Collaboration diagram for phpseclib\Crypt\RSA:
Collaboration diagram for phpseclib\Crypt\RSA:Public Member Functions | |
| __construct () | |
| The constructor. More... | |
| createKey ($bits=1024, $timeout=false, $partial=array()) | |
| Create public / private key pair. More... | |
| _convertPrivateKey ($n, $e, $d, $primes, $exponents, $coefficients) | |
| Convert a private key to the appropriate format. More... | |
| _convertPublicKey ($n, $e) | |
| Convert a public key to the appropriate format. More... | |
| _parseKey ($key, $type) | |
| Break a public or private key down into its constituant components. More... | |
| getSize () | |
| Returns the key size. More... | |
| _start_element_handler ($parser, $name, $attribs) | |
| Start Element Handler. More... | |
| _stop_element_handler ($parser, $name) | |
| Stop Element Handler. More... | |
| _data_handler ($parser, $data) | |
| Data Handler. More... | |
| loadKey ($key, $type=false) | |
| Loads a public or private key. More... | |
| setPassword ($password=false) | |
| Sets the password. More... | |
| setPublicKey ($key=false, $type=false) | |
| Defines the public key. More... | |
| setPrivateKey ($key=false, $type=false) | |
| Defines the private key. More... | |
| getPublicKey ($type=self::PUBLIC_FORMAT_PKCS8) | |
| Returns the public key. More... | |
| getPublicKeyFingerprint ($algorithm='md5') | |
| Returns the public key's fingerprint. More... | |
| getPrivateKey ($type=self::PUBLIC_FORMAT_PKCS1) | |
| Returns the private key. More... | |
| _getPrivatePublicKey ($mode=self::PUBLIC_FORMAT_PKCS8) | |
| Returns a minimalistic private key. More... | |
| __toString () | |
| __toString() magic method More... | |
| __clone () | |
| __clone() magic method More... | |
| _generateMinMax ($bits) | |
| Generates the smallest and largest numbers requiring $bits bits. More... | |
| _decodeLength (&$string) | |
| DER-decode the length. More... | |
| _encodeLength ($length) | |
| DER-encode the length. More... | |
| _string_shift (&$string, $index=1) | |
| String Shift. More... | |
| setPrivateKeyFormat ($format) | |
| Determines the private key format. More... | |
| setPublicKeyFormat ($format) | |
| Determines the public key format. More... | |
| setHash ($hash) | |
| Determines which hashing function should be used. More... | |
| setMGFHash ($hash) | |
| Determines which hashing function should be used for the mask generation function. More... | |
| setSaltLength ($sLen) | |
| Determines the salt length. More... | |
| _i2osp ($x, $xLen) | |
| Integer-to-Octet-String primitive. More... | |
| _os2ip ($x) | |
| Octet-String-to-Integer primitive. More... | |
| _exponentiate ($x) | |
| Exponentiate with or without Chinese Remainder Theorem. More... | |
| _blind ($x, $r, $i) | |
| Performs RSA Blinding. More... | |
| _equals ($x, $y) | |
| Performs blinded RSA equality testing. More... | |
| _rsaep ($m) | |
| RSAEP. More... | |
| _rsadp ($c) | |
| RSADP. More... | |
| _rsasp1 ($m) | |
| RSASP1. More... | |
| _rsavp1 ($s) | |
| RSAVP1. More... | |
| _mgf1 ($mgfSeed, $maskLen) | |
| MGF1. More... | |
| _rsaes_oaep_encrypt ($m, $l='') | |
| RSAES-OAEP-ENCRYPT. More... | |
| _rsaes_oaep_decrypt ($c, $l='') | |
| RSAES-OAEP-DECRYPT. More... | |
| _raw_encrypt ($m) | |
| Raw Encryption / Decryption. More... | |
| _rsaes_pkcs1_v1_5_encrypt ($m) | |
| RSAES-PKCS1-V1_5-ENCRYPT. More... | |
| _rsaes_pkcs1_v1_5_decrypt ($c) | |
| RSAES-PKCS1-V1_5-DECRYPT. More... | |
| _emsa_pss_encode ($m, $emBits) | |
| EMSA-PSS-ENCODE. More... | |
| _emsa_pss_verify ($m, $em, $emBits) | |
| EMSA-PSS-VERIFY. More... | |
| _rsassa_pss_sign ($m) | |
| RSASSA-PSS-SIGN. More... | |
| _rsassa_pss_verify ($m, $s) | |
| RSASSA-PSS-VERIFY. More... | |
| _emsa_pkcs1_v1_5_encode ($m, $emLen) | |
| EMSA-PKCS1-V1_5-ENCODE. More... | |
| _rsassa_pkcs1_v1_5_sign ($m) | |
| RSASSA-PKCS1-V1_5-SIGN. More... | |
| _rsassa_pkcs1_v1_5_verify ($m, $s) | |
| RSASSA-PKCS1-V1_5-VERIFY. More... | |
| setEncryptionMode ($mode) | |
| Set Encryption Mode. More... | |
| setSignatureMode ($mode) | |
| Set Signature Mode. More... | |
| setComment ($comment) | |
| Set public key comment. More... | |
| getComment () | |
| Get public key comment. More... | |
| encrypt ($plaintext) | |
| Encryption. More... | |
| decrypt ($ciphertext) | |
| Decryption. More... | |
| sign ($message) | |
| Create a signature. More... | |
| verify ($message, $signature) | |
| Verifies a signature. More... | |
| _extractBER ($str) | |
| Extract raw BER from Base64 encoding. More... | |
Data Fields | |
| const | ENCRYPTION_OAEP = 1 |
| #+ @access public More... | |
| const | ENCRYPTION_PKCS1 = 2 |
| Use PKCS#1 padding. More... | |
| const | ENCRYPTION_NONE = 3 |
| Do not use any padding. More... | |
| const | SIGNATURE_PSS = 1 |
| #- More... | |
| const | SIGNATURE_PKCS1 = 2 |
| Use the PKCS#1 scheme by default. More... | |
| const | ASN1_INTEGER = 2 |
| #- More... | |
| const | ASN1_BITSTRING = 3 |
| ASN1 Bit String. More... | |
| const | ASN1_OCTETSTRING = 4 |
| ASN1 Octet String. More... | |
| const | ASN1_OBJECT = 6 |
| ASN1 Object Identifier. More... | |
| const | ASN1_SEQUENCE = 48 |
| ASN1 Sequence (with the constucted bit set) More... | |
| const | MODE_INTERNAL = 1 |
| #- More... | |
| const | MODE_OPENSSL = 2 |
| To use the OpenSSL library. More... | |
| const | PRIVATE_FORMAT_PKCS1 = 0 |
| #- More... | |
| const | PRIVATE_FORMAT_PUTTY = 1 |
| PuTTY formatted private key. More... | |
| const | PRIVATE_FORMAT_XML = 2 |
| XML formatted private key. More... | |
| const | PRIVATE_FORMAT_PKCS8 = 8 |
| PKCS#8 formatted private key. More... | |
| const | PUBLIC_FORMAT_RAW = 3 |
| #- More... | |
| const | PUBLIC_FORMAT_PKCS1 = 4 |
| PKCS#1 formatted public key (raw) More... | |
| const | PUBLIC_FORMAT_PKCS1_RAW = 4 |
| const | PUBLIC_FORMAT_XML = 5 |
| XML formatted public key. More... | |
| const | PUBLIC_FORMAT_OPENSSH = 6 |
| OpenSSH formatted public key. More... | |
| const | PUBLIC_FORMAT_PKCS8 = 7 |
| PKCS#1 formatted public key (encapsulated) More... | |
| $zero | |
| $one | |
| $privateKeyFormat = self::PRIVATE_FORMAT_PKCS1 | |
| $publicKeyFormat = self::PUBLIC_FORMAT_PKCS8 | |
| $modulus | |
| $k | |
| $exponent | |
| $primes | |
| $exponents | |
| $coefficients | |
| $hashName | |
| $hash | |
| $hLen | |
| $sLen | |
| $mgfHash | |
| $mgfHLen | |
| $encryptionMode = self::ENCRYPTION_OAEP | |
| $signatureMode = self::SIGNATURE_PSS | |
| $publicExponent = false | |
| $password = false | |
| $components = array() | |
| $current | |
| $configFile | |
| $comment = 'phpseclib-generated-key' | |
Detailed Description
Constructor & Destructor Documentation
◆ __construct()
| phpseclib\Crypt\RSA::__construct | ( | ) |
The constructor.
If you want to make use of the openssl extension, you'll need to set the mode manually, yourself. The reason \phpseclib\Crypt\RSA doesn't do it is because OpenSSL doesn't fail gracefully. openssl_pkey_new(), in particular, requires openssl.cnf be present somewhere and, unfortunately, the only real way to find out is too late.
- Returns
- \phpseclib\Crypt\RSA @access public
Definition at line 464 of file RSA.php.
References $i, $m, and GuzzleHttp\Psr7\hash().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ __clone()
| phpseclib\Crypt\RSA::__clone | ( | ) |
◆ __toString()
| phpseclib\Crypt\RSA::__toString | ( | ) |
__toString() magic method
@access public
- Returns
- string
Definition at line 1847 of file RSA.php.
References $key, phpseclib\Crypt\RSA\_getPrivatePublicKey(), and phpseclib\Crypt\RSA\getPrivateKey().
 Here is the call graph for this function:
Here is the call graph for this function:◆ _blind()
| phpseclib\Crypt\RSA::_blind | ( | $x, | |
| $r, | |||
| $i | |||
| ) |
Performs RSA Blinding.
Protects against timing attacks by employing RSA Blinding. Returns $x->modPow($this->exponents[$i], $this->primes[$i])
@access private
- Parameters
-
\phpseclib\Math\BigInteger $x \phpseclib\Math\BigInteger $r int $i
- Returns
- \phpseclib\Math\BigInteger
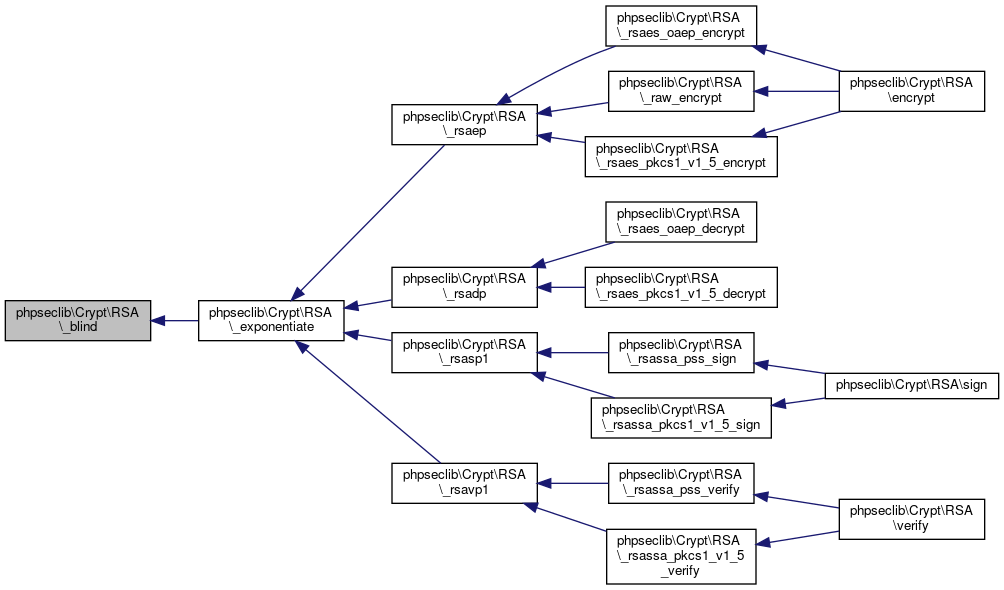
Definition at line 2173 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_exponentiate().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _convertPrivateKey()
| phpseclib\Crypt\RSA::_convertPrivateKey | ( | $n, | |
| $e, | |||
| $d, | |||
| $primes, | |||
| $exponents, | |||
| $coefficients | |||
| ) |
Convert a private key to the appropriate format.
@access private
- See also
- self::setPrivateKeyFormat()
- Parameters
-
string $RSAPrivateKey
- Returns
- string
Definition at line 720 of file RSA.php.
References phpseclib\Crypt\RSA\$coefficients, phpseclib\Crypt\RSA\$components, $d, phpseclib\Crypt\RSA\$exponents, phpseclib\Crypt\RSA\$hash, $i, $key, $n, $name, phpseclib\Crypt\RSA\$password, phpseclib\Crypt\RSA\$primes, $source, phpseclib\Crypt\RSA\_encodeLength(), comment(), phpseclib\Crypt\RSA\PRIVATE_FORMAT_PUTTY, phpseclib\Crypt\RSA\PRIVATE_FORMAT_XML, and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Crypt\RSA\createKey(), and phpseclib\Crypt\RSA\getPrivateKey().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _convertPublicKey()
| phpseclib\Crypt\RSA::_convertPublicKey | ( | $n, | |
| $e | |||
| ) |
Convert a public key to the appropriate format.
@access private
- See also
- self::setPublicKeyFormat()
- Parameters
-
string $RSAPrivateKey
- Returns
- string
Definition at line 949 of file RSA.php.
References phpseclib\Crypt\RSA\$comment, phpseclib\Crypt\RSA\$components, phpseclib\Crypt\RSA\$modulus, $n, phpseclib\Crypt\RSA\$publicExponent, phpseclib\Crypt\RSA\_encodeLength(), phpseclib\Crypt\RSA\PUBLIC_FORMAT_OPENSSH, phpseclib\Crypt\RSA\PUBLIC_FORMAT_RAW, and phpseclib\Crypt\RSA\PUBLIC_FORMAT_XML.
Referenced by phpseclib\Crypt\RSA\_getPrivatePublicKey(), phpseclib\Crypt\RSA\createKey(), and phpseclib\Crypt\RSA\getPublicKey().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _data_handler()
| phpseclib\Crypt\RSA::_data_handler | ( | $parser, | |
| $data | |||
| ) |
Data Handler.
Called by xml_set_character_data_handler()
@access private
- Parameters
-
resource $parser string $data
Definition at line 1496 of file RSA.php.
References $data.
◆ _decodeLength()
| phpseclib\Crypt\RSA::_decodeLength | ( | & | $string | ) |
DER-decode the length.
DER supports lengths up to (2**8)**127, however, we'll only support lengths up to (2**8)**4. See X.690 paragraph 8.1.3 for more information.
@access private
- Parameters
-
string $string
- Returns
- int
Definition at line 1906 of file RSA.php.
References phpseclib\Crypt\RSA\_string_shift().
Referenced by phpseclib\Crypt\RSA\_parseKey().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _emsa_pkcs1_v1_5_encode()
| phpseclib\Crypt\RSA::_emsa_pkcs1_v1_5_encode | ( | $m, | |
| $emLen | |||
| ) |
EMSA-PKCS1-V1_5-ENCODE.
See RFC3447#section-9.2.
@access private
- Parameters
-
string $m int $emLen
- Returns
- string
Definition at line 2715 of file RSA.php.
References $h, $m, $t, and GuzzleHttp\Psr7\hash().
Referenced by phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_sign(), and phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_verify().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _emsa_pss_encode()
| phpseclib\Crypt\RSA::_emsa_pss_encode | ( | $m, | |
| $emBits | |||
| ) |
EMSA-PSS-ENCODE.
@access private
- Parameters
-
string $m int $emBits
Definition at line 2565 of file RSA.php.
References $h, phpseclib\Crypt\RSA\$hLen, $m, phpseclib\Crypt\RSA\$sLen, phpseclib\Crypt\RSA\_mgf1(), GuzzleHttp\Psr7\hash(), and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Crypt\RSA\_rsassa_pss_sign().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _emsa_pss_verify()
| phpseclib\Crypt\RSA::_emsa_pss_verify | ( | $m, | |
| $em, | |||
| $emBits | |||
| ) |
EMSA-PSS-VERIFY.
@access private
- Parameters
-
string $m string $em int $emBits
- Returns
- string
Definition at line 2603 of file RSA.php.
References $h, phpseclib\Crypt\RSA\$hLen, $m, phpseclib\Crypt\RSA\$sLen, phpseclib\Crypt\RSA\_equals(), phpseclib\Crypt\RSA\_mgf1(), and GuzzleHttp\Psr7\hash().
Referenced by phpseclib\Crypt\RSA\_rsassa_pss_verify().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _encodeLength()
| phpseclib\Crypt\RSA::_encodeLength | ( | $length | ) |
DER-encode the length.
DER supports lengths up to (2**8)**127, however, we'll only support lengths up to (2**8)**4. See X.690 paragraph 8.1.3 for more information.
@access private
- Parameters
-
int $length
- Returns
- string
Definition at line 1927 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), and phpseclib\Crypt\RSA\_convertPublicKey().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _equals()
| phpseclib\Crypt\RSA::_equals | ( | $x, | |
| $y | |||
| ) |
Performs blinded RSA equality testing.
Protects against a particular type of timing attack described.
See A Lesson In Timing Attacks (or, Don't use MessageDigest.isEquals)
Thanks for the heads up singpolyma!
@access private
- Parameters
-
string $x string $y
- Returns
- bool
Definition at line 2199 of file RSA.php.
References $i, $result, $x, and $y.
Referenced by phpseclib\Crypt\RSA\_emsa_pss_verify(), and phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_verify().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _exponentiate()
| phpseclib\Crypt\RSA::_exponentiate | ( | $x | ) |
Exponentiate with or without Chinese Remainder Theorem.
@access private
- Parameters
-
\phpseclib\Math\BigInteger $x
- Returns
- \phpseclib\Math\BigInteger
Definition at line 2093 of file RSA.php.
References $h, $i, $m, phpseclib\Crypt\RSA\$one, $r, $x, and phpseclib\Crypt\RSA\_blind().
Referenced by phpseclib\Crypt\RSA\_rsadp(), phpseclib\Crypt\RSA\_rsaep(), phpseclib\Crypt\RSA\_rsasp1(), and phpseclib\Crypt\RSA\_rsavp1().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _extractBER()
| phpseclib\Crypt\RSA::_extractBER | ( | $str | ) |
Extract raw BER from Base64 encoding.
@access private
- Parameters
-
string $str
- Returns
- string
Definition at line 3025 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_parseKey().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _generateMinMax()
| phpseclib\Crypt\RSA::_generateMinMax | ( | $bits | ) |
Generates the smallest and largest numbers requiring $bits bits.
@access private
- Parameters
-
int $bits
- Returns
- array
Definition at line 1877 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\createKey().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _getPrivatePublicKey()
| phpseclib\Crypt\RSA::_getPrivatePublicKey | ( | $mode = self::PUBLIC_FORMAT_PKCS8 | ) |
Returns a minimalistic private key.
Returns the private key without the prime number constituants. Structurally identical to a public key that hasn't been set as the public key
- See also
- self::getPrivateKey() @access private
- Parameters
-
string $key int $type optional
Definition at line 1828 of file RSA.php.
References phpseclib\Crypt\RSA\$publicKeyFormat, and phpseclib\Crypt\RSA\_convertPublicKey().
Referenced by phpseclib\Crypt\RSA\__toString().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _i2osp()
| phpseclib\Crypt\RSA::_i2osp | ( | $x, | |
| $xLen | |||
| ) |
Integer-to-Octet-String primitive.
See RFC3447#section-4.1.
@access private
- Parameters
-
\phpseclib\Math\BigInteger $x int $xLen
- Returns
- string
Definition at line 2060 of file RSA.php.
References $x.
Referenced by phpseclib\Crypt\RSA\_raw_encrypt(), phpseclib\Crypt\RSA\_rsaes_oaep_decrypt(), phpseclib\Crypt\RSA\_rsaes_oaep_encrypt(), phpseclib\Crypt\RSA\_rsaes_pkcs1_v1_5_decrypt(), phpseclib\Crypt\RSA\_rsaes_pkcs1_v1_5_encrypt(), phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_sign(), phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_verify(), phpseclib\Crypt\RSA\_rsassa_pss_sign(), and phpseclib\Crypt\RSA\_rsassa_pss_verify().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _mgf1()
| phpseclib\Crypt\RSA::_mgf1 | ( | $mgfSeed, | |
| $maskLen | |||
| ) |
MGF1.
@access private
- Parameters
-
string $mgfSeed int $mgfLen
- Returns
- string
Definition at line 2295 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_emsa_pss_encode(), phpseclib\Crypt\RSA\_emsa_pss_verify(), phpseclib\Crypt\RSA\_rsaes_oaep_decrypt(), and phpseclib\Crypt\RSA\_rsaes_oaep_encrypt().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _os2ip()
| phpseclib\Crypt\RSA::_os2ip | ( | $x | ) |
Octet-String-to-Integer primitive.
See RFC3447#section-4.2.
@access private
- Parameters
-
string $x
- Returns
- \phpseclib\Math\BigInteger
Definition at line 2079 of file RSA.php.
References $x.
Referenced by phpseclib\Crypt\RSA\_raw_encrypt(), phpseclib\Crypt\RSA\_rsaes_oaep_decrypt(), phpseclib\Crypt\RSA\_rsaes_oaep_encrypt(), phpseclib\Crypt\RSA\_rsaes_pkcs1_v1_5_decrypt(), phpseclib\Crypt\RSA\_rsaes_pkcs1_v1_5_encrypt(), phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_sign(), phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_verify(), phpseclib\Crypt\RSA\_rsassa_pss_sign(), and phpseclib\Crypt\RSA\_rsassa_pss_verify().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _parseKey()
| phpseclib\Crypt\RSA::_parseKey | ( | $key, | |
| $type | |||
| ) |
Break a public or private key down into its constituant components.
@access private
- See also
- self::_convertPublicKey()
- self::_convertPrivateKey()
- Parameters
-
string $key int $type
- Returns
- array
Definition at line 1029 of file RSA.php.
References phpseclib\Crypt\RSA\$comment, phpseclib\Crypt\RSA\$components, $key, phpseclib\Crypt\RSA\$modulus, phpseclib\Crypt\RSA\$publicExponent, $tag, $type, $xml, phpseclib\Crypt\RSA\_decodeLength(), phpseclib\Crypt\RSA\_extractBER(), phpseclib\Crypt\RSA\_parseKey(), phpseclib\Crypt\RSA\_string_shift(), phpseclib\Crypt\RSA\ASN1_SEQUENCE, phpseclib\Crypt\Base\MODE_CFB, phpseclib\Crypt\RSA\PRIVATE_FORMAT_PKCS1, phpseclib\Crypt\RSA\PRIVATE_FORMAT_PKCS8, phpseclib\Crypt\RSA\PRIVATE_FORMAT_PUTTY, phpseclib\Crypt\RSA\PRIVATE_FORMAT_XML, phpseclib\Crypt\RSA\PUBLIC_FORMAT_OPENSSH, phpseclib\Crypt\RSA\PUBLIC_FORMAT_PKCS1, phpseclib\Crypt\RSA\PUBLIC_FORMAT_RAW, and phpseclib\Crypt\RSA\PUBLIC_FORMAT_XML.
Referenced by phpseclib\Crypt\RSA\_parseKey(), phpseclib\Crypt\RSA\createKey(), phpseclib\Crypt\RSA\loadKey(), and phpseclib\Crypt\RSA\setPublicKey().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _raw_encrypt()
| phpseclib\Crypt\RSA::_raw_encrypt | ( | $m | ) |
Raw Encryption / Decryption.
Doesn't use padding and is not recommended.
@access private
- Parameters
-
string $m
- Returns
- string
Definition at line 2441 of file RSA.php.
References $m, phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_os2ip(), and phpseclib\Crypt\RSA\_rsaep().
Referenced by phpseclib\Crypt\RSA\encrypt().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsadp()
| phpseclib\Crypt\RSA::_rsadp | ( | $c | ) |
RSADP.
@access private
- Parameters
-
\phpseclib\Math\BigInteger $c
- Returns
- \phpseclib\Math\BigInteger
Definition at line 2240 of file RSA.php.
References $c, and phpseclib\Crypt\RSA\_exponentiate().
Referenced by phpseclib\Crypt\RSA\_rsaes_oaep_decrypt(), and phpseclib\Crypt\RSA\_rsaes_pkcs1_v1_5_decrypt().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsaep()
| phpseclib\Crypt\RSA::_rsaep | ( | $m | ) |
RSAEP.
@access private
- Parameters
-
\phpseclib\Math\BigInteger $m
- Returns
- \phpseclib\Math\BigInteger
Definition at line 2222 of file RSA.php.
References $m, and phpseclib\Crypt\RSA\_exponentiate().
Referenced by phpseclib\Crypt\RSA\_raw_encrypt(), phpseclib\Crypt\RSA\_rsaes_oaep_encrypt(), and phpseclib\Crypt\RSA\_rsaes_pkcs1_v1_5_encrypt().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsaes_oaep_decrypt()
| phpseclib\Crypt\RSA::_rsaes_oaep_decrypt | ( | $c, | |
$l = '' |
|||
| ) |
RSAES-OAEP-DECRYPT.
See RFC3447#section-7.1.2. The fact that the error messages aren't distinguishable from one another hinders debugging, but, to quote from RFC3447::section-7.1.2:
Note. Care must be taken to ensure that an opponent cannot distinguish the different error conditions in Step 3.g, whether by error message or timing, or, more generally, learn partial information about the encoded message EM. Otherwise an opponent may be able to obtain useful information about the decryption of the ciphertext C, leading to a chosen-ciphertext attack such as the one observed by Manger [36].
As for $l... to quote from RFC3447#page-17:
Both the encryption and the decryption operations of RSAES-OAEP take the value of a label L as input. In this version of PKCS #1, L is the empty string; other uses of the label are outside the scope of this document.
@access private
- Parameters
-
string $c string $l
- Returns
- string
Definition at line 2383 of file RSA.php.
References $c, $l, $m, $y, phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_mgf1(), phpseclib\Crypt\RSA\_os2ip(), phpseclib\Crypt\RSA\_rsadp(), and GuzzleHttp\Psr7\hash().
 Here is the call graph for this function:
Here is the call graph for this function:◆ _rsaes_oaep_encrypt()
| phpseclib\Crypt\RSA::_rsaes_oaep_encrypt | ( | $m, | |
$l = '' |
|||
| ) |
RSAES-OAEP-ENCRYPT.
See RFC3447#section-7.1.1 and {http://en.wikipedia.org/wiki/Optimal_Asymmetric_Encryption_Padding OAES}.
@access private
- Parameters
-
string $m string $l
- Returns
- string
Definition at line 2320 of file RSA.php.
References $c, $l, $m, phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_mgf1(), phpseclib\Crypt\RSA\_os2ip(), phpseclib\Crypt\RSA\_rsaep(), GuzzleHttp\Psr7\hash(), and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Crypt\RSA\encrypt().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsaes_pkcs1_v1_5_decrypt()
| phpseclib\Crypt\RSA::_rsaes_pkcs1_v1_5_decrypt | ( | $c | ) |
RSAES-PKCS1-V1_5-DECRYPT.
For compatibility purposes, this function departs slightly from the description given in RFC3447. The reason being that RFC2313::section-8.1 (PKCS#1 v1.5) states that ciphertext's encrypted by the private key should have the second byte set to either 0 or 1 and that ciphertext's encrypted by the public key should have the second byte set to 2. In RFC3447 (PKCS#1 v2.1), the second byte is supposed to be 2 regardless of which key is used. For compatibility purposes, we'll just check to make sure the second byte is 2 or less. If it is, we'll accept the decrypted string as valid.
As a consequence of this, a private key encrypted ciphertext produced with \phpseclib\Crypt\RSA may not decrypt with a strictly PKCS#1 v1.5 compliant RSA implementation. Public key encrypted ciphertext's should but not private key encrypted ciphertext's.
@access private
- Parameters
-
string $c
- Returns
- string
Definition at line 2516 of file RSA.php.
References $c, $m, phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_os2ip(), and phpseclib\Crypt\RSA\_rsadp().
 Here is the call graph for this function:
Here is the call graph for this function:◆ _rsaes_pkcs1_v1_5_encrypt()
| phpseclib\Crypt\RSA::_rsaes_pkcs1_v1_5_encrypt | ( | $m | ) |
RSAES-PKCS1-V1_5-ENCRYPT.
@access private
- Parameters
-
string $m
- Returns
- string
Definition at line 2457 of file RSA.php.
References $c, $m, $type, phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_os2ip(), phpseclib\Crypt\RSA\_rsaep(), and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Crypt\RSA\encrypt().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsasp1()
| phpseclib\Crypt\RSA::_rsasp1 | ( | $m | ) |
RSASP1.
@access private
- Parameters
-
\phpseclib\Math\BigInteger $m
- Returns
- \phpseclib\Math\BigInteger
Definition at line 2258 of file RSA.php.
References $m, and phpseclib\Crypt\RSA\_exponentiate().
Referenced by phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_sign(), and phpseclib\Crypt\RSA\_rsassa_pss_sign().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsassa_pkcs1_v1_5_sign()
| phpseclib\Crypt\RSA::_rsassa_pkcs1_v1_5_sign | ( | $m | ) |
RSASSA-PKCS1-V1_5-SIGN.
@access private
- Parameters
-
string $m
- Returns
- string
Definition at line 2766 of file RSA.php.
References $m, $s, phpseclib\Crypt\RSA\_emsa_pkcs1_v1_5_encode(), phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_os2ip(), and phpseclib\Crypt\RSA\_rsasp1().
Referenced by phpseclib\Crypt\RSA\sign().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsassa_pkcs1_v1_5_verify()
| phpseclib\Crypt\RSA::_rsassa_pkcs1_v1_5_verify | ( | $m, | |
| $s | |||
| ) |
RSASSA-PKCS1-V1_5-VERIFY.
@access private
- Parameters
-
string $m
- Returns
- string
Definition at line 2796 of file RSA.php.
References $m, $s, phpseclib\Crypt\RSA\_emsa_pkcs1_v1_5_encode(), phpseclib\Crypt\RSA\_equals(), phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_os2ip(), and phpseclib\Crypt\RSA\_rsavp1().
Referenced by phpseclib\Crypt\RSA\verify().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsassa_pss_sign()
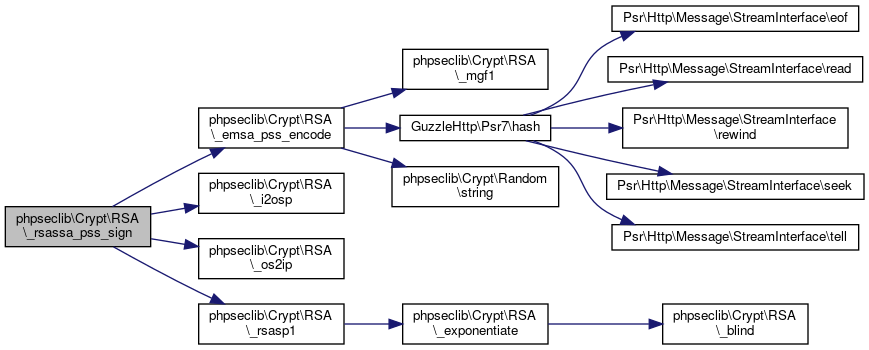
| phpseclib\Crypt\RSA::_rsassa_pss_sign | ( | $m | ) |
RSASSA-PSS-SIGN.
@access private
- Parameters
-
string $m
- Returns
- string
Definition at line 2648 of file RSA.php.
References $m, $s, phpseclib\Crypt\RSA\_emsa_pss_encode(), phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_os2ip(), and phpseclib\Crypt\RSA\_rsasp1().
Referenced by phpseclib\Crypt\RSA\sign().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsassa_pss_verify()
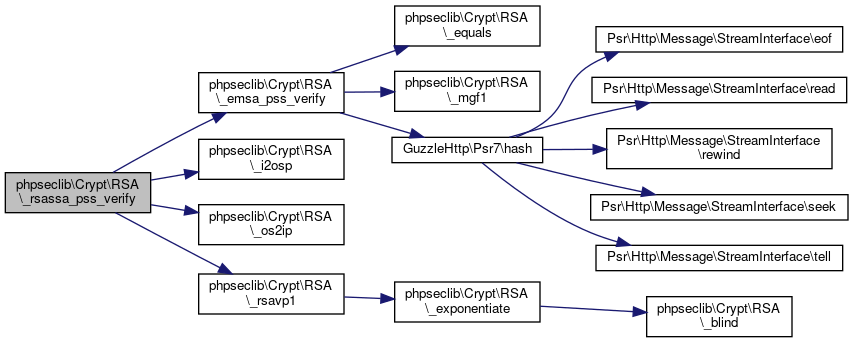
| phpseclib\Crypt\RSA::_rsassa_pss_verify | ( | $m, | |
| $s | |||
| ) |
RSASSA-PSS-VERIFY.
@access private
- Parameters
-
string $m string $s
- Returns
- string
Definition at line 2675 of file RSA.php.
References phpseclib\Crypt\RSA\$k, $m, $s, phpseclib\Crypt\RSA\_emsa_pss_verify(), phpseclib\Crypt\RSA\_i2osp(), phpseclib\Crypt\RSA\_os2ip(), and phpseclib\Crypt\RSA\_rsavp1().
Referenced by phpseclib\Crypt\RSA\verify().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _rsavp1()
| phpseclib\Crypt\RSA::_rsavp1 | ( | $s | ) |
RSAVP1.
@access private
- Parameters
-
\phpseclib\Math\BigInteger $s
- Returns
- \phpseclib\Math\BigInteger
Definition at line 2276 of file RSA.php.
References $s, and phpseclib\Crypt\RSA\_exponentiate().
Referenced by phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_verify(), and phpseclib\Crypt\RSA\_rsassa_pss_verify().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _start_element_handler()
| phpseclib\Crypt\RSA::_start_element_handler | ( | $parser, | |
| $name, | |||
| $attribs | |||
| ) |
Start Element Handler.
Called by xml_set_element_handler()
@access private
- Parameters
-
resource $parser string $name array $attribs
Definition at line 1439 of file RSA.php.
References $name.
◆ _stop_element_handler()
| phpseclib\Crypt\RSA::_stop_element_handler | ( | $parser, | |
| $name | |||
| ) |
◆ _string_shift()
| phpseclib\Crypt\RSA::_string_shift | ( | & | $string, |
$index = 1 |
|||
| ) |
String Shift.
Inspired by array_shift
- Parameters
-
string $string int $index
- Returns
- string @access private
Definition at line 1947 of file RSA.php.
References $index.
Referenced by phpseclib\Crypt\RSA\_decodeLength(), and phpseclib\Crypt\RSA\_parseKey().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ createKey()
| phpseclib\Crypt\RSA::createKey | ( | $bits = 1024, |
|
$timeout = false, |
|||
$partial = array() |
|||
| ) |
Create public / private key pair.
Returns an array with the following three elements:
- 'privatekey': The private key.
- 'publickey': The public key.
- 'partialkey': A partially computed key (if the execution time exceeded $timeout). Will need to be passed back to \phpseclib\Crypt\RSA::createKey() as the third parameter for further processing.
@access public
- Parameters
-
int $bits int $timeout array $p
Definition at line 540 of file RSA.php.
References phpseclib\Crypt\RSA\$coefficients, $config, phpseclib\Crypt\RSA\$configFile, $d, phpseclib\Crypt\RSA\$exponents, $i, $n, phpseclib\Crypt\RSA\$primes, $start, phpseclib\Crypt\RSA\_convertPrivateKey(), phpseclib\Crypt\RSA\_convertPublicKey(), phpseclib\Crypt\RSA\_generateMinMax(), and phpseclib\Crypt\RSA\_parseKey().
 Here is the call graph for this function:
Here is the call graph for this function:◆ decrypt()
| phpseclib\Crypt\RSA::decrypt | ( | $ciphertext | ) |
Decryption.
- See also
- self::encrypt() @access User interface
- Parameters
-
string $plaintext
- Returns
- string
Definition at line 2937 of file RSA.php.
References $c, phpseclib\Crypt\RSA\ENCRYPTION_NONE, and phpseclib\Crypt\RSA\ENCRYPTION_PKCS1.
◆ encrypt()
| phpseclib\Crypt\RSA::encrypt | ( | $plaintext | ) |
Encryption.
Both self::ENCRYPTION_OAEP and self::ENCRYPTION_PKCS1 both place limits on how long $plaintext can be. If $plaintext exceeds those limits it will be broken up so that it does and the resultant ciphertext's will be concatenated together.
- See also
- self::decrypt() @access User interface
- Parameters
-
string $plaintext
- Returns
- string
Definition at line 2891 of file RSA.php.
References $m, phpseclib\Crypt\RSA\_raw_encrypt(), phpseclib\Crypt\RSA\_rsaes_oaep_encrypt(), phpseclib\Crypt\RSA\_rsaes_pkcs1_v1_5_encrypt(), phpseclib\Crypt\RSA\ENCRYPTION_NONE, and phpseclib\Crypt\RSA\ENCRYPTION_PKCS1.
 Here is the call graph for this function:
Here is the call graph for this function:◆ getComment()
| phpseclib\Crypt\RSA::getComment | ( | ) |
Get public key comment.
@access public
- Returns
- string
Definition at line 2874 of file RSA.php.
References phpseclib\Crypt\RSA\$comment.
◆ getPrivateKey()
| phpseclib\Crypt\RSA::getPrivateKey | ( | $type = self::PUBLIC_FORMAT_PKCS1 | ) |
Returns the private key.
The private key is only returned if the currently loaded key contains the constituent prime numbers.
- See also
- self::getPublicKey() @access User interface
- Parameters
-
string $key int $type optional
- Returns
- mixed
Definition at line 1804 of file RSA.php.
References phpseclib\Crypt\RSA\$privateKeyFormat, $type, and phpseclib\Crypt\RSA\_convertPrivateKey().
Referenced by phpseclib\Crypt\RSA\__toString().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getPublicKey()
| phpseclib\Crypt\RSA::getPublicKey | ( | $type = self::PUBLIC_FORMAT_PKCS8 | ) |
Returns the public key.
The public key is only returned under two circumstances - if the private key had the public key embedded within it or if the public key was set via setPublicKey(). If the currently loaded key is supposed to be the public key this function won't return it since this library, for the most part, doesn't distinguish between public and private keys.
- See also
- self::getPublicKey() @access User interface
- Parameters
-
string $key int $type optional
Definition at line 1745 of file RSA.php.
References phpseclib\Crypt\RSA\$publicKeyFormat, $type, and phpseclib\Crypt\RSA\_convertPublicKey().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getPublicKeyFingerprint()
| phpseclib\Crypt\RSA::getPublicKeyFingerprint | ( | $algorithm = 'md5' | ) |
Returns the public key's fingerprint.
The public key's fingerprint is returned, which is equivalent to running ssh-keygen -lf rsa.pub. If there is no public key currently loaded, false is returned. Example output (md5): "c1:b1:30:29:d7:b8:de:6c:97:77:10:d7:46:41:63:87" (as specified by RFC 4716)
@access public
- Parameters
-
string $algorithm The hashing algorithm to be used. Valid options are 'md5' and 'sha256'. False is returned for invalid values.
- Returns
- mixed
Definition at line 1770 of file RSA.php.
References $base, phpseclib\Crypt\RSA\$hash, phpseclib\Crypt\RSA\$modulus, and phpseclib\Crypt\RSA\$publicExponent.
◆ getSize()
| phpseclib\Crypt\RSA::getSize | ( | ) |
◆ loadKey()
| phpseclib\Crypt\RSA::loadKey | ( | $key, | |
$type = false |
|||
| ) |
Loads a public or private key.
Returns true on success and false on failure (ie. an incorrect password was provided or the key was malformed)
@access public
- Parameters
-
string $key int $type optional
Definition at line 1513 of file RSA.php.
References phpseclib\Crypt\RSA\$components, phpseclib\Crypt\RSA\$exponent, $key, $type, phpseclib\Crypt\RSA\_parseKey(), comment(), GuzzleHttp\Psr7\hash(), phpseclib\Crypt\RSA\PRIVATE_FORMAT_PKCS1, phpseclib\Crypt\RSA\PUBLIC_FORMAT_OPENSSH, phpseclib\Crypt\RSA\PUBLIC_FORMAT_RAW, and phpseclib\Crypt\RSA\setPublicKey().
Referenced by phpseclib\Crypt\RSA\setPrivateKey().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ setComment()
| phpseclib\Crypt\RSA::setComment | ( | $comment | ) |
◆ setEncryptionMode()
| phpseclib\Crypt\RSA::setEncryptionMode | ( | $mode | ) |
◆ setHash()
| phpseclib\Crypt\RSA::setHash | ( | $hash | ) |
Determines which hashing function should be used.
Used with signature production / verification and (if the encryption mode is self::ENCRYPTION_OAEP) encryption and decryption. If $hash isn't supported, sha1 is used.
@access public
- Parameters
-
string $hash
Definition at line 1987 of file RSA.php.
References phpseclib\Crypt\RSA\$hash, and GuzzleHttp\Psr7\hash().
 Here is the call graph for this function:
Here is the call graph for this function:◆ setMGFHash()
| phpseclib\Crypt\RSA::setMGFHash | ( | $hash | ) |
Determines which hashing function should be used for the mask generation function.
The mask generation function is used by self::ENCRYPTION_OAEP and self::SIGNATURE_PSS and although it's best if Hash and MGFHash are set to the same thing this is not a requirement.
@access public
- Parameters
-
string $hash
Definition at line 2016 of file RSA.php.
References phpseclib\Crypt\RSA\$hash.
◆ setPassword()
| phpseclib\Crypt\RSA::setPassword | ( | $password = false | ) |
Sets the password.
Private keys can be encrypted with a password. To unset the password, pass in the empty string or false. Or rather, pass in $password such that empty($password) && !is_string($password) is true.
- See also
- self::createKey()
- self::loadKey() @access User interface
- Parameters
-
string $password
Definition at line 1629 of file RSA.php.
References phpseclib\Crypt\RSA\$password.
◆ setPrivateKey()
| phpseclib\Crypt\RSA::setPrivateKey | ( | $key = false, |
|
$type = false |
|||
| ) |
Defines the private key.
If phpseclib guessed a private key was a public key and loaded it as such it might be desirable to force phpseclib to treat the key as a private key. This function will do that.
Do note that when a new key is loaded the index will be cleared.
Returns true on success, false on failure
- See also
- self::getPublicKey() @access User interface
- Parameters
-
string $key optional int $type optional
- Returns
- bool
Definition at line 1715 of file RSA.php.
References $key, $type, and phpseclib\Crypt\RSA\loadKey().
 Here is the call graph for this function:
Here is the call graph for this function:◆ setPrivateKeyFormat()
| phpseclib\Crypt\RSA::setPrivateKeyFormat | ( | $format | ) |
Determines the private key format.
- See also
- self::createKey() @access User interface
- Parameters
-
int $format
Definition at line 1961 of file RSA.php.
References $format.
◆ setPublicKey()
| phpseclib\Crypt\RSA::setPublicKey | ( | $key = false, |
|
$type = false |
|||
| ) |
Defines the public key.
Some private key formats define the public exponent and some don't. Those that don't define it are problematic when used in certain contexts. For example, in SSH-2, RSA authentication works by sending the public key along with a message signed by the private key to the server. The SSH-2 server looks the public key up in an index of public keys and if it's present then proceeds to verify the signature. Problem is, if your private key doesn't include the public exponent this won't work unless you manually add the public exponent. phpseclib tries to guess if the key being used is the public key but in the event that it guesses incorrectly you might still want to explicitly set the key as being public.
Do note that when a new key is loaded the index will be cleared.
Returns true on success, false on failure
- See also
- self::getPublicKey() @access User interface
- Parameters
-
string $key optional int $type optional
- Returns
- bool
Definition at line 1655 of file RSA.php.
References phpseclib\Crypt\RSA\$components, phpseclib\Crypt\RSA\$exponent, $key, $type, and phpseclib\Crypt\RSA\_parseKey().
Referenced by phpseclib\Crypt\RSA\loadKey().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ setPublicKeyFormat()
| phpseclib\Crypt\RSA::setPublicKeyFormat | ( | $format | ) |
Determines the public key format.
- See also
- self::createKey() @access User interface
- Parameters
-
int $format
Definition at line 1973 of file RSA.php.
References $format.
◆ setSaltLength()
| phpseclib\Crypt\RSA::setSaltLength | ( | $sLen | ) |
Determines the salt length.
To quote from RFC3447#page-38:
Typical salt lengths in octets are hLen (the length of the output of the hash function Hash) and 0.
@access public
- Parameters
-
int $format
Definition at line 2045 of file RSA.php.
References phpseclib\Crypt\RSA\$sLen.
◆ setSignatureMode()
| phpseclib\Crypt\RSA::setSignatureMode | ( | $mode | ) |
◆ sign()
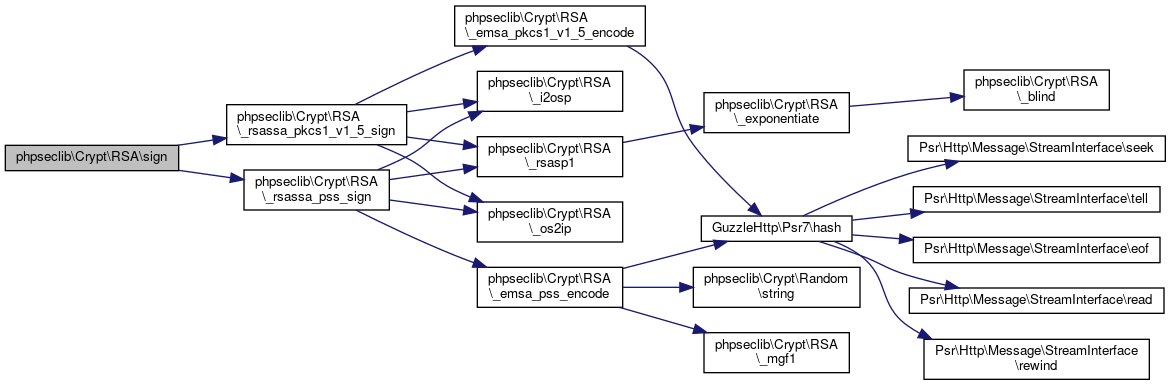
| phpseclib\Crypt\RSA::sign | ( | $message | ) |
Create a signature.
- See also
- self::verify() @access User interface
- Parameters
-
string $message
- Returns
- string
Definition at line 2979 of file RSA.php.
References $message, phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_sign(), phpseclib\Crypt\RSA\_rsassa_pss_sign(), and phpseclib\Crypt\RSA\SIGNATURE_PKCS1.
 Here is the call graph for this function:
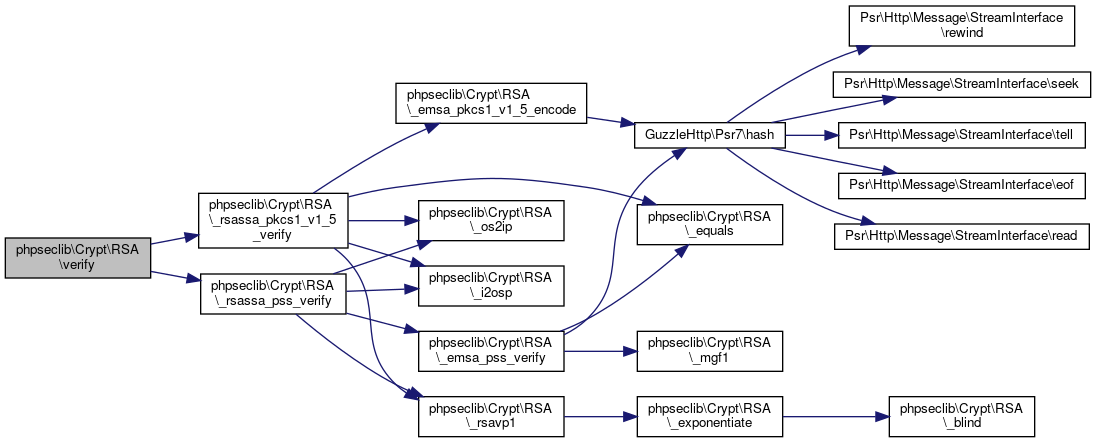
Here is the call graph for this function:◆ verify()
| phpseclib\Crypt\RSA::verify | ( | $message, | |
| $signature | |||
| ) |
Verifies a signature.
- See also
- self::sign() @access User interface
- Parameters
-
string $message string $signature
- Returns
- bool
Definition at line 3003 of file RSA.php.
References $message, phpseclib\Crypt\RSA\_rsassa_pkcs1_v1_5_verify(), phpseclib\Crypt\RSA\_rsassa_pss_verify(), and phpseclib\Crypt\RSA\SIGNATURE_PKCS1.
 Here is the call graph for this function:
Here is the call graph for this function:Field Documentation
◆ $coefficients
| phpseclib\Crypt\RSA::$coefficients |
Definition at line 330 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), and phpseclib\Crypt\RSA\createKey().
◆ $comment
| phpseclib\Crypt\RSA::$comment = 'phpseclib-generated-key' |
Definition at line 452 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPublicKey(), phpseclib\Crypt\RSA\_parseKey(), phpseclib\Crypt\RSA\getComment(), and phpseclib\Crypt\RSA\setComment().
◆ $components
| phpseclib\Crypt\RSA::$components = array() |
Definition at line 422 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), phpseclib\Crypt\RSA\_convertPublicKey(), phpseclib\Crypt\RSA\_parseKey(), phpseclib\Crypt\RSA\loadKey(), and phpseclib\Crypt\RSA\setPublicKey().
◆ $configFile
| phpseclib\Crypt\RSA::$configFile |
Definition at line 444 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\createKey().
◆ $current
◆ $encryptionMode
| phpseclib\Crypt\RSA::$encryptionMode = self::ENCRYPTION_OAEP |
◆ $exponent
| phpseclib\Crypt\RSA::$exponent |
Definition at line 306 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\loadKey(), and phpseclib\Crypt\RSA\setPublicKey().
◆ $exponents
| phpseclib\Crypt\RSA::$exponents |
Definition at line 322 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), and phpseclib\Crypt\RSA\createKey().
◆ $hash
| phpseclib\Crypt\RSA::$hash |
Definition at line 346 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), phpseclib\Crypt\RSA\getPublicKeyFingerprint(), phpseclib\Crypt\RSA\setHash(), and phpseclib\Crypt\RSA\setMGFHash().
◆ $hashName
◆ $hLen
| phpseclib\Crypt\RSA::$hLen |
Definition at line 354 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_emsa_pss_encode(), and phpseclib\Crypt\RSA\_emsa_pss_verify().
◆ $k
| phpseclib\Crypt\RSA::$k |
Definition at line 298 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_rsassa_pss_verify().
◆ $mgfHash
◆ $mgfHLen
◆ $modulus
| phpseclib\Crypt\RSA::$modulus |
Definition at line 290 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPublicKey(), phpseclib\Crypt\RSA\_parseKey(), and phpseclib\Crypt\RSA\getPublicKeyFingerprint().
◆ $one
| phpseclib\Crypt\RSA::$one |
Definition at line 266 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_exponentiate().
◆ $password
| phpseclib\Crypt\RSA::$password = false |
Definition at line 410 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), and phpseclib\Crypt\RSA\setPassword().
◆ $primes
| phpseclib\Crypt\RSA::$primes |
Definition at line 314 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), and phpseclib\Crypt\RSA\createKey().
◆ $privateKeyFormat
| phpseclib\Crypt\RSA::$privateKeyFormat = self::PRIVATE_FORMAT_PKCS1 |
Definition at line 274 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\getPrivateKey().
◆ $publicExponent
| phpseclib\Crypt\RSA::$publicExponent = false |
Definition at line 402 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPublicKey(), phpseclib\Crypt\RSA\_parseKey(), and phpseclib\Crypt\RSA\getPublicKeyFingerprint().
◆ $publicKeyFormat
| phpseclib\Crypt\RSA::$publicKeyFormat = self::PUBLIC_FORMAT_PKCS8 |
Definition at line 282 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_getPrivatePublicKey(), and phpseclib\Crypt\RSA\getPublicKey().
◆ $signatureMode
◆ $sLen
| phpseclib\Crypt\RSA::$sLen |
Definition at line 362 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_emsa_pss_encode(), phpseclib\Crypt\RSA\_emsa_pss_verify(), and phpseclib\Crypt\RSA\setSaltLength().
◆ $zero
◆ ASN1_BITSTRING
| const phpseclib\Crypt\RSA::ASN1_BITSTRING = 3 |
◆ ASN1_INTEGER
| const phpseclib\Crypt\RSA::ASN1_INTEGER = 2 |
◆ ASN1_OBJECT
| const phpseclib\Crypt\RSA::ASN1_OBJECT = 6 |
◆ ASN1_OCTETSTRING
| const phpseclib\Crypt\RSA::ASN1_OCTETSTRING = 4 |
◆ ASN1_SEQUENCE
| const phpseclib\Crypt\RSA::ASN1_SEQUENCE = 48 |
ASN1 Sequence (with the constucted bit set)
Definition at line 150 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_parseKey().
◆ ENCRYPTION_NONE
| const phpseclib\Crypt\RSA::ENCRYPTION_NONE = 3 |
Do not use any padding.
Although this method is not recommended it can none-the-less sometimes be useful if you're trying to decrypt some legacy stuff, if you're trying to diagnose why an encrypted message isn't decrypting, etc.
Definition at line 100 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\decrypt(), and phpseclib\Crypt\RSA\encrypt().
◆ ENCRYPTION_OAEP
| const phpseclib\Crypt\RSA::ENCRYPTION_OAEP = 1 |
#+ @access public
- See also
- self::encrypt()
-
self::decrypt() Use
Optimal Asymmetric Encryption Padding(OAEP) for encryption / decryption.
Uses sha1 by default.
- See also
- self::setHash()
- self::setMGFHash()
◆ ENCRYPTION_PKCS1
| const phpseclib\Crypt\RSA::ENCRYPTION_PKCS1 = 2 |
Use PKCS#1 padding.
Although self::ENCRYPTION_OAEP offers more security, including PKCS#1 padding is necessary for purposes of backwards compatibility with protocols (like SSH-1) written before OAEP's introduction.
Definition at line 93 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\decrypt(), and phpseclib\Crypt\RSA\encrypt().
◆ MODE_INTERNAL
| const phpseclib\Crypt\RSA::MODE_INTERNAL = 1 |
◆ MODE_OPENSSL
| const phpseclib\Crypt\RSA::MODE_OPENSSL = 2 |
◆ PRIVATE_FORMAT_PKCS1
| const phpseclib\Crypt\RSA::PRIVATE_FORMAT_PKCS1 = 0 |
#-
#+ @access public
- See also
- \phpseclib\Crypt\RSA::createKey()
- \phpseclib\Crypt\RSA::setPrivateKeyFormat() PKCS#1 formatted private key
Used by OpenSSH
Definition at line 179 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_parseKey(), and phpseclib\Crypt\RSA\loadKey().
◆ PRIVATE_FORMAT_PKCS8
| const phpseclib\Crypt\RSA::PRIVATE_FORMAT_PKCS8 = 8 |
PKCS#8 formatted private key.
Definition at line 191 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_parseKey().
◆ PRIVATE_FORMAT_PUTTY
| const phpseclib\Crypt\RSA::PRIVATE_FORMAT_PUTTY = 1 |
PuTTY formatted private key.
Definition at line 183 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), and phpseclib\Crypt\RSA\_parseKey().
◆ PRIVATE_FORMAT_XML
| const phpseclib\Crypt\RSA::PRIVATE_FORMAT_XML = 2 |
XML formatted private key.
Definition at line 187 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPrivateKey(), and phpseclib\Crypt\RSA\_parseKey().
◆ PUBLIC_FORMAT_OPENSSH
| const phpseclib\Crypt\RSA::PUBLIC_FORMAT_OPENSSH = 6 |
OpenSSH formatted public key.
Place in $HOME/.ssh/authorized_keys
Definition at line 235 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPublicKey(), phpseclib\Crypt\RSA\_parseKey(), and phpseclib\Crypt\RSA\loadKey().
◆ PUBLIC_FORMAT_PKCS1
| const phpseclib\Crypt\RSA::PUBLIC_FORMAT_PKCS1 = 4 |
PKCS#1 formatted public key (raw)
Used by File/X509.php
Has the following header:
--—BEGIN RSA PUBLIC KEY--—
Analogous to ssh-keygen's pem format (as specified by -m)
Definition at line 224 of file RSA.php.
Referenced by phpseclib\File\X509\_formatSubjectPublicKey(), phpseclib\Crypt\RSA\_parseKey(), and phpseclib\File\X509\computeKeyIdentifier().
◆ PUBLIC_FORMAT_PKCS1_RAW
◆ PUBLIC_FORMAT_PKCS8
| const phpseclib\Crypt\RSA::PUBLIC_FORMAT_PKCS8 = 7 |
PKCS#1 formatted public key (encapsulated)
Used by PHP's openssl_public_encrypt() and openssl's rsautl (when -pubin is set)
Has the following header:
--—BEGIN PUBLIC KEY--—
Analogous to ssh-keygen's pkcs8 format (as specified by -m). Although PKCS8 is specific to private keys it's basically creating a DER-encoded wrapper for keys. This just extends that same concept to public keys (much like ssh-keygen)
◆ PUBLIC_FORMAT_RAW
| const phpseclib\Crypt\RSA::PUBLIC_FORMAT_RAW = 3 |
#-
#+ @access public
- See also
- \phpseclib\Crypt\RSA::createKey()
- \phpseclib\Crypt\RSA::setPublicKeyFormat() Raw User interface key
An array containing two \phpseclib\Math\BigInteger objects.
The exponent can be indexed with any of the following:
0, e, exponent, publicExponent
The modulus can be indexed with any of the following:
1, n, modulo, modulus
Definition at line 212 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPublicKey(), phpseclib\Crypt\RSA\_parseKey(), phpseclib\Net\SSH2\_privatekey_login(), and phpseclib\Crypt\RSA\loadKey().
◆ PUBLIC_FORMAT_XML
| const phpseclib\Crypt\RSA::PUBLIC_FORMAT_XML = 5 |
XML formatted public key.
Definition at line 229 of file RSA.php.
Referenced by phpseclib\Crypt\RSA\_convertPublicKey(), and phpseclib\Crypt\RSA\_parseKey().
◆ SIGNATURE_PKCS1
| const phpseclib\Crypt\RSA::SIGNATURE_PKCS1 = 2 |
Use the PKCS#1 scheme by default.
Although self::SIGNATURE_PSS offers more security, including PKCS#1 signing is necessary for purposes of backwards compatibility with protocols (like SSH-2) written before PSS's introduction.
Definition at line 124 of file RSA.php.
Referenced by phpseclib\Net\SSH2\_privatekey_login(), phpseclib\File\X509\_sign(), phpseclib\File\X509\_validateSignature(), phpseclib\Crypt\RSA\sign(), phpseclib\Crypt\RSA\verify(), and Jumbojett\OpenIDConnectClient\verifyRSAJWTsignature().
◆ SIGNATURE_PSS
| const phpseclib\Crypt\RSA::SIGNATURE_PSS = 1 |
#-
#+ @access public
- See also
- self::sign()
- self::verify()
- self::setHash() Use the Probabilistic Signature Scheme for signing
Uses sha1 by default.
- See also
- self::setSaltLength()
- self::setMGFHash()
Definition at line 117 of file RSA.php.
Referenced by Jumbojett\OpenIDConnectClient\verifyRSAJWTsignature().
The documentation for this class was generated from the following file:
- libs/composer/vendor/phpseclib/phpseclib/phpseclib/Crypt/RSA.php