Collaboration diagram for phpseclib\Net\SSH1:
Collaboration diagram for phpseclib\Net\SSH1:Public Member Functions | |
| __construct ($host, $port=22, $timeout=10, $cipher=self::CIPHER_3DES) | |
| Default Constructor. More... | |
| _connect () | |
| Connect to an SSHv1 server. More... | |
| login ($username, $password='') | |
| Login. More... | |
| setTimeout ($timeout) | |
| Set Timeout. More... | |
| exec ($cmd, $block=true) | |
| Executes a command on a non-interactive shell, returns the output, and quits. More... | |
| _initShell () | |
| Creates an interactive shell. More... | |
| write ($cmd) | |
| Inputs a command into an interactive shell. More... | |
| read ($expect, $mode=self::READ__SIMPLE) | |
| Returns the output of an interactive shell when there's a match for $expect. More... | |
| interactiveWrite ($cmd) | |
| Inputs a command into an interactive shell. More... | |
| interactiveRead () | |
| Returns the output of an interactive shell when no more output is available. More... | |
| disconnect () | |
| Disconnect. More... | |
| __destruct () | |
| Destructor. More... | |
| _disconnect ($msg='Client Quit') | |
| Disconnect. More... | |
| _get_binary_packet () | |
| Gets Binary Packets. More... | |
| _send_binary_packet ($data) | |
| Sends Binary Packets. More... | |
| _crc ($data) | |
| Cyclic Redundancy Check (CRC) More... | |
| _string_shift (&$string, $index=1) | |
| String Shift. More... | |
| _rsa_crypt ($m, $key) | |
| RSA Encrypt. More... | |
| _define_array () | |
| Define Array. More... | |
| getLog () | |
| Returns a log of the packets that have been sent and received. More... | |
| _format_log ($message_log, $message_number_log) | |
| Formats a log for printing. More... | |
| _format_log_helper ($matches) | |
| Helper function for _format_log. More... | |
| getServerKeyPublicExponent ($raw_output=false) | |
| Return the server key public exponent. More... | |
| getServerKeyPublicModulus ($raw_output=false) | |
| Return the server key public modulus. More... | |
| getHostKeyPublicExponent ($raw_output=false) | |
| Return the host key public exponent. More... | |
| getHostKeyPublicModulus ($raw_output=false) | |
| Return the host key public modulus. More... | |
| getSupportedCiphers ($raw_output=false) | |
| Return a list of ciphers supported by SSH1 server. More... | |
| getSupportedAuthentications ($raw_output=false) | |
| Return a list of authentications supported by SSH1 server. More... | |
| getServerIdentification () | |
| Return the server identification. More... | |
| _append_log ($protocol_flags, $message) | |
| Logs data packets. More... | |
Data Fields | |
| const | CIPHER_NONE = 0 |
| #+ Encryption Methods More... | |
| const | CIPHER_IDEA = 1 |
| IDEA in CFB mode. More... | |
| const | CIPHER_DES = 2 |
| DES in CBC mode. More... | |
| const | CIPHER_3DES = 3 |
| Triple-DES in CBC mode. More... | |
| const | CIPHER_BROKEN_TSS = 4 |
| TRI's Simple Stream encryption CBC. More... | |
| const | CIPHER_RC4 = 5 |
| RC4. More... | |
| const | CIPHER_BLOWFISH = 6 |
| Blowfish. More... | |
| const | AUTH_RHOSTS = 1 |
| #- More... | |
| const | AUTH_RSA = 2 |
| pure RSA authentication More... | |
| const | AUTH_PASSWORD = 3 |
| password authentication More... | |
| const | AUTH_RHOSTS_RSA = 4 |
| .rhosts with RSA host authentication More... | |
| const | TTY_OP_END = 0 |
| #- More... | |
| const | RESPONSE_TYPE = 1 |
| #- More... | |
| const | RESPONSE_DATA = 2 |
| The Response Data. More... | |
| const | MASK_CONSTRUCTOR = 0x00000001 |
| #+ Execution Bitmap Masks More... | |
| const | MASK_CONNECTED = 0x00000002 |
| const | MASK_LOGIN = 0x00000004 |
| const | MASK_SHELL = 0x00000008 |
| const | LOG_SIMPLE = 1 |
| #- More... | |
| const | LOG_COMPLEX = 2 |
| Returns the message content. More... | |
| const | LOG_REALTIME = 3 |
| Outputs the content real-time. More... | |
| const | LOG_REALTIME_FILE = 4 |
| Dumps the content real-time to a file. More... | |
| const | READ_SIMPLE = 1 |
| #- More... | |
| const | READ_REGEX = 2 |
| Returns when a string matching the regular expression $expect is found. More... | |
| $identifier = 'SSH-1.5-phpseclib' | |
| $fsock | |
| $crypto = false | |
| $bitmap = 0 | |
| $server_key_public_exponent | |
| $server_key_public_modulus | |
| $host_key_public_exponent | |
| $host_key_public_modulus | |
| $supported_ciphers | |
| $supported_authentications | |
| $server_identification = '' | |
| $protocol_flags = array() | |
| $protocol_flag_log = array() | |
| $message_log = array() | |
| $realtime_log_file | |
| $realtime_log_size | |
| $realtime_log_wrap | |
| $interactiveBuffer = '' | |
| $timeout | |
| Timeout. More... | |
| $curTimeout | |
| Current Timeout. More... | |
| $log_boundary = ':' | |
| Log Boundary. More... | |
| $log_long_width = 65 | |
| Log Long Width. More... | |
| $log_short_width = 16 | |
| Log Short Width. More... | |
| $host | |
| $port | |
| $connectionTimeout | |
| $cipher | |
Detailed Description
Constructor & Destructor Documentation
◆ __construct()
| phpseclib\Net\SSH1::__construct | ( | $host, | |
$port = 22, |
|||
$timeout = 10, |
|||
$cipher = self::CIPHER_3DES |
|||
| ) |
Default Constructor.
Connects to an SSHv1 server
- Parameters
-
string $host int $port int $timeout int $cipher
- Returns
- \phpseclib\Net\SSH1 @access public
Definition at line 507 of file SSH1.php.
References phpseclib\Net\SSH1\$cipher, phpseclib\Net\SSH1\$host, phpseclib\Net\SSH1\$port, phpseclib\Net\SSH1\$timeout, and phpseclib\Net\SSH1\_define_array().
 Here is the call graph for this function:
Here is the call graph for this function:◆ __destruct()
| phpseclib\Net\SSH1::__destruct | ( | ) |
Destructor.
Will be called, automatically, if you're supporting just PHP5. If you're supporting PHP4, you'll need to call disconnect().
@access public
Definition at line 1021 of file SSH1.php.
References phpseclib\Net\SSH1\_disconnect().
 Here is the call graph for this function:
Here is the call graph for this function:Member Function Documentation
◆ _append_log()
| phpseclib\Net\SSH1::_append_log | ( | $protocol_flags, | |
| $message | |||
| ) |
Logs data packets.
Makes sure that only the last 1MB worth of packets will be logged
- Parameters
-
string $data @access private
Definition at line 1559 of file SSH1.php.
References $filename, $message, phpseclib\Net\SSH1\$protocol_flags, phpseclib\Net\SSH1\_format_log(), phpseclib\Net\SSH1\_string_shift(), phpseclib\Net\SSH1\LOG_COMPLEX, phpseclib\Net\SSH1\LOG_REALTIME, phpseclib\Net\SSH1\LOG_REALTIME_FILE, and phpseclib\Net\SSH1\LOG_SIMPLE.
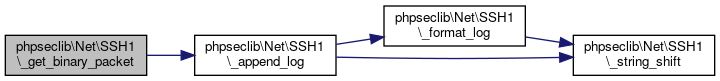
Referenced by phpseclib\Net\SSH1\_connect(), phpseclib\Net\SSH1\_get_binary_packet(), and phpseclib\Net\SSH1\_send_binary_packet().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _connect()
| phpseclib\Net\SSH1::_connect | ( | ) |
Connect to an SSHv1 server.
- Returns
- bool @access private
Definition at line 542 of file SSH1.php.
References phpseclib\Net\SSH1\$cipher, $data, phpseclib\Net\SSH1\$host_key_public_exponent, phpseclib\Net\SSH1\$host_key_public_modulus, $mask, $name, $response, phpseclib\Net\SSH1\$server_key_public_exponent, phpseclib\Net\SSH1\$server_key_public_modulus, phpseclib\Net\SSH1\_append_log(), phpseclib\Net\SSH1\_get_binary_packet(), phpseclib\Net\SSH1\_rsa_crypt(), phpseclib\Net\SSH1\_send_binary_packet(), phpseclib\Net\SSH1\_string_shift(), phpseclib\Net\SSH1\CIPHER_3DES, phpseclib\Net\SSH1\CIPHER_DES, phpseclib\Net\SSH1\MASK_CONNECTED, phpseclib\Crypt\TripleDES\MODE_3CBC, and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Net\SSH1\login().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _crc()
| phpseclib\Net\SSH1::_crc | ( | $data | ) |
Cyclic Redundancy Check (CRC)
PHP's crc32 function is implemented slightly differently than the one that SSH v1 uses, so we've reimplemented it. A more detailed discussion of the differences can be found after $crc_lookup_table's initialization.
- See also
- self::_get_binary_packet()
- self::_send_binary_packet()
- Parameters
-
string $data
- Returns
- int @access private
Definition at line 1195 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_send_binary_packet().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _define_array()
| phpseclib\Net\SSH1::_define_array | ( | ) |
Define Array.
Takes any number of arrays whose indices are integers and whose values are strings and defines a bunch of named constants from it, using the value as the name of the constant and the index as the value of the constant. If any of the constants that would be defined already exists, none of the constants will be defined.
- Parameters
-
array $array @access private
Definition at line 1360 of file SSH1.php.
References $key.
Referenced by phpseclib\Net\SSH1\__construct().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ _disconnect()
| phpseclib\Net\SSH1::_disconnect | ( | $msg = 'Client Quit' | ) |
Disconnect.
- Parameters
-
string $msg @access private
Definition at line 1032 of file SSH1.php.
References $data, and phpseclib\Net\SSH1\_send_binary_packet().
Referenced by phpseclib\Net\SSH1\__destruct(), and phpseclib\Net\SSH1\disconnect().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _format_log()
| phpseclib\Net\SSH1::_format_log | ( | $message_log, | |
| $message_number_log | |||
| ) |
Formats a log for printing.
- Parameters
-
array $message_log array $message_number_log @access private
- Returns
- string
Definition at line 1408 of file SSH1.php.
References $i, phpseclib\Net\SSH1\$message_log, Sabre\VObject\$output, and phpseclib\Net\SSH1\_string_shift().
Referenced by phpseclib\Net\SSH1\_append_log(), and phpseclib\Net\SSH1\getLog().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ _format_log_helper()
| phpseclib\Net\SSH1::_format_log_helper | ( | $matches | ) |
◆ _get_binary_packet()
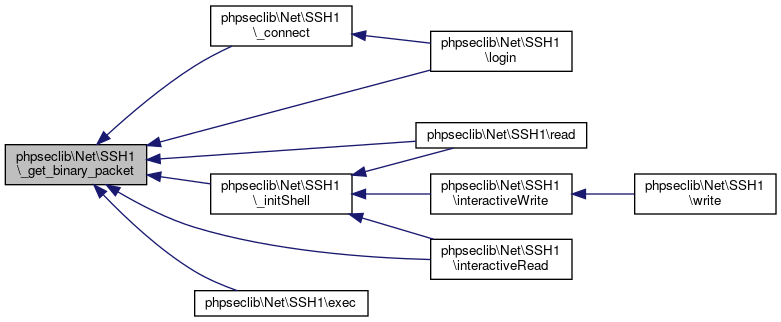
| phpseclib\Net\SSH1::_get_binary_packet | ( | ) |
Gets Binary Packets.
See 'The Binary Packet Protocol' of protocol-1.5.txt for more info.
Also, this function could be improved upon by adding detection for the following exploit: http://www.securiteam.com/securitynews/5LP042K3FY.html
- See also
- self::_send_binary_packet()
- Returns
- array @access private
Definition at line 1070 of file SSH1.php.
References $data, $start, $type, and phpseclib\Net\SSH1\_append_log().
Referenced by phpseclib\Net\SSH1\_connect(), phpseclib\Net\SSH1\_initShell(), phpseclib\Net\SSH1\exec(), phpseclib\Net\SSH1\interactiveRead(), phpseclib\Net\SSH1\login(), and phpseclib\Net\SSH1\read().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
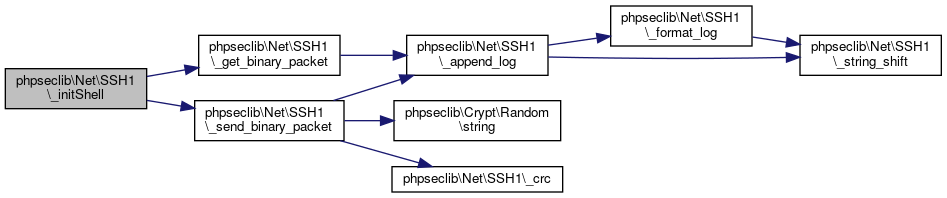
Here is the caller graph for this function:◆ _initShell()
| phpseclib\Net\SSH1::_initShell | ( | ) |
Creates an interactive shell.
- See also
- self::interactiveRead()
- self::interactiveWrite()
- Returns
- bool @access private
Definition at line 846 of file SSH1.php.
References $data, $response, phpseclib\Net\SSH1\_get_binary_packet(), phpseclib\Net\SSH1\_send_binary_packet(), and phpseclib\Net\SSH1\MASK_SHELL.
Referenced by phpseclib\Net\SSH1\interactiveRead(), phpseclib\Net\SSH1\interactiveWrite(), and phpseclib\Net\SSH1\read().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
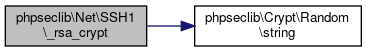
Here is the caller graph for this function:◆ _rsa_crypt()
| phpseclib\Net\SSH1::_rsa_crypt | ( | $m, | |
| $key | |||
| ) |
RSA Encrypt.
Returns mod(pow($m, $e), $n), where $n should be the product of two (large) primes $p and $q and where $e should be a number with the property that gcd($e, ($p - 1) * ($q - 1)) == 1. Could just make anything that calls this call modexp, instead, but I think this makes things clearer, maybe...
- See also
- self::__construct()
- Parameters
-
BigInteger $m array $key
- Returns
- BigInteger @access private
Definition at line 1312 of file SSH1.php.
References $key, $m, and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Net\SSH1\_connect().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
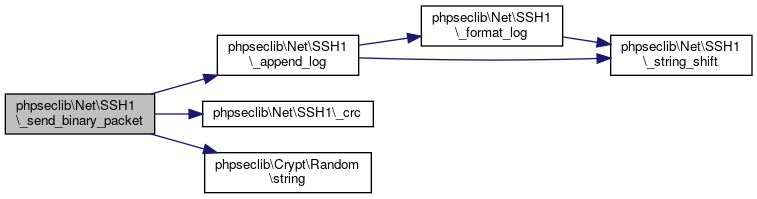
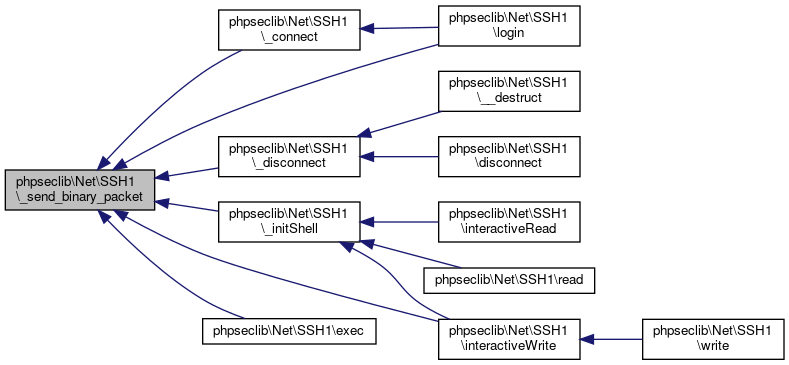
Here is the caller graph for this function:◆ _send_binary_packet()
| phpseclib\Net\SSH1::_send_binary_packet | ( | $data | ) |
Sends Binary Packets.
Returns true on success, false on failure.
- See also
- self::_get_binary_packet()
- Parameters
-
string $data
- Returns
- bool @access private
Definition at line 1147 of file SSH1.php.
References $data, $result, $start, phpseclib\Net\SSH1\_append_log(), phpseclib\Net\SSH1\_crc(), and phpseclib\Crypt\Random\string().
Referenced by phpseclib\Net\SSH1\_connect(), phpseclib\Net\SSH1\_disconnect(), phpseclib\Net\SSH1\_initShell(), phpseclib\Net\SSH1\exec(), phpseclib\Net\SSH1\interactiveWrite(), and phpseclib\Net\SSH1\login().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
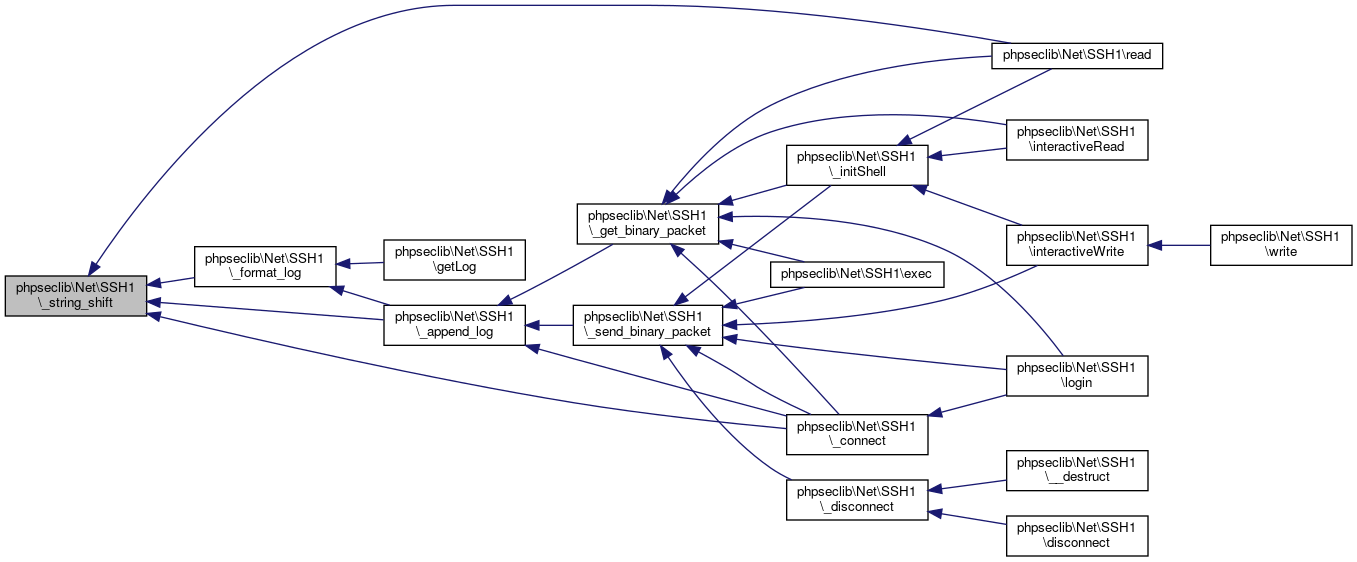
Here is the caller graph for this function:◆ _string_shift()
| phpseclib\Net\SSH1::_string_shift | ( | & | $string, |
$index = 1 |
|||
| ) |
String Shift.
Inspired by array_shift
- Parameters
-
string $string int $index
- Returns
- string @access private
Definition at line 1292 of file SSH1.php.
References $index.
Referenced by phpseclib\Net\SSH1\_append_log(), phpseclib\Net\SSH1\_connect(), phpseclib\Net\SSH1\_format_log(), and phpseclib\Net\SSH1\read().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ disconnect()
| phpseclib\Net\SSH1::disconnect | ( | ) |
Disconnect.
@access public
Definition at line 1008 of file SSH1.php.
References phpseclib\Net\SSH1\_disconnect().
 Here is the call graph for this function:
Here is the call graph for this function:◆ exec()
| phpseclib\Net\SSH1::exec | ( | $cmd, | |
$block = true |
|||
| ) |
Executes a command on a non-interactive shell, returns the output, and quits.
An SSH1 server will close the connection after a command has been executed on a non-interactive shell. SSH2 servers don't, however, this isn't an SSH2 client. The way this works, on the server, is by initiating a shell with the -s option, as discussed in the following links:
http://www.faqs.org/docs/bashman/bashref_65.html http://www.faqs.org/docs/bashman/bashref_62.html
To execute further commands, a new \phpseclib\Net\SSH1 object will need to be created.
Returns false on failure and the output, otherwise.
- See also
- self::interactiveRead()
- self::interactiveWrite()
- Parameters
-
string $cmd
- Returns
- mixed @access public
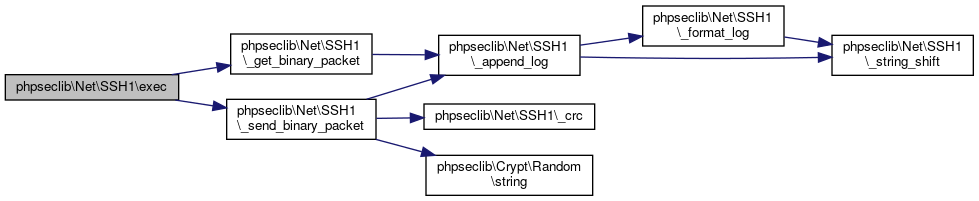
Definition at line 797 of file SSH1.php.
References $data, Sabre\VObject\$output, $response, phpseclib\Net\SSH1\_get_binary_packet(), and phpseclib\Net\SSH1\_send_binary_packet().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getHostKeyPublicExponent()
| phpseclib\Net\SSH1::getHostKeyPublicExponent | ( | $raw_output = false | ) |
Return the host key public exponent.
Returns, by default, the base-10 representation. If $raw_output is set to true, returns, instead, the raw bytes. This behavior is similar to PHP's md5() function.
- Parameters
-
bool $raw_output
- Returns
- string @access public
Definition at line 1488 of file SSH1.php.
◆ getHostKeyPublicModulus()
| phpseclib\Net\SSH1::getHostKeyPublicModulus | ( | $raw_output = false | ) |
Return the host key public modulus.
Returns, by default, the base-10 representation. If $raw_output is set to true, returns, instead, the raw bytes. This behavior is similar to PHP's md5() function.
- Parameters
-
bool $raw_output
- Returns
- string @access public
Definition at line 1503 of file SSH1.php.
◆ getLog()
| phpseclib\Net\SSH1::getLog | ( | ) |
Returns a log of the packets that have been sent and received.
Returns a string if NET_SSH1_LOGGING == self::LOG_COMPLEX, an array if NET_SSH1_LOGGING == self::LOG_SIMPLE and false if !defined('NET_SSH1_LOGGING')
@access public
- Returns
- array|false|string
Definition at line 1382 of file SSH1.php.
References phpseclib\Net\SSH1\_format_log(), phpseclib\Net\SSH1\LOG_COMPLEX, and phpseclib\Net\SSH1\LOG_SIMPLE.
 Here is the call graph for this function:
Here is the call graph for this function:◆ getServerIdentification()
| phpseclib\Net\SSH1::getServerIdentification | ( | ) |
◆ getServerKeyPublicExponent()
| phpseclib\Net\SSH1::getServerKeyPublicExponent | ( | $raw_output = false | ) |
Return the server key public exponent.
Returns, by default, the base-10 representation. If $raw_output is set to true, returns, instead, the raw bytes. This behavior is similar to PHP's md5() function.
- Parameters
-
bool $raw_output
- Returns
- string @access public
Definition at line 1458 of file SSH1.php.
◆ getServerKeyPublicModulus()
| phpseclib\Net\SSH1::getServerKeyPublicModulus | ( | $raw_output = false | ) |
Return the server key public modulus.
Returns, by default, the base-10 representation. If $raw_output is set to true, returns, instead, the raw bytes. This behavior is similar to PHP's md5() function.
- Parameters
-
bool $raw_output
- Returns
- string @access public
Definition at line 1473 of file SSH1.php.
◆ getSupportedAuthentications()
| phpseclib\Net\SSH1::getSupportedAuthentications | ( | $raw_output = false | ) |
Return a list of authentications supported by SSH1 server.
Just because a cipher is supported by an SSH1 server doesn't mean it's supported by this library. If $raw_output is set to true, returns, instead, an array of constants. ie. instead of array('password authentication'), you'll get array(self::AUTH_PASSWORD).
- Parameters
-
bool $raw_output
- Returns
- array @access public
Definition at line 1535 of file SSH1.php.
◆ getSupportedCiphers()
| phpseclib\Net\SSH1::getSupportedCiphers | ( | $raw_output = false | ) |
Return a list of ciphers supported by SSH1 server.
Just because a cipher is supported by an SSH1 server doesn't mean it's supported by this library. If $raw_output is set to true, returns, instead, an array of constants. ie. instead of array('Triple-DES in CBC mode'), you'll get array(self::CIPHER_3DES).
- Parameters
-
bool $raw_output
- Returns
- array @access public
Definition at line 1519 of file SSH1.php.
◆ interactiveRead()
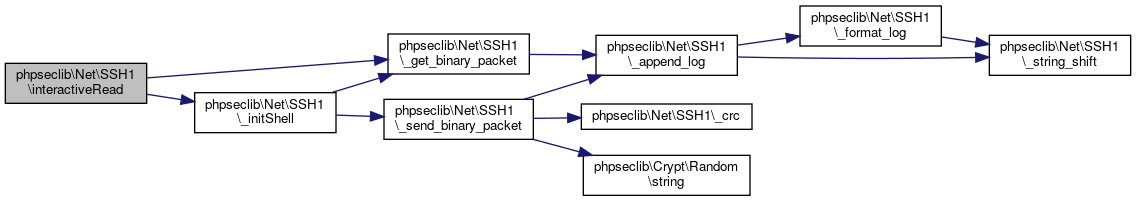
| phpseclib\Net\SSH1::interactiveRead | ( | ) |
Returns the output of an interactive shell when no more output is available.
Requires PHP 4.3.0 or later due to the use of the stream_select() function. If you see stuff like "^[[00m", you're seeing ANSI escape codes. According to How to Enable ANSI.SYS in a Command Window, "Windows NT
does not support ANSI escape sequences in Win32 Console applications", so if you're a Windows user, there's not going to be much recourse.
- See also
- self::interactiveRead()
- Returns
- string @access public
Definition at line 981 of file SSH1.php.
References $response, phpseclib\Net\SSH1\_get_binary_packet(), and phpseclib\Net\SSH1\_initShell().
 Here is the call graph for this function:
Here is the call graph for this function:◆ interactiveWrite()
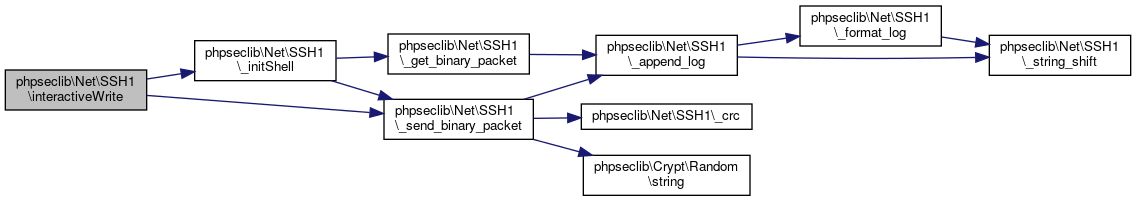
| phpseclib\Net\SSH1::interactiveWrite | ( | $cmd | ) |
Inputs a command into an interactive shell.
- See also
- self::interactiveRead()
- Parameters
-
string $cmd
- Returns
- bool @access public
Definition at line 946 of file SSH1.php.
References $data, phpseclib\Net\SSH1\_initShell(), and phpseclib\Net\SSH1\_send_binary_packet().
Referenced by phpseclib\Net\SSH1\write().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ login()
| phpseclib\Net\SSH1::login | ( | $username, | |
$password = '' |
|||
| ) |
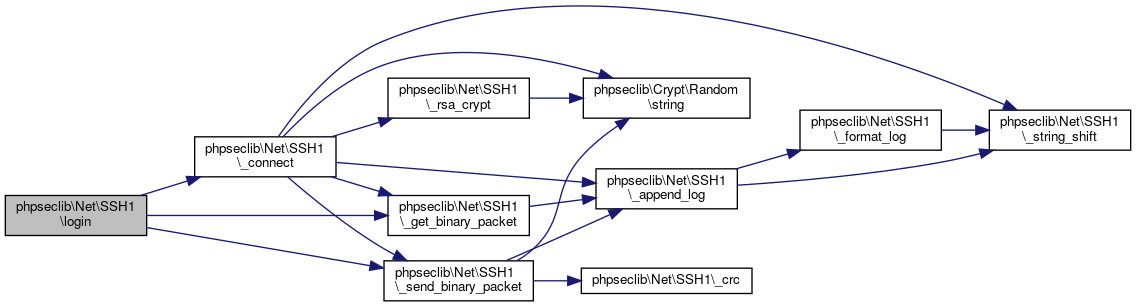
Login.
- Parameters
-
string $username string $password
- Returns
- bool @access public
Definition at line 702 of file SSH1.php.
References $data, $password, $response, phpseclib\Net\SSH1\_connect(), phpseclib\Net\SSH1\_get_binary_packet(), phpseclib\Net\SSH1\_send_binary_packet(), phpseclib\Net\SSH1\MASK_CONSTRUCTOR, and phpseclib\Net\SSH1\MASK_LOGIN.
 Here is the call graph for this function:
Here is the call graph for this function:◆ read()
| phpseclib\Net\SSH1::read | ( | $expect, | |
$mode = self::READ__SIMPLE |
|||
| ) |
Returns the output of an interactive shell when there's a match for $expect.
$expect can take the form of a string literal or, if $mode == self::READ__REGEX, a regular expression.
- See also
- self::write()
- Parameters
-
string $expect int $mode
- Returns
- bool @access public
Definition at line 907 of file SSH1.php.
References $response, phpseclib\Net\SSH1\_get_binary_packet(), phpseclib\Net\SSH1\_initShell(), and phpseclib\Net\SSH1\_string_shift().
 Here is the call graph for this function:
Here is the call graph for this function:◆ setTimeout()
| phpseclib\Net\SSH1::setTimeout | ( | $timeout | ) |
Set Timeout.
$ssh->exec('ping 127.0.0.1'); on a Linux host will never return and will run indefinitely. setTimeout() makes it so it'll timeout. Setting $timeout to false or 0 will mean there is no timeout.
- Parameters
-
mixed $timeout
Definition at line 772 of file SSH1.php.
References phpseclib\Net\SSH1\$timeout.
◆ write()
| phpseclib\Net\SSH1::write | ( | $cmd | ) |
Inputs a command into an interactive shell.
- See also
- self::interactiveWrite()
- Parameters
-
string $cmd
- Returns
- bool @access public
Definition at line 890 of file SSH1.php.
References phpseclib\Net\SSH1\interactiveWrite().
 Here is the call graph for this function:
Here is the call graph for this function:Field Documentation
◆ $bitmap
◆ $cipher
| phpseclib\Net\SSH1::$cipher |
Definition at line 493 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\__construct(), and phpseclib\Net\SSH1\_connect().
◆ $connectionTimeout
◆ $crypto
◆ $curTimeout
| phpseclib\Net\SSH1::$curTimeout |
◆ $fsock
◆ $host
| phpseclib\Net\SSH1::$host |
Definition at line 458 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\__construct().
◆ $host_key_public_exponent
| phpseclib\Net\SSH1::$host_key_public_exponent |
Definition at line 290 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_connect().
◆ $host_key_public_modulus
| phpseclib\Net\SSH1::$host_key_public_modulus |
Definition at line 301 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_connect().
◆ $identifier
◆ $interactiveBuffer
◆ $log_boundary
| phpseclib\Net\SSH1::$log_boundary = ':' |
◆ $log_long_width
| phpseclib\Net\SSH1::$log_long_width = 65 |
◆ $log_short_width
| phpseclib\Net\SSH1::$log_short_width = 16 |
◆ $message_log
| phpseclib\Net\SSH1::$message_log = array() |
Definition at line 372 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_format_log().
◆ $port
| phpseclib\Net\SSH1::$port |
Definition at line 468 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\__construct().
◆ $protocol_flag_log
◆ $protocol_flags
| phpseclib\Net\SSH1::$protocol_flags = array() |
Definition at line 354 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_append_log().
◆ $realtime_log_file
◆ $realtime_log_size
◆ $realtime_log_wrap
◆ $server_identification
◆ $server_key_public_exponent
| phpseclib\Net\SSH1::$server_key_public_exponent |
Definition at line 268 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_connect().
◆ $server_key_public_modulus
| phpseclib\Net\SSH1::$server_key_public_modulus |
Definition at line 279 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_connect().
◆ $supported_authentications
| phpseclib\Net\SSH1::$supported_authentications |
◆ $supported_ciphers
| phpseclib\Net\SSH1::$supported_ciphers |
◆ $timeout
| phpseclib\Net\SSH1::$timeout |
Timeout.
- See also
- self::setTimeout() @access private
Definition at line 416 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\__construct(), and phpseclib\Net\SSH1\setTimeout().
◆ AUTH_PASSWORD
| const phpseclib\Net\SSH1::AUTH_PASSWORD = 3 |
◆ AUTH_RHOSTS
| const phpseclib\Net\SSH1::AUTH_RHOSTS = 1 |
#-
#+ Authentication Methods
- See also
- \phpseclib\Net\SSH1::getSupportedAuthentications() @access User interface .rhosts or /etc/hosts.equiv
◆ AUTH_RHOSTS_RSA
| const phpseclib\Net\SSH1::AUTH_RHOSTS_RSA = 4 |
◆ AUTH_RSA
| const phpseclib\Net\SSH1::AUTH_RSA = 2 |
◆ CIPHER_3DES
| const phpseclib\Net\SSH1::CIPHER_3DES = 3 |
Triple-DES in CBC mode.
All implementations are required to support this
Definition at line 92 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_connect().
◆ CIPHER_BLOWFISH
| const phpseclib\Net\SSH1::CIPHER_BLOWFISH = 6 |
◆ CIPHER_BROKEN_TSS
| const phpseclib\Net\SSH1::CIPHER_BROKEN_TSS = 4 |
◆ CIPHER_DES
| const phpseclib\Net\SSH1::CIPHER_DES = 2 |
DES in CBC mode.
Definition at line 86 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_connect().
◆ CIPHER_IDEA
| const phpseclib\Net\SSH1::CIPHER_IDEA = 1 |
◆ CIPHER_NONE
| const phpseclib\Net\SSH1::CIPHER_NONE = 0 |
#+ Encryption Methods
- See also
- \phpseclib\Net\SSH1::getSupportedCiphers() @access User interface No encryption
Not supported.
◆ CIPHER_RC4
| const phpseclib\Net\SSH1::CIPHER_RC4 = 5 |
◆ LOG_COMPLEX
| const phpseclib\Net\SSH1::LOG_COMPLEX = 2 |
Returns the message content.
Definition at line 199 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_append_log(), and phpseclib\Net\SSH1\getLog().
◆ LOG_REALTIME
| const phpseclib\Net\SSH1::LOG_REALTIME = 3 |
Outputs the content real-time.
Definition at line 203 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_append_log().
◆ LOG_REALTIME_FILE
| const phpseclib\Net\SSH1::LOG_REALTIME_FILE = 4 |
Dumps the content real-time to a file.
Definition at line 207 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_append_log().
◆ LOG_SIMPLE
| const phpseclib\Net\SSH1::LOG_SIMPLE = 1 |
#-
#+ @access public
- See also
- \phpseclib\Net\SSH1::getLog() Returns the message numbers
Definition at line 195 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_append_log(), and phpseclib\Net\SSH1\getLog().
◆ MASK_CONNECTED
| const phpseclib\Net\SSH1::MASK_CONNECTED = 0x00000002 |
Definition at line 183 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_connect().
◆ MASK_CONSTRUCTOR
| const phpseclib\Net\SSH1::MASK_CONSTRUCTOR = 0x00000001 |
#+ Execution Bitmap Masks
- See also
- \phpseclib\Net\SSH1::bitmap @access private
Definition at line 182 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\login().
◆ MASK_LOGIN
| const phpseclib\Net\SSH1::MASK_LOGIN = 0x00000004 |
Definition at line 184 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\login().
◆ MASK_SHELL
| const phpseclib\Net\SSH1::MASK_SHELL = 0x00000008 |
Definition at line 185 of file SSH1.php.
Referenced by phpseclib\Net\SSH1\_initShell().
◆ READ_REGEX
| const phpseclib\Net\SSH1::READ_REGEX = 2 |
◆ READ_SIMPLE
| const phpseclib\Net\SSH1::READ_SIMPLE = 1 |
◆ RESPONSE_DATA
| const phpseclib\Net\SSH1::RESPONSE_DATA = 2 |
The Response Data.
- See also
- \phpseclib\Net\SSH1::_get_binary_packet() @access private
Definition at line 174 of file SSH1.php.
Referenced by phpseclib\Net\SCP\_receive().
◆ RESPONSE_TYPE
| const phpseclib\Net\SSH1::RESPONSE_TYPE = 1 |
#-
The Response Type
- See also
- \phpseclib\Net\SSH1::_get_binary_packet() @access private
Definition at line 166 of file SSH1.php.
Referenced by phpseclib\Net\SCP\_receive().
◆ TTY_OP_END
| const phpseclib\Net\SSH1::TTY_OP_END = 0 |
The documentation for this class was generated from the following file:
- libs/composer/vendor/phpseclib/phpseclib/phpseclib/Net/SSH1.php