Net\SSH2\disconnect().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ _append_log()
| phpseclib\Net\SSH2::_append_log | ( | $message_number, | |
| $message | |||
| ) |
Logs data packets.
Makes sure that only the last 1MB worth of packets will be logged
- Parameters
-
string $data @access private
Definition at line 3451 of file SSH2.php.
References $filename, $message, $start, phpseclib\Net\SSH2\_format_log(), phpseclib\Net\SSH2\_string_shift(), phpseclib\Net\SSH2\LOG_COMPLEX, phpseclib\Net\SSH2\LOG_REALTIME, phpseclib\Net\SSH2\LOG_REALTIME_FILE, and phpseclib\Net\SSH2\LOG_SIMPLE.
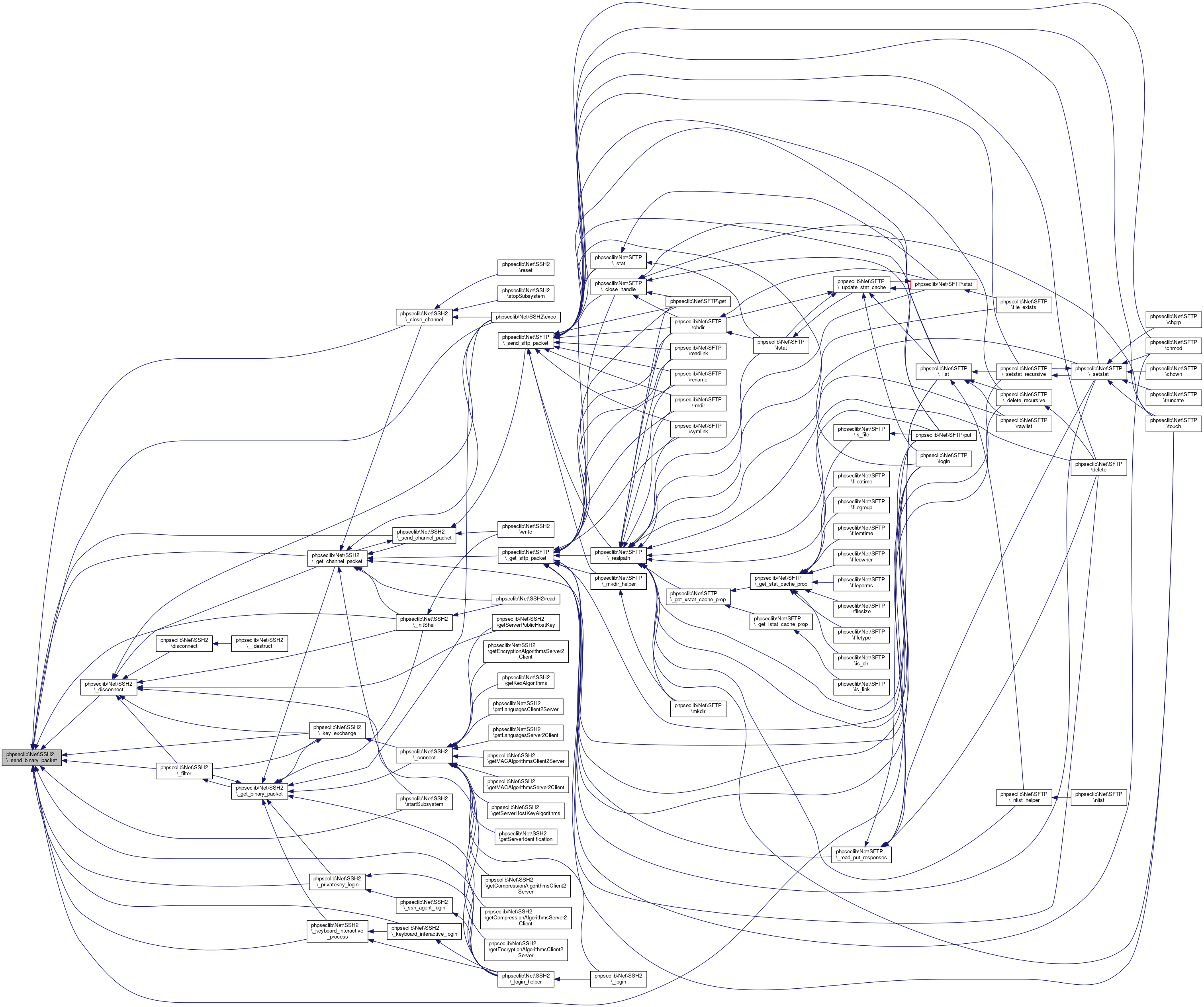
Referenced by phpseclib\Net\SSH2\_connect(), phpseclib\Net\SSH2\_get_binary_packet(), and phpseclib\Net\SSH2\_send_binary_packet().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _array_intersect_first()
| phpseclib\Net\SSH2::_array_intersect_first | ( | $array1, | |
| $array2 | |||
| ) |
Returns the first value of the intersection of two arrays or false if the intersection is empty.
The order is defined by the first parameter.
- Parameters
-
array $array1 array $array2
- Returns
- mixed False if intersection is empty, else intersected value. @access private
Definition at line 3761 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _close_channel()
| phpseclib\Net\SSH2::_close_channel | ( | $client_channel, | |
$want_reply = false |
|||
| ) |
Closes and flushes a channel.
\phpseclib\Net\SSH2 doesn't properly close most channels. For exec() channels are normally closed by the server and for SFTP channels are presumably closed when the client disconnects. This functions is intended for SCP more than anything.
- Parameters
-
int $client_channel bool $want_reply
- Returns
- bool @access private
Definition at line 3577 of file SSH2.php.
References phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_send_binary_packet(), and phpseclib\Net\SSH2\MASK_SHELL.
Referenced by phpseclib\Net\SSH2\exec(), phpseclib\Net\SSH2\reset(), and phpseclib\Net\SSH2\stopSubsystem().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _connect()
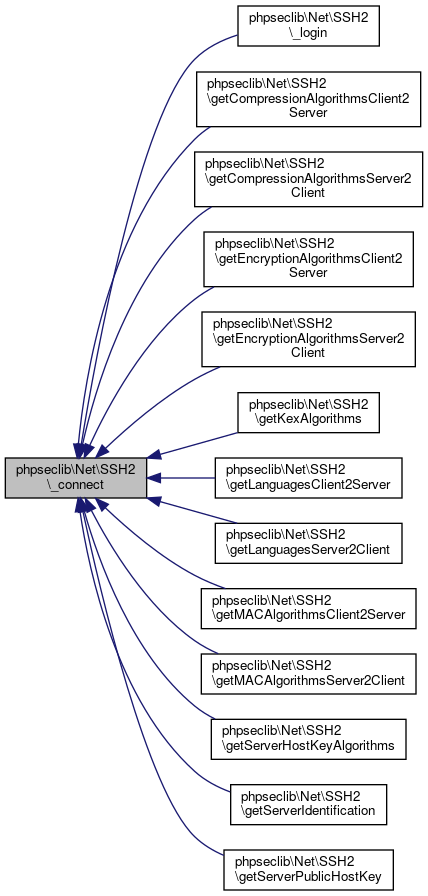
| phpseclib\Net\SSH2::_connect | ( | ) |
Connect to an SSHv2 server.
- Returns
- bool @access private
Definition at line 994 of file SSH2.php.
References phpseclib\Net\SSH2\$host, phpseclib\Net\SSH2\$port, $response, $start, phpseclib\Net\SSH2\$timeout, phpseclib\Net\SSH2\_append_log(), phpseclib\Net\SSH2\_generate_identifier(), phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_key_exchange(), phpseclib\Net\SSH2\MASK_CONNECTED, and phpseclib\Net\SSH2\MASK_CONSTRUCTOR.
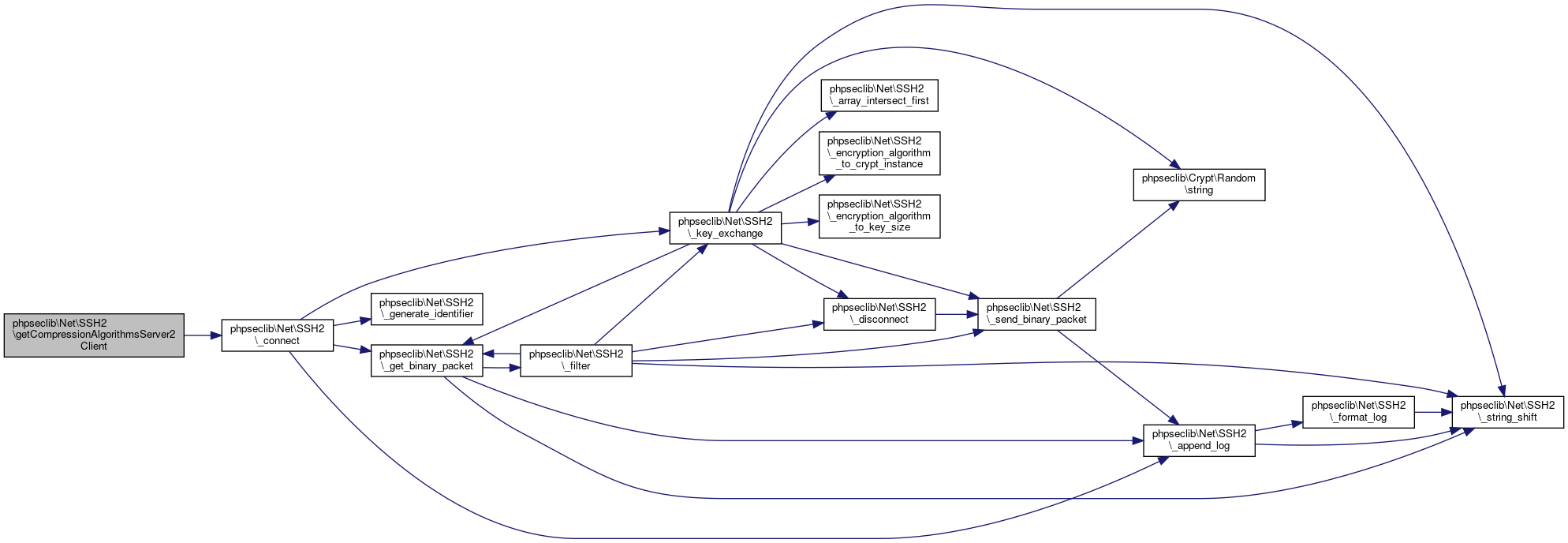
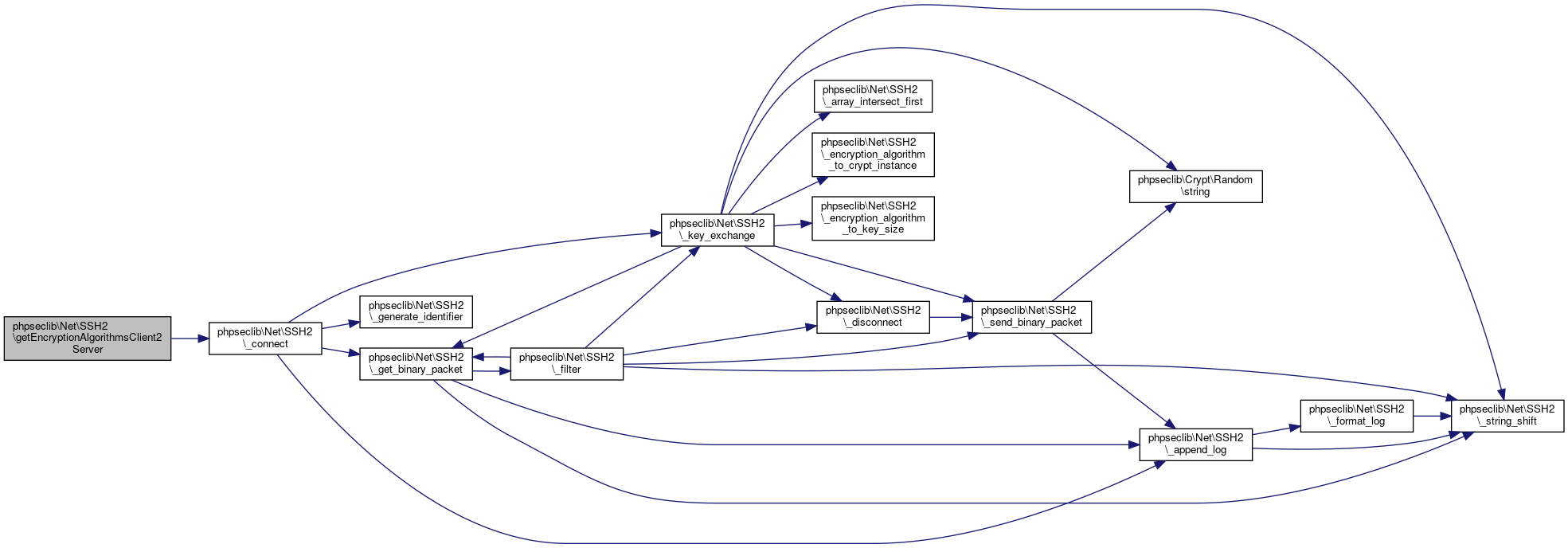
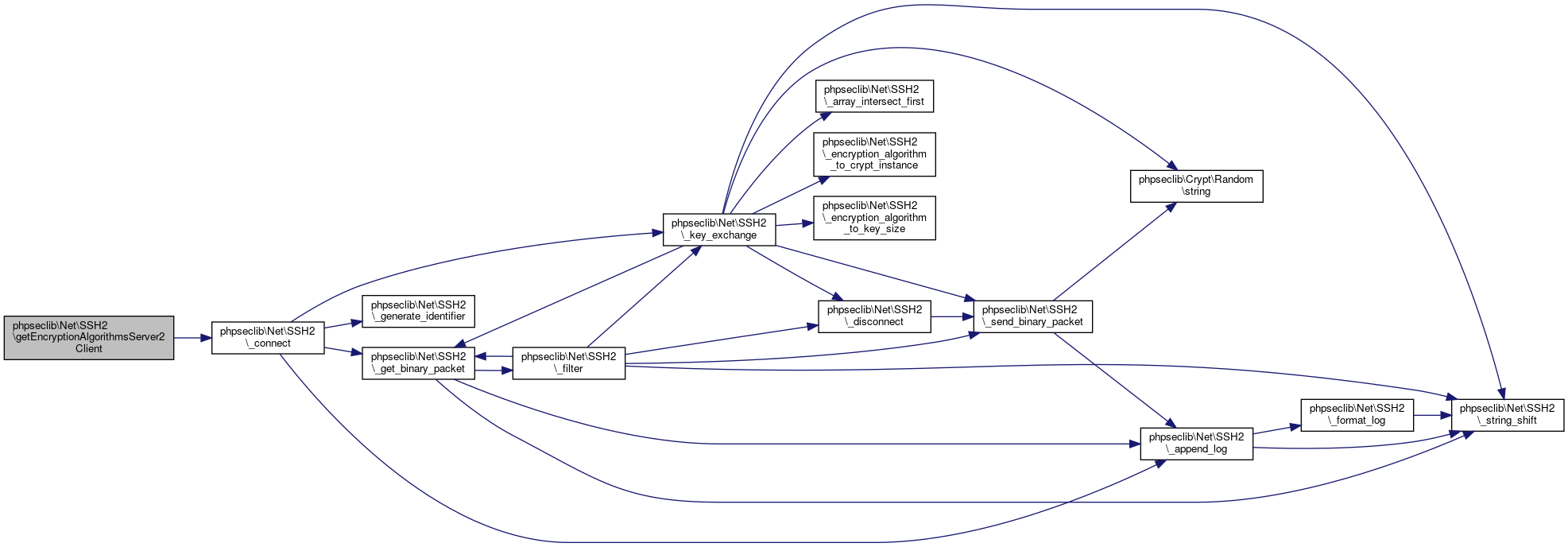
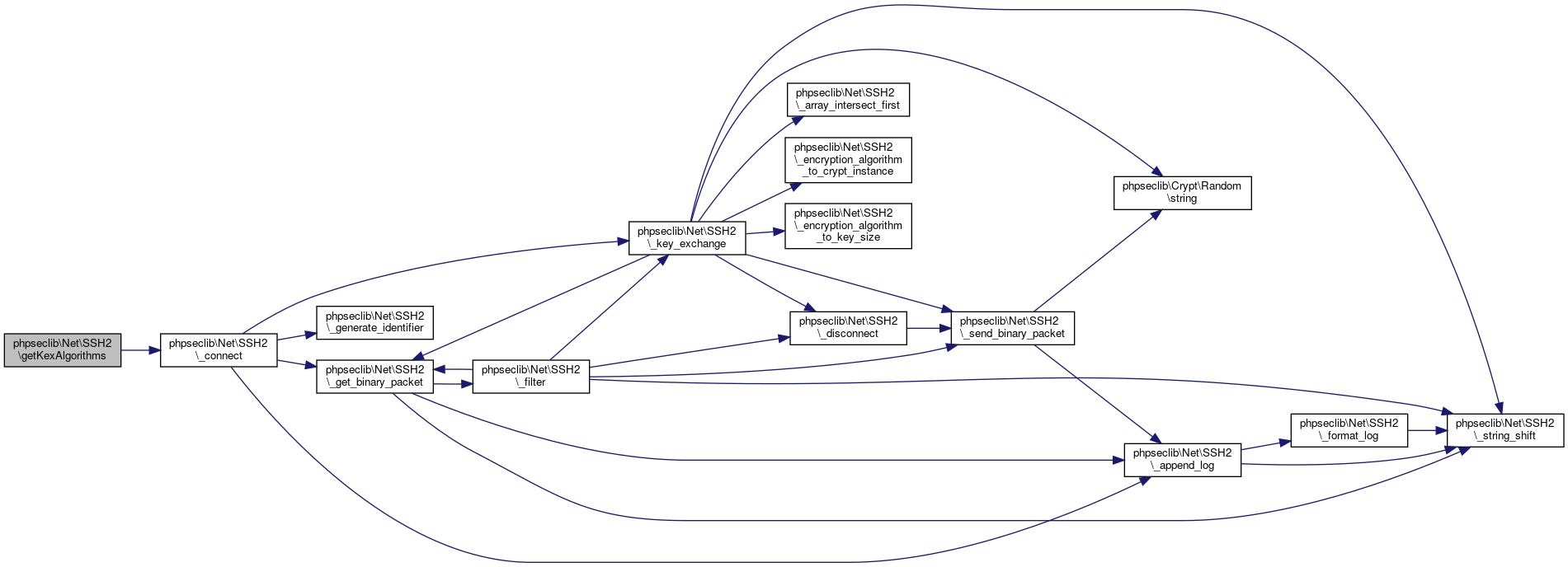
Referenced by phpseclib\Net\SSH2\_login(), phpseclib\Net\SSH2\getCompressionAlgorithmsClient2Server(), phpseclib\Net\SSH2\getCompressionAlgorithmsServer2Client(), phpseclib\Net\SSH2\getEncryptionAlgorithmsClient2Server(), phpseclib\Net\SSH2\getEncryptionAlgorithmsServer2Client(), phpseclib\Net\SSH2\getKexAlgorithms(), phpseclib\Net\SSH2\getLanguagesClient2Server(), phpseclib\Net\SSH2\getLanguagesServer2Client(), phpseclib\Net\SSH2\getMACAlgorithmsClient2Server(), phpseclib\Net\SSH2\getMACAlgorithmsServer2Client(), phpseclib\Net\SSH2\getServerHostKeyAlgorithms(), phpseclib\Net\SSH2\getServerIdentification(), and phpseclib\Net\SSH2\getServerPublicHostKey().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
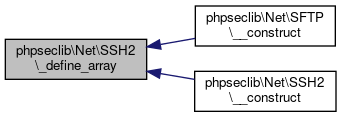
Here is the caller graph for this function:◆ _define_array()
| phpseclib\Net\SSH2::_define_array | ( | ) |
Define Array.
Takes any number of arrays whose indices are integers and whose values are strings and defines a bunch of named constants from it, using the value as the name of the constant and the index as the value of the constant. If any of the constants that would be defined already exists, none of the constants will be defined.
- Parameters
-
array $array @access private
Definition at line 3648 of file SSH2.php.
References $key.
Referenced by phpseclib\Net\SFTP\__construct(), and phpseclib\Net\SSH2\__construct().
 Here is the caller graph for this function:
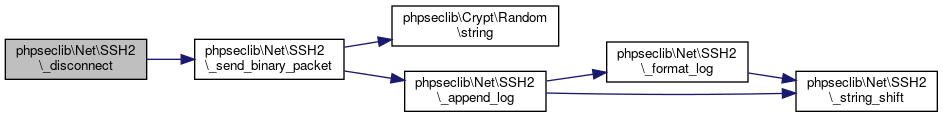
Here is the caller graph for this function:◆ _disconnect()
| phpseclib\Net\SSH2::_disconnect | ( | $reason | ) |
Disconnect.
- Parameters
-
int $reason
- Returns
- bool @access private
Reimplemented in phpseclib\Net\SFTP.
Definition at line 3610 of file SSH2.php.
References $data, and phpseclib\Net\SSH2\_send_binary_packet().
Referenced by phpseclib\Net\SSH2\_filter(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_initShell(), phpseclib\Net\SSH2\_key_exchange(), phpseclib\Net\SSH2\_login_helper(), phpseclib\Net\SSH2\disconnect(), phpseclib\Net\SSH2\exec(), and phpseclib\Net\SSH2\getServerPublicHostKey().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
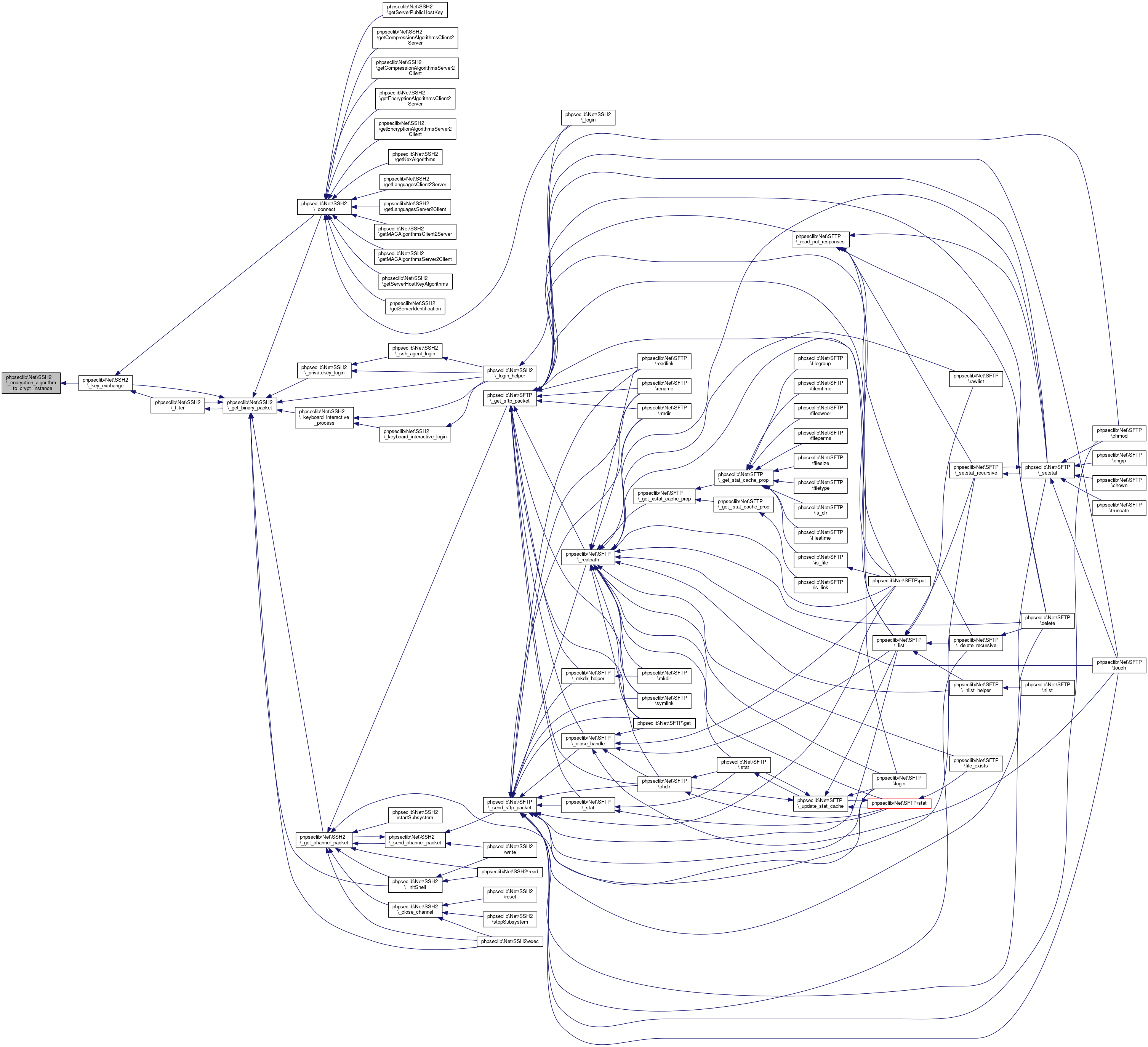
Here is the caller graph for this function:◆ _encryption_algorithm_to_crypt_instance()
| phpseclib\Net\SSH2::_encryption_algorithm_to_crypt_instance | ( | $algorithm | ) |
Maps an encryption algorithm name to an instance of a subclass of \phpseclib\Crypt\Base.
- Parameters
-
string $algorithm Name of the encryption algorithm
- Returns
- mixed Instance of \phpseclib\Crypt\Base or null for unknown @access private
Definition at line 1803 of file SSH2.php.
References phpseclib\Crypt\Base\MODE_CTR.
Referenced by phpseclib\Net\SSH2\_key_exchange().
 Here is the caller graph for this function:
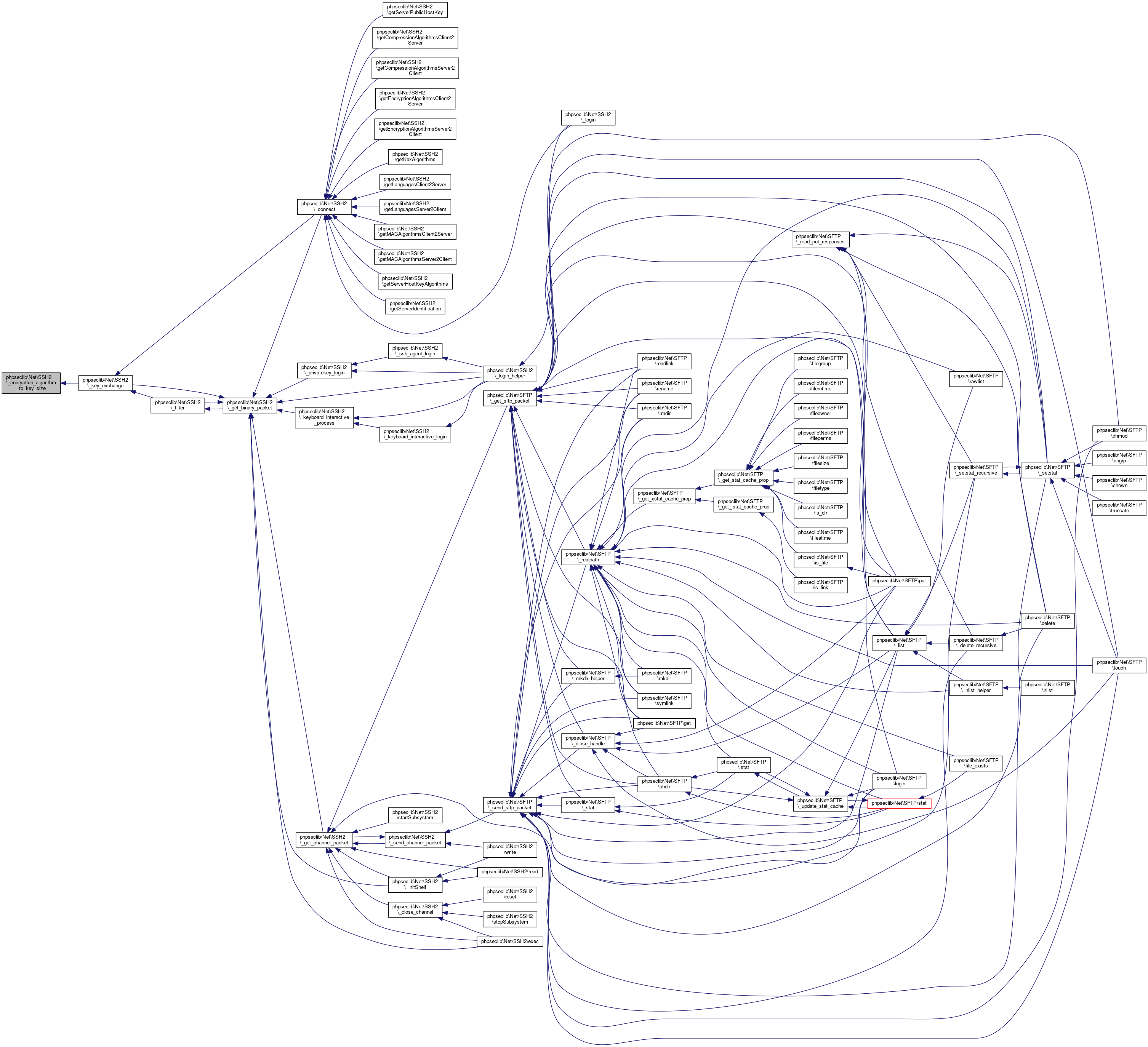
Here is the caller graph for this function:◆ _encryption_algorithm_to_key_size()
| phpseclib\Net\SSH2::_encryption_algorithm_to_key_size | ( | $algorithm | ) |
Maps an encryption algorithm name to the number of key bytes.
- Parameters
-
string $algorithm Name of the encryption algorithm
- Returns
- int|null Number of bytes as an integer or null for unknown @access private
Definition at line 1763 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange().
 Here is the caller graph for this function:
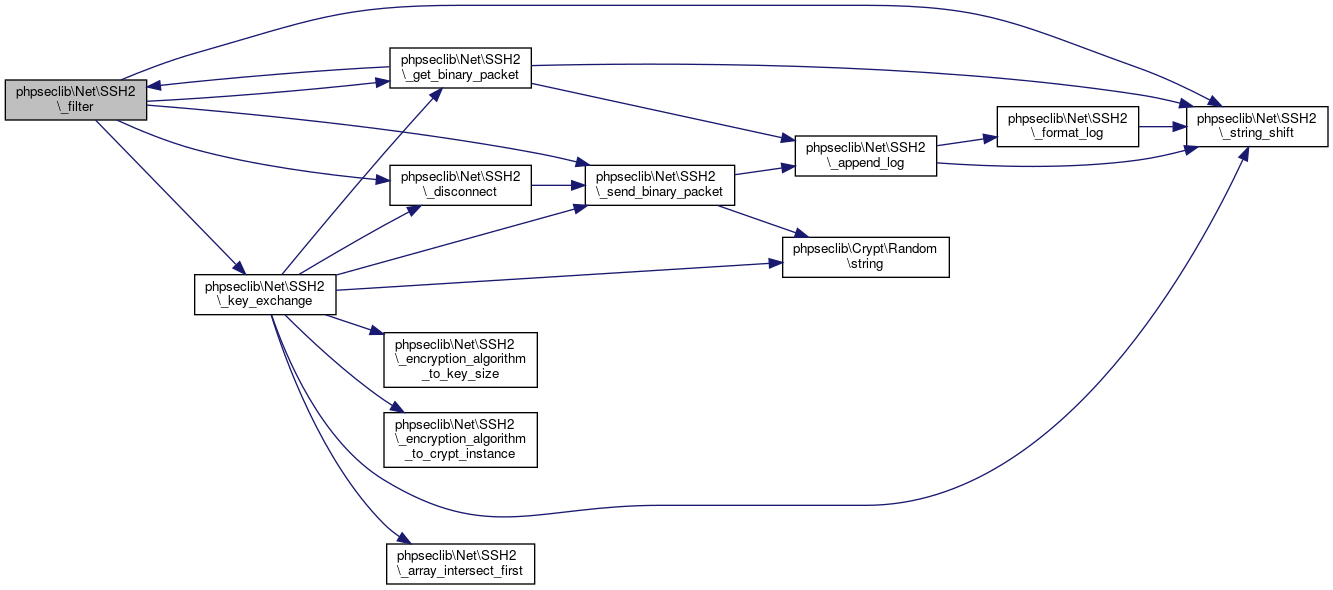
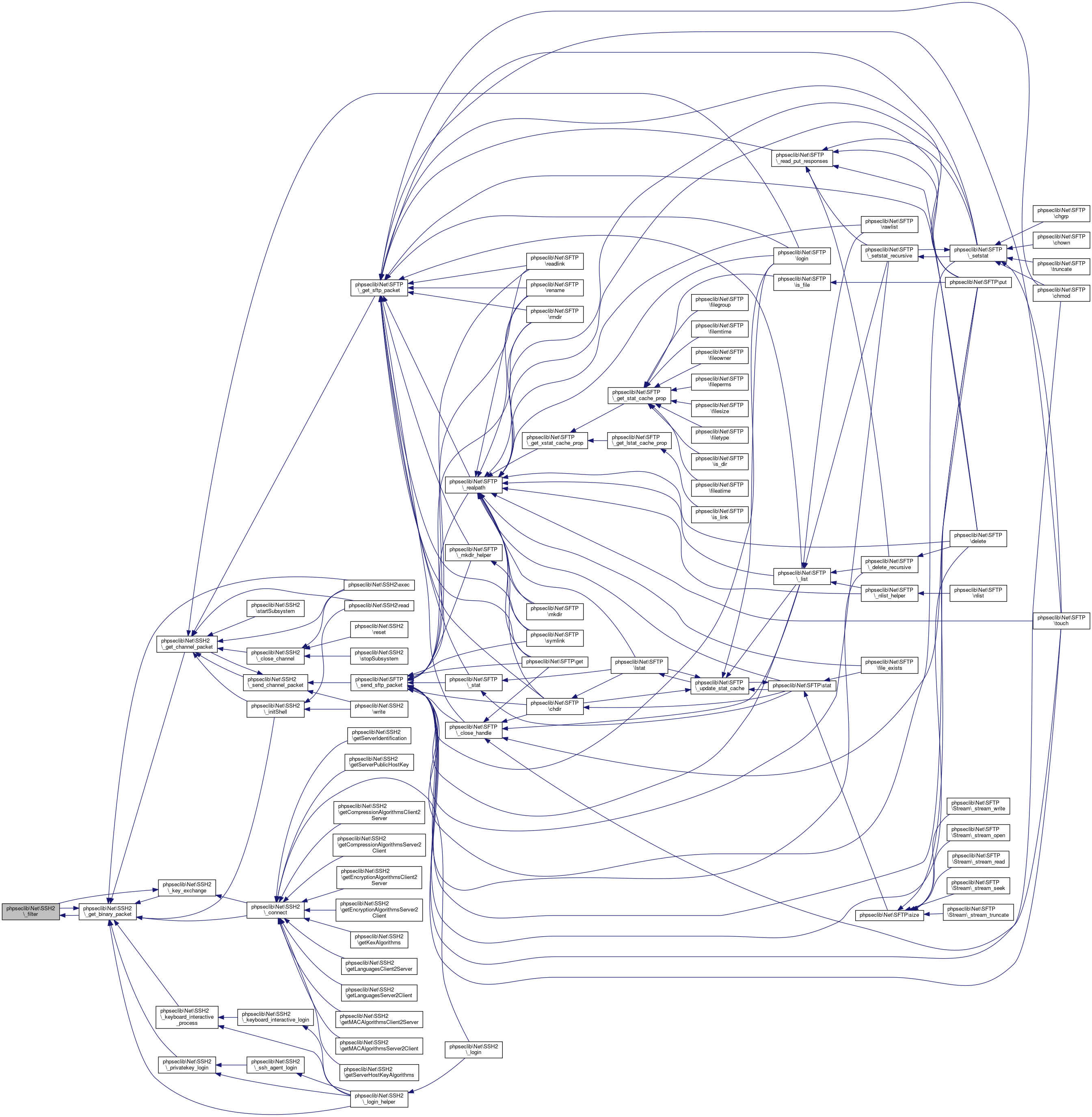
Here is the caller graph for this function:◆ _filter()
| phpseclib\Net\SSH2::_filter | ( | $payload | ) |
Filter Binary Packets.
Because some binary packets need to be ignored...
- See also
- self::_get_binary_packet()
- Returns
- string @access private
Definition at line 2978 of file SSH2.php.
References $data, phpseclib\Net\SSH2\$window_size, phpseclib\Net\SSH2\_disconnect(), phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_key_exchange(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\_string_shift(), phpseclib\Net\SSH2\CHANNEL_AGENT_FORWARD, and phpseclib\Net\SSH2\MASK_WINDOW_ADJUST.
Referenced by phpseclib\Net\SSH2\_get_binary_packet().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _format_log()
| phpseclib\Net\SSH2::_format_log | ( | $message_log, | |
| $message_number_log | |||
| ) |
Formats a log for printing.
- Parameters
-
array $message_log array $message_number_log @access private
- Returns
- string
Definition at line 3696 of file SSH2.php.
References $i, phpseclib\Net\SSH2\$message_log, phpseclib\Net\SSH2\$message_number_log, Sabre\VObject\$output, and phpseclib\Net\SSH2\_string_shift().
Referenced by phpseclib\Net\SSH2\_append_log(), and phpseclib\Net\SSH2\getLog().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _format_log_helper()
| phpseclib\Net\SSH2::_format_log_helper | ( | $matches | ) |
◆ _generate_identifier()
| phpseclib\Net\SSH2::_generate_identifier | ( | ) |
Generates the SSH identifier.
You should overwrite this method in your own class if you want to use another identifier
@access protected
- Returns
- string
Definition at line 1114 of file SSH2.php.
References phpseclib\Net\SSH2\$identifier.
Referenced by phpseclib\Net\SSH2\_connect().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _get_binary_packet()
| phpseclib\Net\SSH2::_get_binary_packet | ( | ) |
Gets Binary Packets.
See '6. Binary Packet Protocol' of rfc4253 for more info.
- See also
- self::_send_binary_packet()
- Returns
- string @access private
Definition at line 2885 of file SSH2.php.
References $current, phpseclib\Net\SSH2\$decrypt_block_size, $start, phpseclib\Net\SSH2\_append_log(), phpseclib\Net\SSH2\_filter(), and phpseclib\Net\SSH2\_string_shift().
Referenced by phpseclib\Net\SSH2\_connect(), phpseclib\Net\SSH2\_filter(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_initShell(), phpseclib\Net\SSH2\_key_exchange(), phpseclib\Net\SSH2\_keyboard_interactive_process(), phpseclib\Net\SSH2\_login_helper(), phpseclib\Net\SSH2\_privatekey_login(), and phpseclib\Net\SSH2\exec().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _get_channel_packet()
| phpseclib\Net\SSH2::_get_channel_packet | ( | $client_channel, | |
$skip_extended = false |
|||
| ) |
Gets channel data.
Returns the data as a string if it's available and false if not.
- Parameters
-
$client_channel
- Returns
- mixed @access private
Definition at line 3175 of file SSH2.php.
References $data, phpseclib\Net\SSH2\$exit_status, $response, $result, $start, $type, phpseclib\Net\SSH2\$window_size, phpseclib\Net\SSH2\_disconnect(), phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_on_channel_open(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\_send_channel_packet(), phpseclib\Net\SSH2\_string_shift(), and phpseclib\Net\SSH2\MASK_SHELL.
Referenced by phpseclib\Net\SSH2\_close_channel(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_initShell(), phpseclib\Net\SSH2\_send_channel_packet(), phpseclib\Net\SSH2\exec(), phpseclib\Net\SFTP\login(), phpseclib\Net\SSH2\read(), and phpseclib\Net\SSH2\startSubsystem().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _get_interactive_channel()
| phpseclib\Net\SSH2::_get_interactive_channel | ( | ) |
Return the channel to be used with read() / write()
- See also
- self::read()
- self::write()
- Returns
- int @access public
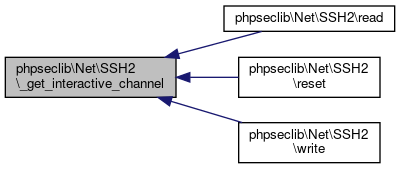
Definition at line 2619 of file SSH2.php.
References phpseclib\Net\SSH2\CHANNEL_EXEC, phpseclib\Net\SSH2\CHANNEL_SHELL, and phpseclib\Net\SSH2\CHANNEL_SUBSYSTEM.
Referenced by phpseclib\Net\SSH2\read(), phpseclib\Net\SSH2\reset(), and phpseclib\Net\SSH2\write().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _get_open_channel()
| phpseclib\Net\SSH2::_get_open_channel | ( | ) |
Return an available open channel.
- Returns
- int @access public
Definition at line 2637 of file SSH2.php.
References phpseclib\Net\SSH2\CHANNEL_EXEC.
◆ _initShell()
| phpseclib\Net\SSH2::_initShell | ( | ) |
Creates an interactive shell.
- See also
- self::read()
- self::write()
- Returns
- bool @access private
Definition at line 2515 of file SSH2.php.
References $response, phpseclib\Net\SSH2\$terminal_modes, $type, phpseclib\Net\SSH2\$window_size, phpseclib\Net\SSH2\_disconnect(), phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\_string_shift(), phpseclib\Net\SSH2\CHANNEL_SHELL, and phpseclib\Net\SSH2\MASK_SHELL.
Referenced by phpseclib\Net\SSH2\read(), and phpseclib\Net\SSH2\write().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _key_exchange()
| phpseclib\Net\SSH2::_key_exchange | ( | $kexinit_payload_server | ) |
Key Exchange.
- Parameters
-
string $kexinit_payload_server @access private
Definition at line 1148 of file SSH2.php.
References phpseclib\Net\SSH2\$compression_algorithms_client_to_server, phpseclib\Net\SSH2\$compression_algorithms_server_to_client, $data, phpseclib\Net\SSH2\$decrypt, phpseclib\Net\SSH2\$encrypt, phpseclib\Net\SSH2\$encryption_algorithms_client_to_server, phpseclib\Net\SSH2\$encryption_algorithms_server_to_client, phpseclib\Net\SSH2\$exchange_hash, $f, phpseclib\Net\SSH2\$kex_algorithms, $key, phpseclib\Net\SSH2\$mac_algorithms_client_to_server, phpseclib\Net\SSH2\$mac_algorithms_server_to_client, $response, phpseclib\Net\SSH2\$server_host_key_algorithms, phpseclib\Net\SSH2\$server_public_host_key, $type, $x, phpseclib\Net\SSH2\_array_intersect_first(), phpseclib\Net\SSH2\_disconnect(), phpseclib\Net\SSH2\_encryption_algorithm_to_crypt_instance(), phpseclib\Net\SSH2\_encryption_algorithm_to_key_size(), phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\_string_shift(), and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Net\SSH2\_connect(), and phpseclib\Net\SSH2\_filter().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _keyboard_interactive_login()
| phpseclib\Net\SSH2::_keyboard_interactive_login | ( | $username, | |
| $password | |||
| ) |
Login via keyboard-interactive authentication.
See RFC4256 for details. This is not a full-featured keyboard-interactive authenticator.
- Parameters
-
string $username string $password
- Returns
- bool @access private
Definition at line 2070 of file SSH2.php.
References $password, phpseclib\Net\SSH2\_keyboard_interactive_process(), and phpseclib\Net\SSH2\_send_binary_packet().
Referenced by phpseclib\Net\SSH2\_login_helper().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _keyboard_interactive_process()
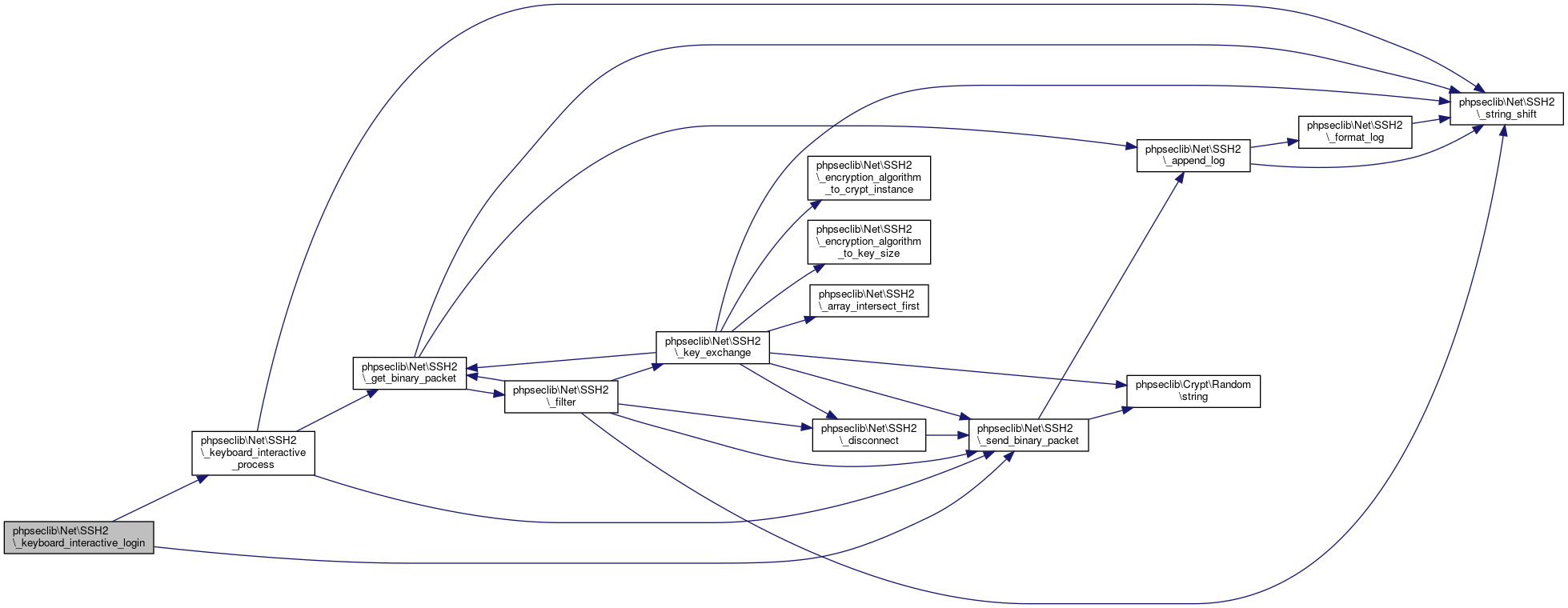
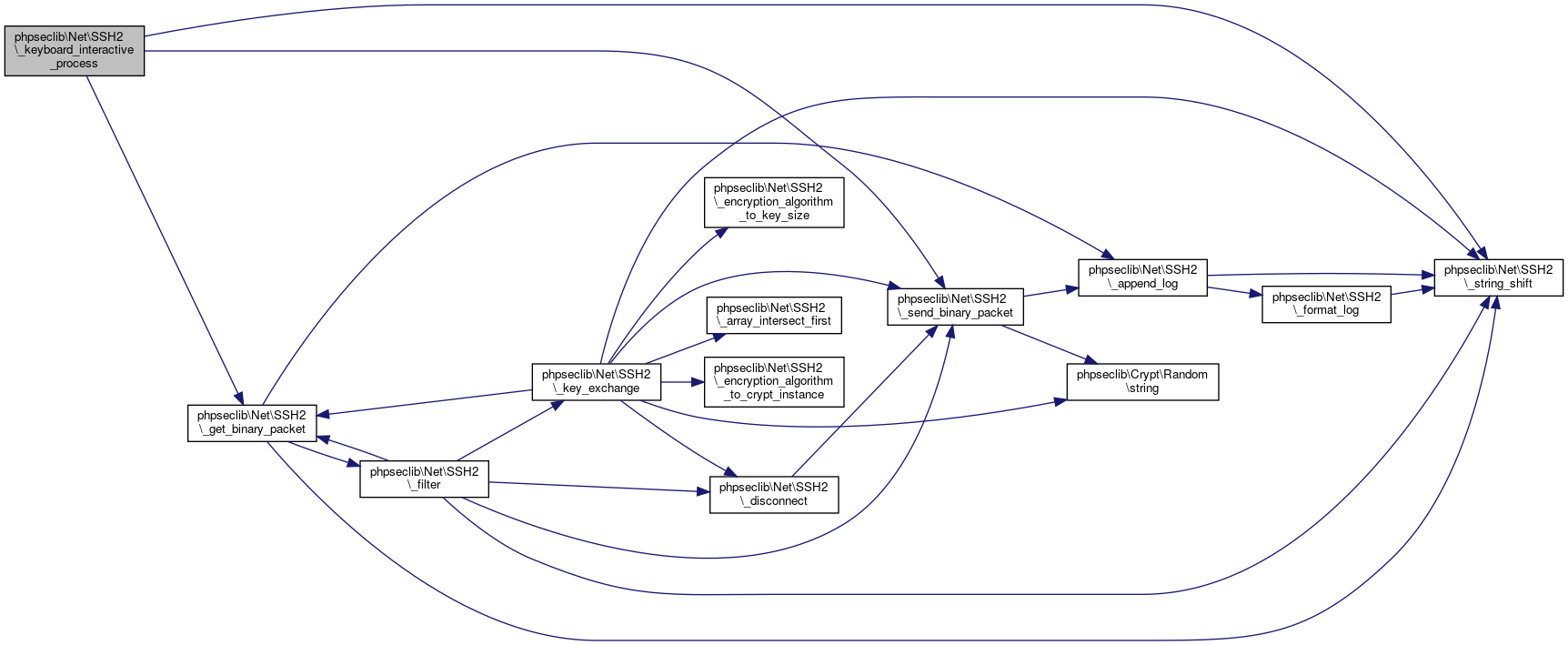
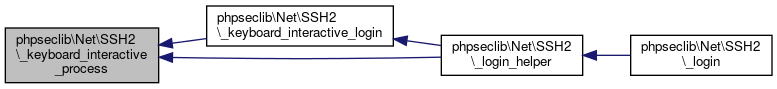
| phpseclib\Net\SSH2::_keyboard_interactive_process | ( | ) |
Handle the keyboard-interactive requests / responses.
- Parameters
-
string $responses,...
- Returns
- bool @access private
Definition at line 2101 of file SSH2.php.
References $i, $key, phpseclib\Net\SSH2\$last_interactive_response, $response, $type, phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_keyboard_interactive_process(), phpseclib\Net\SSH2\_send_binary_packet(), and phpseclib\Net\SSH2\_string_shift().
Referenced by phpseclib\Net\SSH2\_keyboard_interactive_login(), phpseclib\Net\SSH2\_keyboard_interactive_process(), and phpseclib\Net\SSH2\_login_helper().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _login()
| phpseclib\Net\SSH2::_login | ( | $username | ) |
Login Helper.
- Parameters
-
string $username mixed $password mixed $...
- Returns
- bool
- See also
- self::_login_helper() @access private
Definition at line 1867 of file SSH2.php.
References phpseclib\Net\SSH2\_connect(), and phpseclib\Net\SSH2\_login_helper().
 Here is the call graph for this function:
Here is the call graph for this function:◆ _login_helper()
| phpseclib\Net\SSH2::_login_helper | ( | $username, | |
$password = null |
|||
| ) |
Login Helper.
- Parameters
-
string $username string $password
- Returns
- bool @access private
Definition at line 1898 of file SSH2.php.
References $password, $response, $type, phpseclib\Net\SSH2\_disconnect(), phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_keyboard_interactive_login(), phpseclib\Net\SSH2\_keyboard_interactive_process(), phpseclib\Net\SSH2\_privatekey_login(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\_ssh_agent_login(), phpseclib\Net\SSH2\_string_shift(), phpseclib\Net\SSH2\MASK_LOGIN, and phpseclib\Net\SSH2\MASK_LOGIN_REQ.
Referenced by phpseclib\Net\SSH2\_login().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _on_channel_open()
| phpseclib\Net\SSH2::_on_channel_open | ( | ) |
Helper function for agent->_on_channel_open()
Used when channels are created to inform agent of said channel opening. Must be called after channel open confirmation received
@access private
Definition at line 3745 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_get_channel_packet().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _privatekey_login()
| phpseclib\Net\SSH2::_privatekey_login | ( | $username, | |
| $privatekey | |||
| ) |
Login with an RSA private key.
- Parameters
-
string $username \phpseclib\Crypt\RSA $password
- Returns
- bool @access private
Definition at line 2239 of file SSH2.php.
References $response, phpseclib\Net\SSH2\$signature, $type, phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\_string_shift(), phpseclib\Net\SSH2\MASK_LOGIN, phpseclib\Crypt\RSA\PUBLIC_FORMAT_RAW, and phpseclib\Crypt\RSA\SIGNATURE_PKCS1.
Referenced by phpseclib\Net\SSH2\_login_helper(), and phpseclib\Net\SSH2\_ssh_agent_login().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _send_binary_packet()
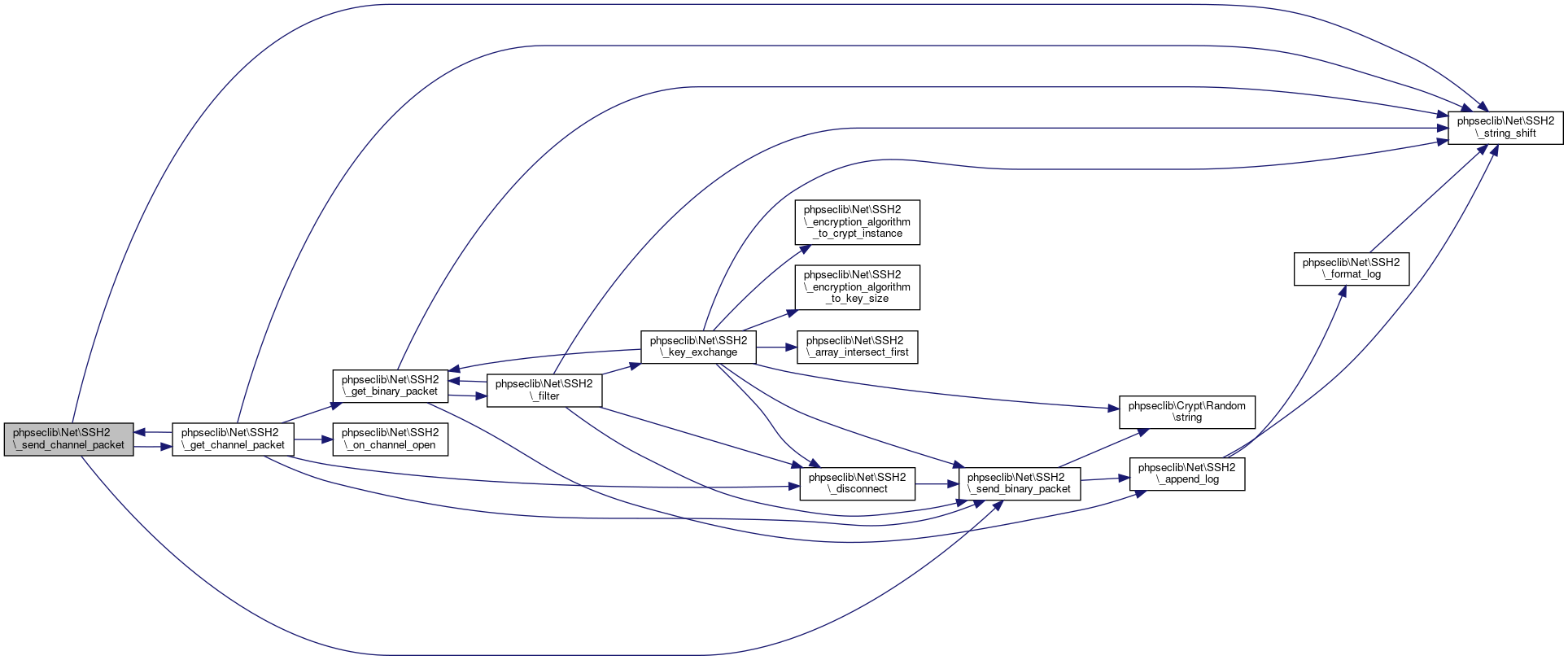
| phpseclib\Net\SSH2::_send_binary_packet | ( | $data, | |
$logged = null |
|||
| ) |
Sends Binary Packets.
See '6. Binary Packet Protocol' of rfc4253 for more info.
- Parameters
-
string $data string $logged
- See also
- self::_get_binary_packet()
- Returns
- bool @access private
Definition at line 3393 of file SSH2.php.
References $current, $data, phpseclib\Net\SSH2\$encrypt_block_size, $result, $start, phpseclib\Net\SSH2\_append_log(), and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Net\SSH2\_close_channel(), phpseclib\Net\SSH2\_disconnect(), phpseclib\Net\SSH2\_filter(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_initShell(), phpseclib\Net\SSH2\_key_exchange(), phpseclib\Net\SSH2\_keyboard_interactive_login(), phpseclib\Net\SSH2\_keyboard_interactive_process(), phpseclib\Net\SSH2\_login_helper(), phpseclib\Net\SSH2\_privatekey_login(), phpseclib\Net\SSH2\_send_channel_packet(), phpseclib\Net\SSH2\exec(), phpseclib\Net\SFTP\login(), and phpseclib\Net\SSH2\startSubsystem().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _send_channel_packet()
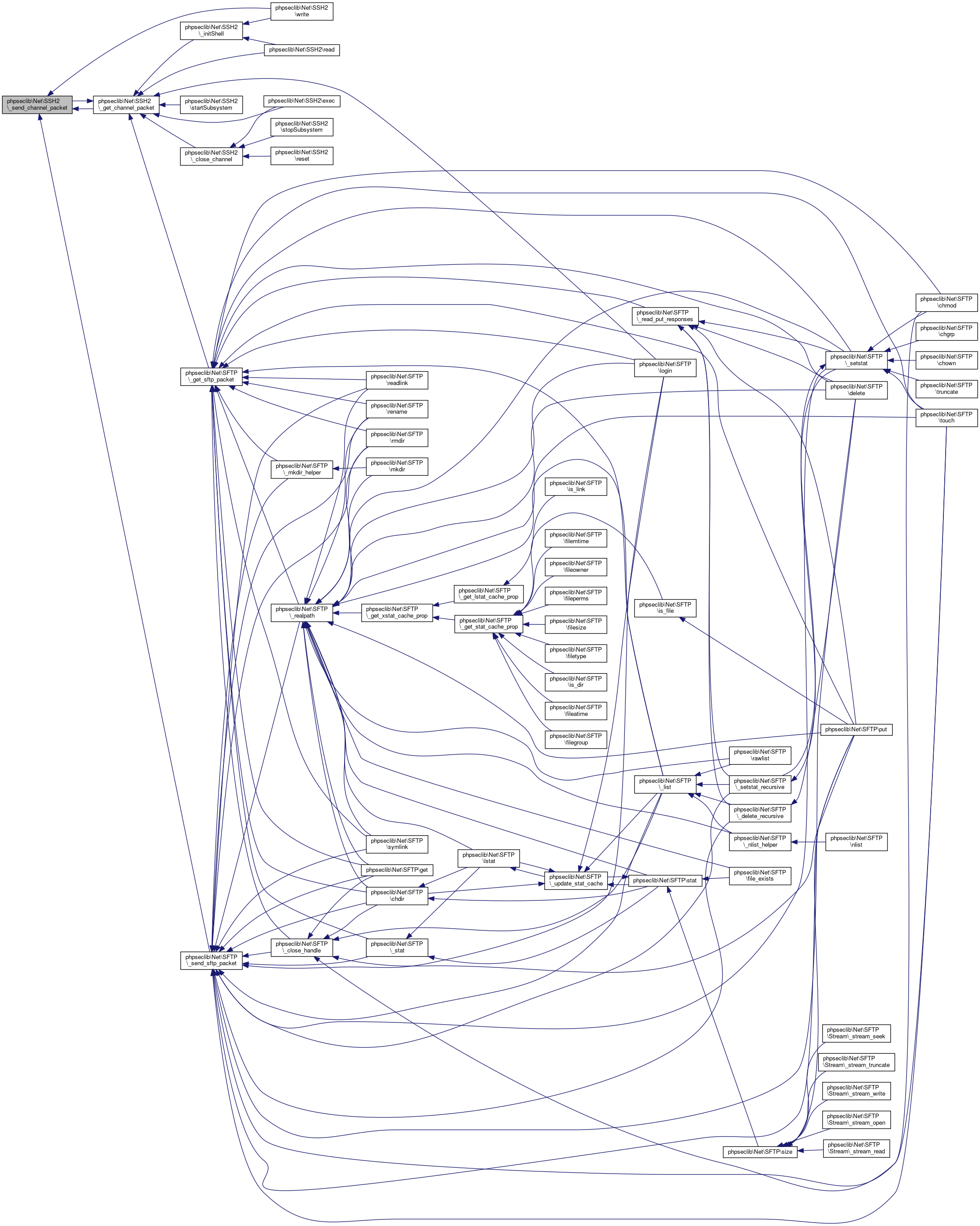
| phpseclib\Net\SSH2::_send_channel_packet | ( | $client_channel, | |
| $data | |||
| ) |
Sends channel data.
Spans multiple SSH_MSG_CHANNEL_DATAs if appropriate
- Parameters
-
int $client_channel string $data
- Returns
- bool @access private
Definition at line 3529 of file SSH2.php.
References $data, phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\_string_shift(), and phpseclib\Net\SSH2\MASK_WINDOW_ADJUST.
Referenced by phpseclib\Net\SSH2\_get_channel_packet(), and phpseclib\Net\SSH2\write().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _ssh_agent_login()
| phpseclib\Net\SSH2::_ssh_agent_login | ( | $username, | |
| $agent | |||
| ) |
Login with an ssh-agent provided key.
- Parameters
-
string $username \phpseclib\System\SSH\Agent $agent
- Returns
- bool @access private
Definition at line 2216 of file SSH2.php.
References phpseclib\Net\SSH2\$agent, $key, $keys, and phpseclib\Net\SSH2\_privatekey_login().
Referenced by phpseclib\Net\SSH2\_login_helper().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _string_shift()
| phpseclib\Net\SSH2::_string_shift | ( | & | $string, |
$index = 1 |
|||
| ) |
String Shift.
Inspired by array_shift
- Parameters
-
string $string int $index
- Returns
- string @access private
Definition at line 3631 of file SSH2.php.
References $index.
Referenced by phpseclib\Net\SSH2\_append_log(), phpseclib\Net\SFTP\_close_handle(), phpseclib\Net\SSH2\_filter(), phpseclib\Net\SSH2\_format_log(), phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_initShell(), phpseclib\Net\SSH2\_key_exchange(), phpseclib\Net\SSH2\_keyboard_interactive_process(), phpseclib\Net\SFTP\_list(), phpseclib\Net\SFTP\_logError(), phpseclib\Net\SSH2\_login_helper(), phpseclib\Net\SFTP\_mkdir_helper(), phpseclib\Net\SSH2\_privatekey_login(), phpseclib\Net\SFTP\_read_put_responses(), phpseclib\Net\SFTP\_realpath(), phpseclib\Net\SSH2\_send_channel_packet(), phpseclib\Net\SFTP\_setstat(), phpseclib\Net\SFTP\delete(), phpseclib\Net\SSH2\exec(), phpseclib\Net\SSH2\getServerPublicHostKey(), phpseclib\Net\SFTP\login(), phpseclib\Net\SSH2\read(), phpseclib\Net\SFTP\readlink(), phpseclib\Net\SFTP\rmdir(), and phpseclib\Net\SFTP\symlink().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ disablePTY()
| phpseclib\Net\SSH2::disablePTY | ( | ) |
◆ disableQuietMode()
| phpseclib\Net\SSH2::disableQuietMode | ( | ) |
◆ disconnect()
| phpseclib\Net\SSH2::disconnect | ( | ) |
Disconnect.
@access public
Definition at line 2833 of file SSH2.php.
References phpseclib\Net\SSH2\_disconnect().
Referenced by phpseclib\Net\SSH2\__destruct().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ enablePTY()
| phpseclib\Net\SSH2::enablePTY | ( | ) |
◆ enableQuietMode()
| phpseclib\Net\SSH2::enableQuietMode | ( | ) |
◆ exec()
| phpseclib\Net\SSH2::exec | ( | $command, | |
$callback = null |
|||
| ) |
Execute Command.
If $callback is set to false then \phpseclib\Net\SSH2::_get_channel_packet(self::CHANNEL_EXEC) will need to be called manually. In all likelihood, this is not a feature you want to be taking advantage of.
- Parameters
-
string $command Callback $callback
- Returns
- string @access public
Definition at line 2368 of file SSH2.php.
References Sabre\VObject\$output, $response, phpseclib\Net\SSH2\$terminal_modes, phpseclib\Net\SSH2\$timeout, $type, phpseclib\Net\SSH2\$window_size, phpseclib\Net\SSH2\_close_channel(), phpseclib\Net\SSH2\_disconnect(), phpseclib\Net\SSH2\_get_binary_packet(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\_string_shift(), and phpseclib\Net\SSH2\CHANNEL_EXEC.
 Here is the call graph for this function:
Here is the call graph for this function:◆ getBannerMessage()
| phpseclib\Net\SSH2::getBannerMessage | ( | ) |
Returns the banner message.
Quoting from the RFC, "in some jurisdictions, sending a warning message before authentication may be relevant for getting legal protection."
- Returns
- string @access public
Definition at line 3949 of file SSH2.php.
References phpseclib\Net\SSH2\$banner_message.
◆ getCompressionAlgorithmsClient2Server()
| phpseclib\Net\SSH2::getCompressionAlgorithmsClient2Server | ( | ) |
Return a list of the compression algorithms the server supports, when receiving stuff from the client.
- Returns
- array @access public
Definition at line 3894 of file SSH2.php.
References phpseclib\Net\SSH2\$compression_algorithms_client_to_server, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getCompressionAlgorithmsServer2Client()
| phpseclib\Net\SSH2::getCompressionAlgorithmsServer2Client | ( | ) |
Return a list of the compression algorithms the server supports, when sending stuff to the client.
- Returns
- array @access public
Definition at line 3907 of file SSH2.php.
References phpseclib\Net\SSH2\$compression_algorithms_server_to_client, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getEncryptionAlgorithmsClient2Server()
| phpseclib\Net\SSH2::getEncryptionAlgorithmsClient2Server | ( | ) |
Return a list of the (symmetric key) encryption algorithms the server supports, when receiving stuff from the client.
- Returns
- array @access public
Definition at line 3842 of file SSH2.php.
References phpseclib\Net\SSH2\$encryption_algorithms_client_to_server, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getEncryptionAlgorithmsServer2Client()
| phpseclib\Net\SSH2::getEncryptionAlgorithmsServer2Client | ( | ) |
Return a list of the (symmetric key) encryption algorithms the server supports, when sending stuff to the client.
- Returns
- array @access public
Definition at line 3855 of file SSH2.php.
References phpseclib\Net\SSH2\$encryption_algorithms_server_to_client, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getErrors()
| phpseclib\Net\SSH2::getErrors | ( | ) |
Returns all errors.
- Returns
- string @access public
Definition at line 3777 of file SSH2.php.
References phpseclib\Net\SSH2\$errors.
◆ getExitStatus()
| phpseclib\Net\SSH2::getExitStatus | ( | ) |
Returns the exit status of an SSH command or false.
- Returns
- false|int @access public
Definition at line 4104 of file SSH2.php.
References phpseclib\Net\SSH2\$exit_status.
◆ getKexAlgorithms()
| phpseclib\Net\SSH2::getKexAlgorithms | ( | ) |
Return a list of the key exchange algorithms the server supports.
- Returns
- array @access public
Definition at line 3816 of file SSH2.php.
References phpseclib\Net\SSH2\$kex_algorithms, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getLanguagesClient2Server()
| phpseclib\Net\SSH2::getLanguagesClient2Server | ( | ) |
Return a list of the languages the server supports, when receiving stuff from the client.
- Returns
- array @access public
Definition at line 3933 of file SSH2.php.
References phpseclib\Net\SSH2\$languages_client_to_server, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getLanguagesServer2Client()
| phpseclib\Net\SSH2::getLanguagesServer2Client | ( | ) |
Return a list of the languages the server supports, when sending stuff to the client.
- Returns
- array @access public
Definition at line 3920 of file SSH2.php.
References phpseclib\Net\SSH2\$languages_server_to_client, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getLastError()
| phpseclib\Net\SSH2::getLastError | ( | ) |
◆ getLog()
| phpseclib\Net\SSH2::getLog | ( | ) |
Returns a log of the packets that have been sent and received.
Returns a string if NET_SSH2_LOGGING == self::LOG_COMPLEX, an array if NET_SSH2_LOGGING == self::LOG_SIMPLE and false if !defined('NET_SSH2_LOGGING')
@access public
- Returns
- array|false|string
Definition at line 3670 of file SSH2.php.
References phpseclib\Net\SSH2\$message_number_log, phpseclib\Net\SSH2\_format_log(), phpseclib\Net\SSH2\LOG_COMPLEX, and phpseclib\Net\SSH2\LOG_SIMPLE.
 Here is the call graph for this function:
Here is the call graph for this function:◆ getMACAlgorithmsClient2Server()
| phpseclib\Net\SSH2::getMACAlgorithmsClient2Server | ( | ) |
Return a list of the MAC algorithms the server supports, when receiving stuff from the client.
- Returns
- array @access public
Definition at line 3868 of file SSH2.php.
References phpseclib\Net\SSH2\$mac_algorithms_client_to_server, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getMACAlgorithmsServer2Client()
| phpseclib\Net\SSH2::getMACAlgorithmsServer2Client | ( | ) |
Return a list of the MAC algorithms the server supports, when sending stuff to the client.
- Returns
- array @access public
Definition at line 3881 of file SSH2.php.
References phpseclib\Net\SSH2\$mac_algorithms_server_to_client, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getServerHostKeyAlgorithms()
| phpseclib\Net\SSH2::getServerHostKeyAlgorithms | ( | ) |
Return a list of the host key (public key) algorithms the server supports.
- Returns
- array @access public
Definition at line 3829 of file SSH2.php.
References phpseclib\Net\SSH2\$server_host_key_algorithms, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getServerIdentification()
| phpseclib\Net\SSH2::getServerIdentification | ( | ) |
Return the server identification.
- Returns
- string @access public
Definition at line 3803 of file SSH2.php.
References phpseclib\Net\SSH2\$server_identifier, and phpseclib\Net\SSH2\_connect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getServerPublicHostKey()
| phpseclib\Net\SSH2::getServerPublicHostKey | ( | ) |
Returns the server public host key.
Caching this the first time you connect to a server and checking the result on subsequent connections is recommended. Returns false if the server signature is not signed correctly with the public host key.
- Returns
- mixed @access public
Definition at line 3963 of file SSH2.php.
References $h, $n, $r, $s, phpseclib\Net\SSH2\$server_public_host_key, phpseclib\Net\SSH2\$signature, $w, $y, phpseclib\Net\SSH2\_connect(), phpseclib\Net\SSH2\_disconnect(), and phpseclib\Net\SSH2\_string_shift().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getStdError()
| phpseclib\Net\SSH2::getStdError | ( | ) |
Get the output from stdError.
@access public
Definition at line 2352 of file SSH2.php.
References phpseclib\Net\SSH2\$stdErrorLog.
◆ getWindowColumns()
| phpseclib\Net\SSH2::getWindowColumns | ( | ) |
Returns the number of columns for the terminal window size.
- Returns
- int @access public
Definition at line 4118 of file SSH2.php.
References phpseclib\Net\SSH2\$windowColumns.
◆ getWindowRows()
| phpseclib\Net\SSH2::getWindowRows | ( | ) |
Returns the number of rows for the terminal window size.
- Returns
- int @access public
Definition at line 4129 of file SSH2.php.
References phpseclib\Net\SSH2\$windowRows.
◆ isAuthenticated()
| phpseclib\Net\SSH2::isAuthenticated | ( | ) |
Have you successfully been logged in?
- Returns
- bool @access public
Definition at line 2871 of file SSH2.php.
References phpseclib\Net\SSH2\MASK_LOGIN.
◆ isConnected()
| phpseclib\Net\SSH2::isConnected | ( | ) |
Is the connection still active?
- Returns
- bool @access public
Definition at line 2860 of file SSH2.php.
References phpseclib\Net\SSH2\MASK_CONNECTED.
◆ isPTYEnabled()
| phpseclib\Net\SSH2::isPTYEnabled | ( | ) |
Returns whether request-pty is enabled or not.
- See also
- self::enablePTY()
- self::disablePTY() @access User interface
- Returns
- bool
Definition at line 3161 of file SSH2.php.
References phpseclib\Net\SSH2\$request_pty.
◆ isQuietModeEnabled()
| phpseclib\Net\SSH2::isQuietModeEnabled | ( | ) |
Returns whether Quiet Mode is enabled or not.
- See also
- self::enableQuietMode()
- self::disableQuietMode() @access User interface
- Returns
- bool
Definition at line 3128 of file SSH2.php.
References phpseclib\Net\SSH2\$quiet_mode.
◆ isTimeout()
| phpseclib\Net\SSH2::isTimeout | ( | ) |
Is timeout?
Did exec() or read() return because they timed out or because they encountered the end?
@access public
Definition at line 2823 of file SSH2.php.
References phpseclib\Net\SSH2\$is_timeout.
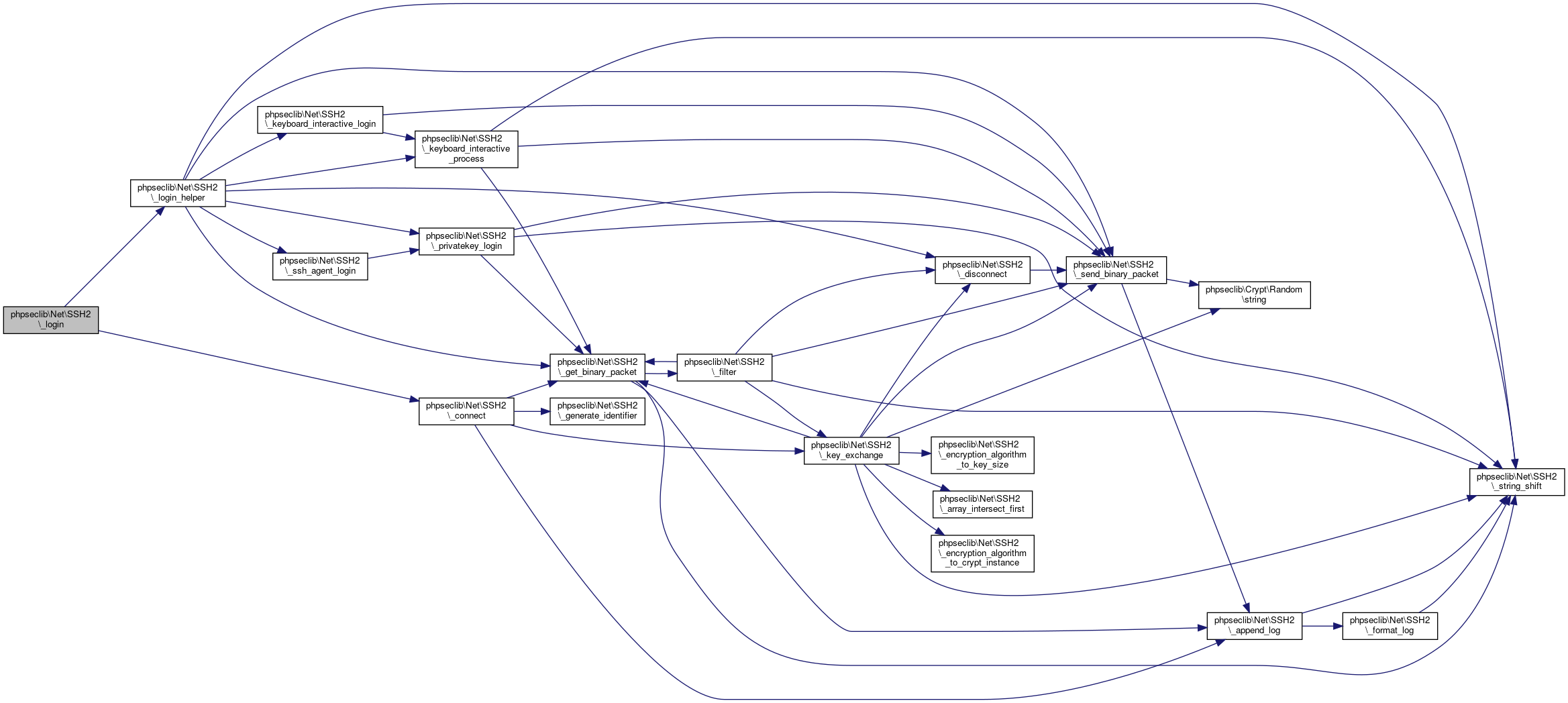
◆ login()
| phpseclib\Net\SSH2::login | ( | $username | ) |
Login.
The $password parameter can be a plaintext password, a \phpseclib\Crypt\RSA object or an array
- Parameters
-
string $username mixed $password mixed $...
- Returns
- bool
- See also
- self::_login() @access User interface
Reimplemented in phpseclib\Net\SFTP.
Definition at line 1851 of file SSH2.php.
◆ read()
| phpseclib\Net\SSH2::read | ( | $expect = '', |
|
$mode = self::READ_SIMPLE |
|||
| ) |
Returns the output of an interactive shell.
Returns when there's a match for $expect, which can take the form of a string literal or, if $mode == self::READ_REGEX, a regular expression.
- See also
- self::write()
- Parameters
-
string $expect int $mode
- Returns
- string @access public
Definition at line 2661 of file SSH2.php.
References $response, phpseclib\Net\SSH2\$timeout, phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_get_interactive_channel(), phpseclib\Net\SSH2\_initShell(), and phpseclib\Net\SSH2\_string_shift().
 Here is the call graph for this function:
Here is the call graph for this function:◆ reset()
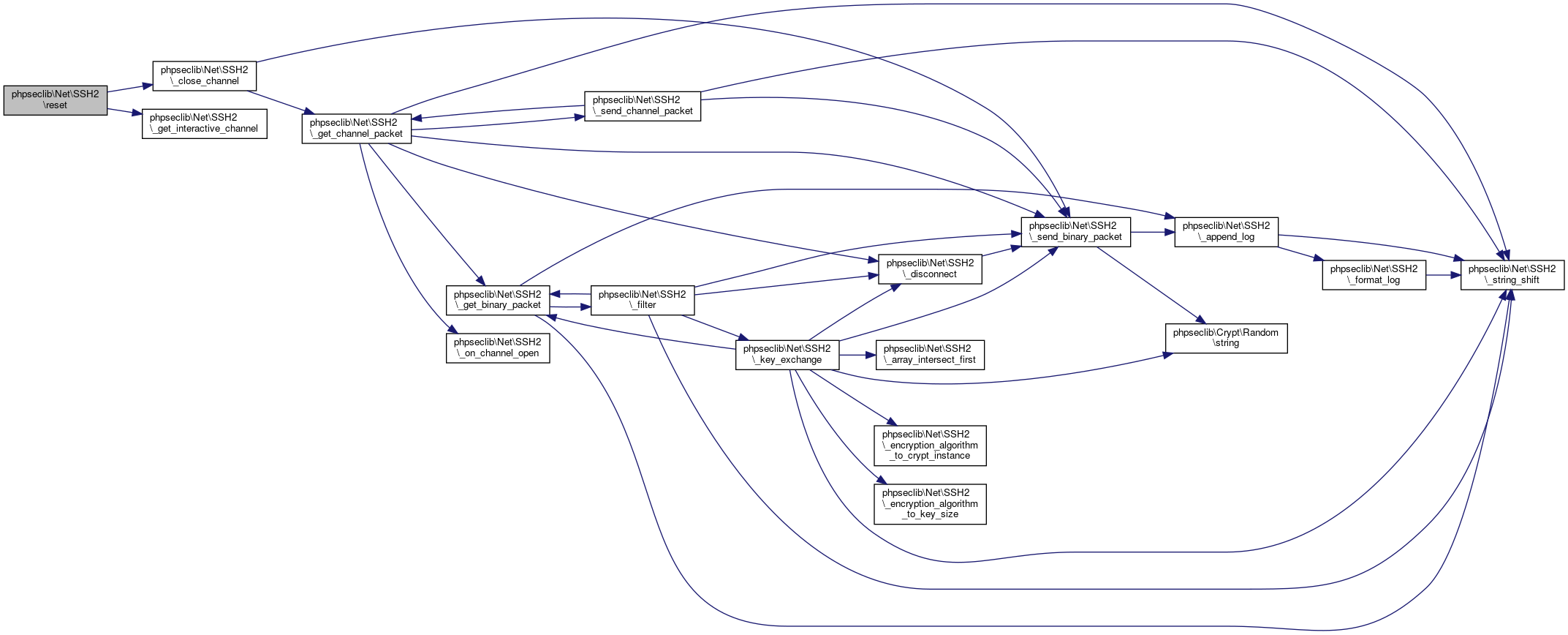
| phpseclib\Net\SSH2::reset | ( | ) |
Closes a channel.
If read() timed out you might want to just close the channel and have it auto-restart on the next read() call
@access public
Definition at line 2811 of file SSH2.php.
References phpseclib\Net\SSH2\_close_channel(), and phpseclib\Net\SSH2\_get_interactive_channel().
 Here is the call graph for this function:
Here is the call graph for this function:◆ setCryptoEngine()
| phpseclib\Net\SSH2::setCryptoEngine | ( | $engine | ) |
◆ setTimeout()
| phpseclib\Net\SSH2::setTimeout | ( | $timeout | ) |
Set Timeout.
$ssh->exec('ping 127.0.0.1'); on a Linux host will never return and will run indefinitely. setTimeout() makes it so it'll timeout. Setting $timeout to false or 0 will mean there is no timeout.
- Parameters
-
mixed $timeout @access public
Definition at line 2342 of file SSH2.php.
References phpseclib\Net\SSH2\$timeout.
◆ setWindowColumns()
| phpseclib\Net\SSH2::setWindowColumns | ( | $value | ) |
◆ setWindowRows()
| phpseclib\Net\SSH2::setWindowRows | ( | $value | ) |
◆ setWindowSize()
| phpseclib\Net\SSH2::setWindowSize | ( | $columns = 80, |
|
$rows = 24 |
|||
| ) |
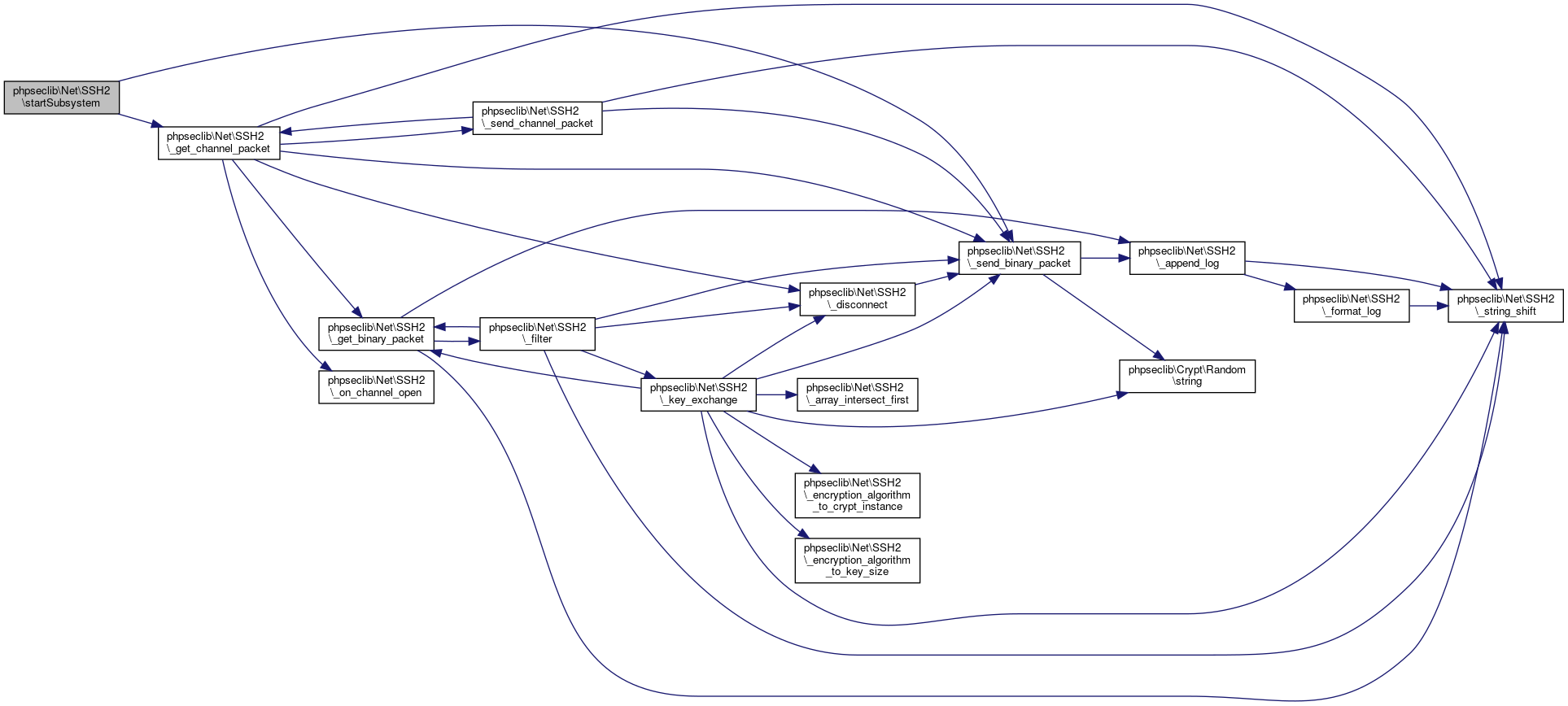
◆ startSubsystem()
| phpseclib\Net\SSH2::startSubsystem | ( | $subsystem | ) |
Start a subsystem.
Right now only one subsystem at a time is supported. To support multiple subsystem's stopSubsystem() could accept a string that contained the name of the subsystem, but at that point, only one subsystem of each type could be opened. To support multiple subsystem's of the same name maybe it'd be best if startSubsystem() generated a new channel id and returns that and then that that was passed into stopSubsystem() but that'll be saved for a future date and implemented if there's sufficient demand for such a feature.
- See also
- self::stopSubsystem()
- Parameters
-
string $subsystem
- Returns
- bool @access public
Definition at line 2735 of file SSH2.php.
References $response, phpseclib\Net\SSH2\$window_size, phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_send_binary_packet(), phpseclib\Net\SSH2\CHANNEL_SUBSYSTEM, and phpseclib\Net\SSH2\MASK_SHELL.
 Here is the call graph for this function:
Here is the call graph for this function:◆ stopSubsystem()
| phpseclib\Net\SSH2::stopSubsystem | ( | ) |
Stops a subsystem.
- See also
- self::startSubsystem()
- Returns
- bool @access public
Definition at line 2797 of file SSH2.php.
References phpseclib\Net\SSH2\_close_channel().
 Here is the call graph for this function:
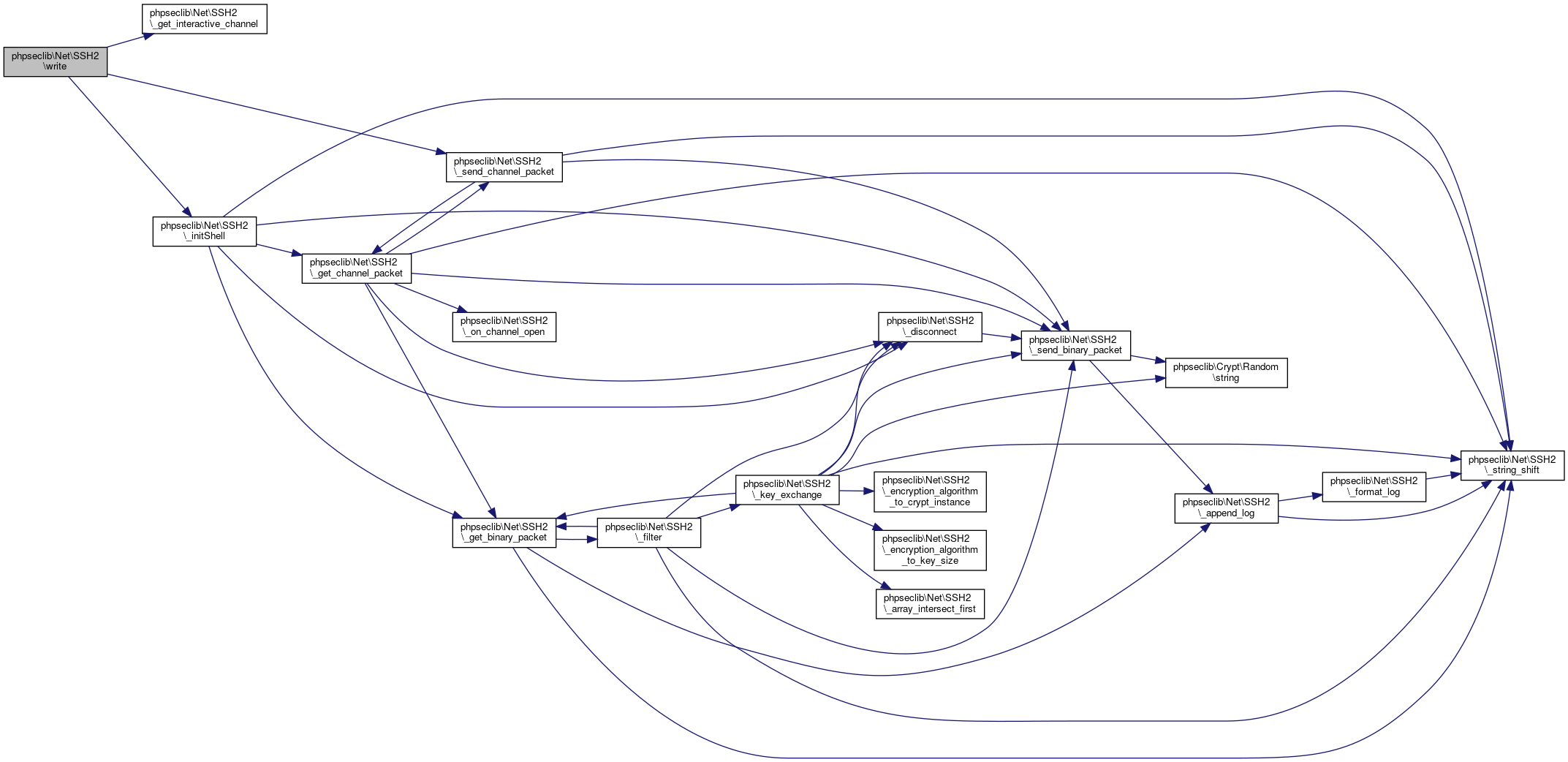
Here is the call graph for this function:◆ write()
| phpseclib\Net\SSH2::write | ( | $cmd | ) |
Inputs a command into an interactive shell.
- See also
- self::read()
- Parameters
-
string $cmd
- Returns
- bool @access public
Definition at line 2706 of file SSH2.php.
References phpseclib\Net\SSH2\_get_interactive_channel(), phpseclib\Net\SSH2\_initShell(), and phpseclib\Net\SSH2\_send_channel_packet().
 Here is the call graph for this function:
Here is the call graph for this function:Field Documentation
◆ $agent
| phpseclib\Net\SSH2::$agent |
Definition at line 867 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_ssh_agent_login().
◆ $banner_message
| phpseclib\Net\SSH2::$banner_message = '' |
Definition at line 771 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\getBannerMessage().
◆ $bitmap
◆ $channel_buffers
◆ $channel_extended_data_type_codes
| phpseclib\Net\SSH2::$channel_extended_data_type_codes = array() |
◆ $channel_open_failure_reasons
| phpseclib\Net\SSH2::$channel_open_failure_reasons = array() |
◆ $channel_status
◆ $compression_algorithms_client_to_server
| phpseclib\Net\SSH2::$compression_algorithms_client_to_server = false |
Definition at line 283 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getCompressionAlgorithmsClient2Server().
◆ $compression_algorithms_server_to_client
| phpseclib\Net\SSH2::$compression_algorithms_server_to_client = false |
Definition at line 292 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getCompressionAlgorithmsServer2Client().
◆ $crypto_engine
◆ $curTimeout
| phpseclib\Net\SSH2::$curTimeout |
◆ $decrypt
| phpseclib\Net\SSH2::$decrypt = false |
Definition at line 346 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange().
◆ $decrypt_block_size
| phpseclib\Net\SSH2::$decrypt_block_size = 8 |
Definition at line 337 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_get_binary_packet().
◆ $disconnect_reasons
◆ $encrypt
| phpseclib\Net\SSH2::$encrypt = false |
Definition at line 355 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange().
◆ $encrypt_block_size
| phpseclib\Net\SSH2::$encrypt_block_size = 8 |
Definition at line 327 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_send_binary_packet().
◆ $encryption_algorithms_client_to_server
| phpseclib\Net\SSH2::$encryption_algorithms_client_to_server = false |
Definition at line 247 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getEncryptionAlgorithmsClient2Server().
◆ $encryption_algorithms_server_to_client
| phpseclib\Net\SSH2::$encryption_algorithms_server_to_client = false |
Definition at line 256 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getEncryptionAlgorithmsServer2Client().
◆ $errors
| phpseclib\Net\SSH2::$errors = array() |
Definition at line 184 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\getErrors().
◆ $exchange_hash
| phpseclib\Net\SSH2::$exchange_hash = false |
Definition at line 421 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange().
◆ $exit_status
| phpseclib\Net\SSH2::$exit_status |
Definition at line 707 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_get_channel_packet(), and phpseclib\Net\SSH2\getExitStatus().
◆ $fsock
◆ $get_seq_no
◆ $hmac_check
◆ $hmac_create
◆ $hmac_size
◆ $host
| phpseclib\Net\SSH2::$host |
Definition at line 817 of file SSH2.php.
Referenced by phpseclib\Net\SFTP\__construct(), phpseclib\Net\SSH2\__construct(), phpseclib\Net\SSH2\_connect(), and phpseclib\Net\SFTP\Stream\_parse_path().
◆ $identifier
| phpseclib\Net\SSH2::$identifier |
Definition at line 155 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_generate_identifier().
◆ $in_request_pty_exec
◆ $in_subsystem
◆ $interactiveBuffer
◆ $is_timeout
| phpseclib\Net\SSH2::$is_timeout = false |
Definition at line 780 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\isTimeout().
◆ $kex_algorithms
| phpseclib\Net\SSH2::$kex_algorithms = false |
Definition at line 202 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getKexAlgorithms().
◆ $kex_dh_group_size_max
◆ $kex_dh_group_size_min
◆ $kex_dh_group_size_preferred
◆ $keyboard_requests_responses
◆ $languages_client_to_server
| phpseclib\Net\SSH2::$languages_client_to_server = false |
Definition at line 310 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\getLanguagesClient2Server().
◆ $languages_server_to_client
| phpseclib\Net\SSH2::$languages_server_to_client = false |
Definition at line 301 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\getLanguagesServer2Client().
◆ $last_interactive_response
| phpseclib\Net\SSH2::$last_interactive_response = '' |
Definition at line 749 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_keyboard_interactive_process().
◆ $last_packet
◆ $log_boundary
◆ $log_long_width
◆ $log_short_width
◆ $log_size
◆ $mac_algorithms_client_to_server
| phpseclib\Net\SSH2::$mac_algorithms_client_to_server = false |
Definition at line 265 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getMACAlgorithmsClient2Server().
◆ $mac_algorithms_server_to_client
| phpseclib\Net\SSH2::$mac_algorithms_server_to_client = false |
Definition at line 274 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getMACAlgorithmsServer2Client().
◆ $message_log
| phpseclib\Net\SSH2::$message_log = array() |
Definition at line 555 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_format_log().
◆ $message_number_log
| phpseclib\Net\SSH2::$message_number_log = array() |
Definition at line 546 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_format_log(), and phpseclib\Net\SSH2\getLog().
◆ $message_numbers
◆ $packet_size_client_to_server
| phpseclib\Net\SSH2::$packet_size_client_to_server = array() |
◆ $port
| phpseclib\Net\SSH2::$port |
Definition at line 827 of file SSH2.php.
Referenced by phpseclib\Net\SFTP\__construct(), phpseclib\Net\SSH2\__construct(), phpseclib\Net\SSH2\_connect(), and phpseclib\Net\SFTP\Stream\_parse_path().
◆ $quiet_mode
| phpseclib\Net\SSH2::$quiet_mode = false |
Flag to suppress stderr from output.
- See also
- self::enableQuietMode() @access private
Definition at line 691 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\isQuietModeEnabled().
◆ $realtime_log_file
◆ $realtime_log_size
◆ $realtime_log_wrap
| phpseclib\Net\SSH2::$realtime_log_wrap |
◆ $request_pty
| phpseclib\Net\SSH2::$request_pty = false |
Definition at line 716 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\isPTYEnabled().
◆ $send_seq_no
◆ $server_channels
◆ $server_host_key_algorithms
| phpseclib\Net\SSH2::$server_host_key_algorithms = false |
Definition at line 238 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getServerHostKeyAlgorithms().
◆ $server_identifier
| phpseclib\Net\SSH2::$server_identifier = false |
Definition at line 193 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\getServerIdentification().
◆ $server_public_host_key
| phpseclib\Net\SSH2::$server_public_host_key |
Definition at line 395 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_key_exchange(), and phpseclib\Net\SSH2\getServerPublicHostKey().
◆ $session_id
◆ $signature
| phpseclib\Net\SSH2::$signature = '' |
Definition at line 600 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_privatekey_login(), and phpseclib\Net\SSH2\getServerPublicHostKey().
◆ $signature_format
◆ $signature_validated
◆ $stdErrorLog
| phpseclib\Net\SSH2::$stdErrorLog |
Definition at line 740 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\getStdError().
◆ $terminal_modes
| phpseclib\Net\SSH2::$terminal_modes = array() |
Definition at line 458 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_initShell(), and phpseclib\Net\SSH2\exec().
◆ $timeout
| phpseclib\Net\SSH2::$timeout |
Timeout.
- See also
- self::setTimeout() @access private
Definition at line 640 of file SSH2.php.
Referenced by phpseclib\Net\SFTP\__construct(), phpseclib\Net\SSH2\__construct(), phpseclib\Net\SSH2\_connect(), phpseclib\Net\SSH2\exec(), phpseclib\Net\SSH2\read(), and phpseclib\Net\SSH2\setTimeout().
◆ $window_size
| phpseclib\Net\SSH2::$window_size = 0x7FFFFFFF |
Definition at line 567 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_filter(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_initShell(), phpseclib\Net\SSH2\exec(), phpseclib\Net\SFTP\login(), and phpseclib\Net\SSH2\startSubsystem().
◆ $window_size_client_to_server
| phpseclib\Net\SSH2::$window_size_client_to_server = array() |
◆ $window_size_server_to_client
| phpseclib\Net\SSH2::$window_size_server_to_client = array() |
◆ $windowColumns
| phpseclib\Net\SSH2::$windowColumns = 80 |
Definition at line 838 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\getWindowColumns().
◆ $windowRows
| phpseclib\Net\SSH2::$windowRows = 24 |
Definition at line 849 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\getWindowRows().
◆ CHANNEL_AGENT_FORWARD
| const phpseclib\Net\SSH2::CHANNEL_AGENT_FORWARD = 3 |
Definition at line 106 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_filter().
◆ CHANNEL_EXEC
| const phpseclib\Net\SSH2::CHANNEL_EXEC = 0 |
#-
#+ Channel constants
RFC4254 refers not to client and server channels but rather to sender and recipient channels. we don't refer to them in that way because RFC4254 toggles the meaning. the client sends a SSH_MSG_CHANNEL_OPEN message with a sender channel and the server sends a SSH_MSG_CHANNEL_OPEN_CONFIRMATION in response, with a sender and a recepient channel. at first glance, you might conclude that SSH_MSG_CHANNEL_OPEN_CONFIRMATION's sender channel would be the same thing as SSH_MSG_CHANNEL_OPEN's sender channel, but it's not, per this snipet: The 'recipient channel' is the channel number given in the original open request, and 'sender channel' is the channel number allocated by the other side.
- See also
- \phpseclib\Net\SSH2::_send_channel_packet()
- \phpseclib\Net\SSH2::_get_channel_packet() @access private
Definition at line 103 of file SSH2.php.
Referenced by phpseclib\Net\SCP\_close(), phpseclib\Net\SSH2\_get_interactive_channel(), phpseclib\Net\SSH2\_get_open_channel(), phpseclib\Net\SCP\_receive(), phpseclib\Net\SCP\_send(), phpseclib\Net\SSH2\exec(), and phpseclib\Net\SCP\put().
◆ CHANNEL_SHELL
| const phpseclib\Net\SSH2::CHANNEL_SHELL = 1 |
Definition at line 104 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_get_interactive_channel(), and phpseclib\Net\SSH2\_initShell().
◆ CHANNEL_SUBSYSTEM
| const phpseclib\Net\SSH2::CHANNEL_SUBSYSTEM = 2 |
Definition at line 105 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_get_interactive_channel(), and phpseclib\Net\SSH2\startSubsystem().
◆ LOG_COMPLEX
| const phpseclib\Net\SSH2::LOG_COMPLEX = 2 |
Returns the message content.
Definition at line 120 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_append_log(), and phpseclib\Net\SSH2\getLog().
◆ LOG_MAX_SIZE
| const phpseclib\Net\SSH2::LOG_MAX_SIZE = 1048576 |
◆ LOG_REALTIME
| const phpseclib\Net\SSH2::LOG_REALTIME = 3 |
Outputs the content real-time.
Definition at line 124 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_append_log().
◆ LOG_REALTIME_FILE
| const phpseclib\Net\SSH2::LOG_REALTIME_FILE = 4 |
Dumps the content real-time to a file.
Definition at line 128 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_append_log().
◆ LOG_SIMPLE
| const phpseclib\Net\SSH2::LOG_SIMPLE = 1 |
#-
#+ @access public
- See also
- \phpseclib\Net\SSH2::getLog() Returns the message numbers
Definition at line 116 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_append_log(), and phpseclib\Net\SSH2\getLog().
◆ MASK_CONNECTED
| const phpseclib\Net\SSH2::MASK_CONNECTED = 0x00000002 |
Definition at line 80 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_connect(), and phpseclib\Net\SSH2\isConnected().
◆ MASK_CONSTRUCTOR
| const phpseclib\Net\SSH2::MASK_CONSTRUCTOR = 0x00000001 |
#+ Execution Bitmap Masks
- See also
- \phpseclib\Net\SSH2::bitmap @access private
Definition at line 79 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_connect().
◆ MASK_LOGIN
| const phpseclib\Net\SSH2::MASK_LOGIN = 0x00000008 |
Definition at line 82 of file SSH2.php.
Referenced by phpseclib\Net\SFTP\_list(), phpseclib\Net\SSH2\_login_helper(), phpseclib\Net\SSH2\_privatekey_login(), phpseclib\Net\SFTP\_setstat(), phpseclib\Net\SFTP\chdir(), phpseclib\Net\SFTP\delete(), phpseclib\Net\SFTP\get(), phpseclib\Net\SSH2\isAuthenticated(), phpseclib\Net\SFTP\lstat(), phpseclib\Net\SFTP\mkdir(), phpseclib\Net\SFTP\put(), phpseclib\Net\SFTP\readlink(), phpseclib\Net\SFTP\rename(), phpseclib\Net\SFTP\rmdir(), phpseclib\Net\SFTP\size(), phpseclib\Net\SFTP\stat(), phpseclib\Net\SFTP\symlink(), and phpseclib\Net\SFTP\touch().
◆ MASK_LOGIN_REQ
| const phpseclib\Net\SSH2::MASK_LOGIN_REQ = 0x00000004 |
Definition at line 81 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_login_helper().
◆ MASK_SHELL
| const phpseclib\Net\SSH2::MASK_SHELL = 0x00000010 |
Definition at line 83 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_close_channel(), phpseclib\Net\SSH2\_get_channel_packet(), phpseclib\Net\SSH2\_initShell(), and phpseclib\Net\SSH2\startSubsystem().
◆ MASK_WINDOW_ADJUST
| const phpseclib\Net\SSH2::MASK_WINDOW_ADJUST = 0x00000020 |
Definition at line 84 of file SSH2.php.
Referenced by phpseclib\Net\SSH2\_filter(), and phpseclib\Net\SSH2\_send_channel_packet().
◆ READ_REGEX
| const phpseclib\Net\SSH2::READ_REGEX = 2 |
◆ READ_SIMPLE
| const phpseclib\Net\SSH2::READ_SIMPLE = 1 |
The documentation for this class was generated from the following file:
- libs/composer/vendor/phpseclib/phpseclib/phpseclib/Net/SSH2.php