Collaboration diagram for sspmod_saml_IdP_SAML2:
Collaboration diagram for sspmod_saml_IdP_SAML2:Static Public Member Functions | |
| static | sendResponse (array $state) |
| Send a response to the SP. More... | |
| static | handleAuthError (SimpleSAML_Error_Exception $exception, array $state) |
| Handle authentication error. More... | |
| static | receiveAuthnRequest (SimpleSAML_IdP $idp) |
| Receive an authentication request. More... | |
| static | processSOAPAuthnRequest (array &$state) |
| static | sendLogoutRequest (SimpleSAML_IdP $idp, array $association, $relayState) |
| Send a logout request to a given association. More... | |
| static | sendLogoutResponse (SimpleSAML_IdP $idp, array $state) |
| Send a logout response. More... | |
| static | receiveLogoutMessage (SimpleSAML_IdP $idp) |
| Receive a logout message. More... | |
| static | getLogoutURL (SimpleSAML_IdP $idp, array $association, $relayState) |
| Retrieve a logout URL for a given logout association. More... | |
| static | getAssociationConfig (SimpleSAML_IdP $idp, array $association) |
| Retrieve the metadata for the given SP association. More... | |
Static Private Member Functions | |
| static | getAssertionConsumerService (array $supportedBindings, SimpleSAML_Configuration $spMetadata, $AssertionConsumerServiceURL, $ProtocolBinding, $AssertionConsumerServiceIndex) |
| Find SP AssertionConsumerService based on parameter in AuthnRequest. More... | |
| static | generateNameIdValue (SimpleSAML_Configuration $idpMetadata, SimpleSAML_Configuration $spMetadata, array &$state) |
| Calculate the NameID value that should be used. More... | |
| static | encodeAttributes (SimpleSAML_Configuration $idpMetadata, SimpleSAML_Configuration $spMetadata, array $attributes) |
| Helper function for encoding attributes. More... | |
| static | getAttributeNameFormat (SimpleSAML_Configuration $idpMetadata, SimpleSAML_Configuration $spMetadata) |
| Determine which NameFormat we should use for attributes. More... | |
| static | buildAssertion (SimpleSAML_Configuration $idpMetadata, SimpleSAML_Configuration $spMetadata, array &$state) |
| Build an assertion based on information in the metadata. More... | |
| static | encryptAssertion (SimpleSAML_Configuration $idpMetadata, SimpleSAML_Configuration $spMetadata, \SAML2\Assertion $assertion) |
| Encrypt an assertion. More... | |
| static | buildLogoutRequest (SimpleSAML_Configuration $idpMetadata, SimpleSAML_Configuration $spMetadata, array $association, $relayState) |
| Build a logout request based on information in the metadata. More... | |
| static | buildResponse (SimpleSAML_Configuration $idpMetadata, SimpleSAML_Configuration $spMetadata, $consumerURL) |
| Build a authentication response based on information in the metadata. More... | |
Detailed Description
Member Function Documentation
◆ buildAssertion()
|
staticprivate |
Build an assertion based on information in the metadata.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. SimpleSAML_Configuration $spMetadata The metadata of the SP. array &$state The state array with information about the request.
- Returns
- \SAML2\Assertion The assertion.
- Exceptions
-
SimpleSAML_Error_Exception In case an error occurs when creating a holder-of-key assertion.
Definition at line 865 of file SAML2.php.
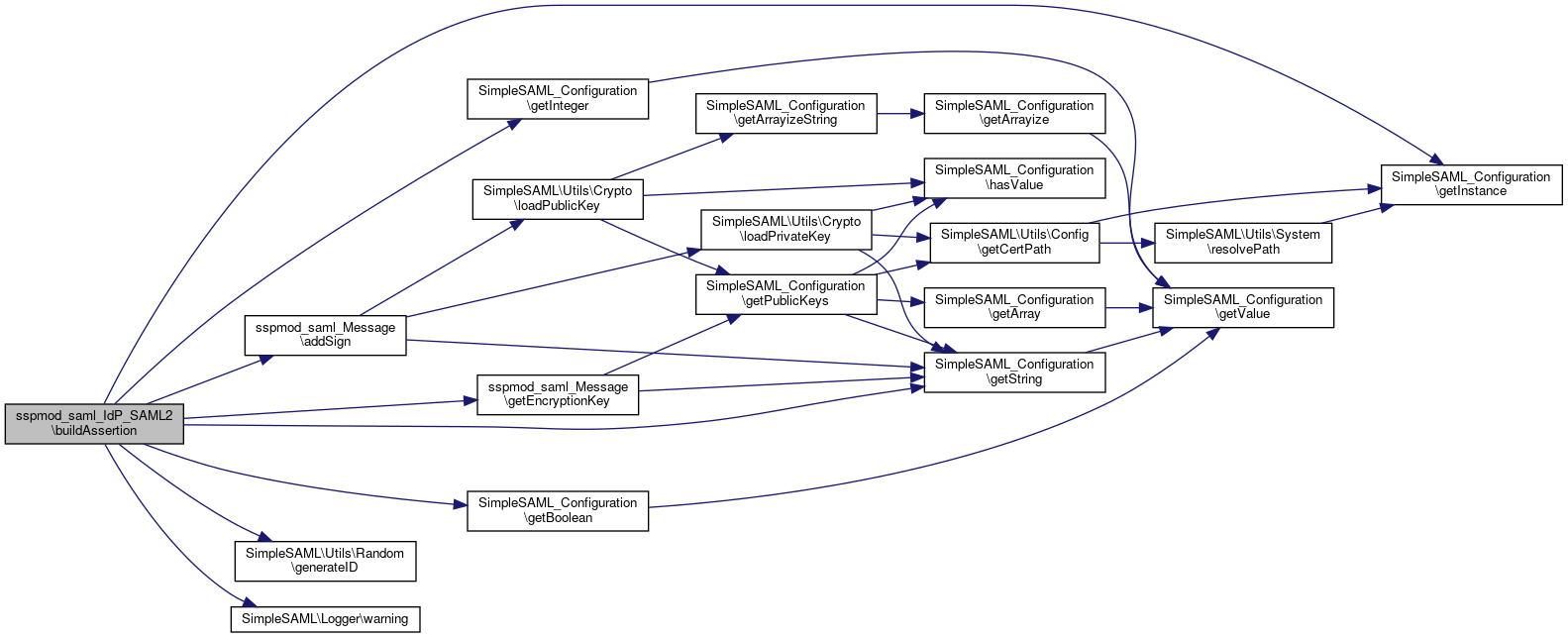
References $_SERVER, $assertionLifetime, $attributeNameFormat, $attributes, $config, $encryptNameId, $idpMetadata, $nameId, $nameIdFormat, $nameIdValue, $sc, $spMetadata, $state, sspmod_saml_Message\addSign(), SAML2\Constants\CM_BEARER, SAML2\Constants\CM_HOK, encodeAttributes(), SimpleSAML\Utils\Random\generateID(), generateNameIdValue(), getAttributeNameFormat(), sspmod_saml_Message\getEncryptionKey(), SimpleSAML_Configuration\getInstance(), SAML2\Constants\NAMEID_TRANSIENT, SubjectConfirmationData, and SimpleSAML\Logger\warning().
Referenced by sendResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ buildLogoutRequest()
|
staticprivate |
Build a logout request based on information in the metadata.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. SimpleSAML_Configuration $spMetadata The metadata of the SP. array $association The SP association. string | null $relayState An id that should be carried across the logout.
- Returns
- \SAML2\LogoutResponse The corresponding SAML2 logout response.
Definition at line 1118 of file SAML2.php.
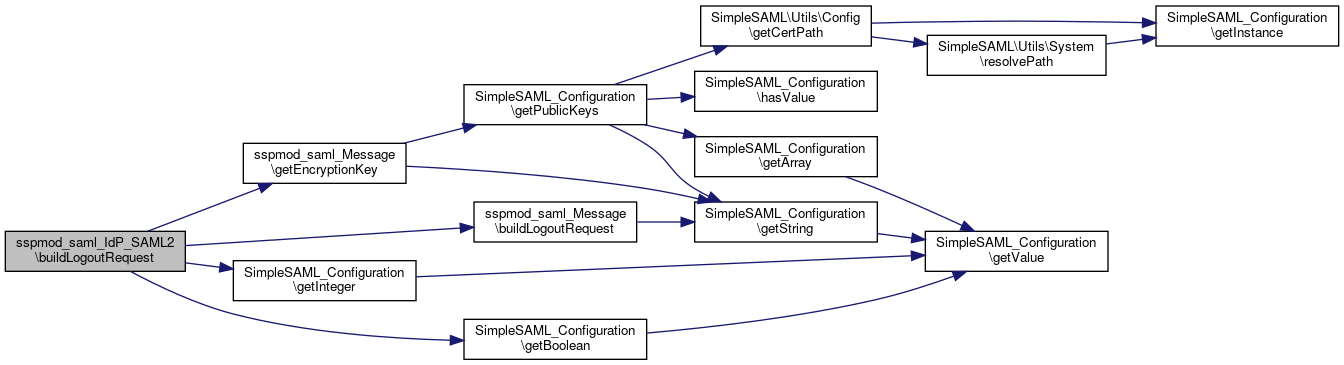
References $assertionLifetime, $association, $encryptNameId, $idpMetadata, $lr, $relayState, $spMetadata, sspmod_saml_Message\buildLogoutRequest(), and sspmod_saml_Message\getEncryptionKey().
Referenced by getLogoutURL(), and sendLogoutRequest().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ buildResponse()
|
staticprivate |
Build a authentication response based on information in the metadata.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. SimpleSAML_Configuration $spMetadata The metadata of the SP. string $consumerURL The Destination URL of the response.
- Returns
- \SAML2\Response The SAML2 response corresponding to the given data.
Definition at line 1157 of file SAML2.php.
References $idpMetadata, $r, $spMetadata, and sspmod_saml_Message\addSign().
Referenced by handleAuthError(), and sendResponse().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ encodeAttributes()
|
staticprivate |
Helper function for encoding attributes.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. SimpleSAML_Configuration $spMetadata The metadata of the SP. array $attributes The attributes of the user.
- Returns
- array The encoded attributes.
- Exceptions
-
SimpleSAML_Error_Exception In case an unsupported encoding is specified by configuration.
Definition at line 743 of file SAML2.php.
References $attributes, $idpMetadata, $name, $ret, $spMetadata, $values, and SAML2\DOMDocumentFactory\fromString().
Referenced by buildAssertion().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ encryptAssertion()
|
staticprivate |
Encrypt an assertion.
This function takes in a \SAML2\Assertion and encrypts it if encryption of assertions are enabled in the metadata.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. SimpleSAML_Configuration $spMetadata The metadata of the SP. \SAML2\Assertion $assertion The assertion we are encrypting.
- Returns
- \SAML2\Assertion|\SAML2\EncryptedAssertion The assertion.
- Exceptions
-
SimpleSAML_Error_Exception In case the encryption key type is not supported.
Definition at line 1056 of file SAML2.php.
References $idpMetadata, $key, $keys, and $spMetadata.
Referenced by sendResponse().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ generateNameIdValue()
|
staticprivate |
Calculate the NameID value that should be used.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. SimpleSAML_Configuration $spMetadata The metadata of the SP. array &$state The authentication state of the user.
- Returns
- string The NameID value.
Definition at line 691 of file SAML2.php.
References $attributes, $idpEntityId, $idpMetadata, $spEntityId, $spMetadata, $state, SimpleSAML\Logger\error(), SimpleSAML\Utils\Config\getSecretSalt(), and GuzzleHttp\Psr7\hash().
Referenced by buildAssertion().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getAssertionConsumerService()
|
staticprivate |
Find SP AssertionConsumerService based on parameter in AuthnRequest.
- Parameters
-
array $supportedBindings The bindings we allow for the response. SimpleSAML_Configuration $spMetadata The metadata for the SP. string | NULL $AssertionConsumerServiceURL AssertionConsumerServiceURL from request. string | NULL $ProtocolBinding ProtocolBinding from request. int | NULL $AssertionConsumerServiceIndex AssertionConsumerServiceIndex from request.
- Returns
- array Array with the Location and Binding we should use for the response.
Definition at line 162 of file SAML2.php.
References $spMetadata, and SimpleSAML\Logger\warning().
Referenced by receiveAuthnRequest().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
Here is the caller graph for this function:◆ getAssociationConfig()
|
static |
Retrieve the metadata for the given SP association.
- Parameters
-
SimpleSAML_IdP $idp The IdP the association belongs to. array $association The SP association.
- Returns
- SimpleSAML_Configuration Configuration object for the SP metadata.
Definition at line 671 of file SAML2.php.
References $association, $metadata, SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), and SimpleSAML_Configuration\loadFromArray().
 Here is the call graph for this function:
Here is the call graph for this function:◆ getAttributeNameFormat()
|
staticprivate |
Determine which NameFormat we should use for attributes.
- Parameters
-
SimpleSAML_Configuration $idpMetadata The metadata of the IdP. SimpleSAML_Configuration $spMetadata The metadata of the SP.
- Returns
- string The NameFormat.
Definition at line 824 of file SAML2.php.
References $attributeNameFormat, $idpMetadata, and $spMetadata.
Referenced by buildAssertion().
 Here is the caller graph for this function:
Here is the caller graph for this function:◆ getLogoutURL()
|
static |
Retrieve a logout URL for a given logout association.
- Parameters
-
SimpleSAML_IdP $idp The IdP we are sending a logout request from. array $association The association that should be terminated. string | NULL $relayState An id that should be carried across the logout.
- Returns
- string The logout URL.
Definition at line 631 of file SAML2.php.
References $association, $binding, $bindings, $dst, $idp, $idpMetadata, $lr, $metadata, PHPMailer\PHPMailer\$params, $relayState, $spMetadata, buildLogoutRequest(), SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), SimpleSAML\Module\getModuleURL(), and SimpleSAML\Logger\info().
 Here is the call graph for this function:
Here is the call graph for this function:◆ handleAuthError()
|
static |
Handle authentication error.
SimpleSAML_Error_Exception $exception The exception.
- Parameters
-
array $state The error state.
Definition at line 96 of file SAML2.php.
References $binding, $idp, $idpMetadata, $relayState, $spEntityId, $spMetadata, $state, buildResponse(), sspmod_saml_Error\fromException(), SAML2\Binding\getBinding(), SimpleSAML_IdP\getByState(), SimpleSAML_Configuration\loadFromArray(), SimpleSAML_Error_Exception\log(), SimpleSAML_Stats\log(), and SimpleSAML\Logger\warning().
 Here is the call graph for this function:
Here is the call graph for this function:◆ processSOAPAuthnRequest()
|
static |
Definition at line 443 of file SAML2.php.
References $_SERVER, $state, and SimpleSAML\Logger\error().
Referenced by receiveAuthnRequest().
 Here is the call graph for this function:
Here is the call graph for this function: Here is the caller graph for this function:
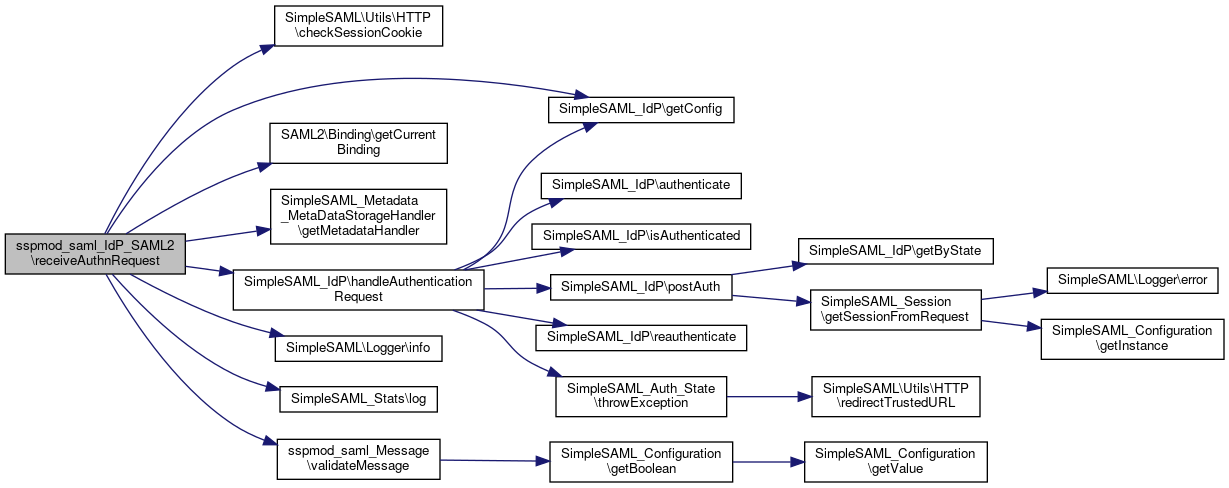
Here is the caller graph for this function:◆ receiveAuthnRequest()
|
static |
Receive an authentication request.
- Parameters
-
SimpleSAML_IdP $idp The IdP we are receiving it for.
- Exceptions
-
SimpleSAML_Error_BadRequest In case an error occurs when trying to receive the request.
Definition at line 248 of file SAML2.php.
References $binding, $idp, $idpMetadata, $metadata, $relayState, $request, $spEntityId, $spMetadata, $state, SAML2\Constants\BINDING_HOK_SSO, SAML2\Constants\BINDING_HTTP_ARTIFACT, SAML2\Constants\BINDING_PAOS, SimpleSAML\Utils\HTTP\checkSessionCookie(), SimpleSAML_Auth_State\EXCEPTION_HANDLER_FUNC, getAssertionConsumerService(), SAML2\Binding\getCurrentBinding(), SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), SimpleSAML\Logger\info(), SimpleSAML_Stats\log(), processSOAPAuthnRequest(), SimpleSAML_Auth_State\RESTART, and sspmod_saml_Message\validateMessage().
 Here is the call graph for this function:
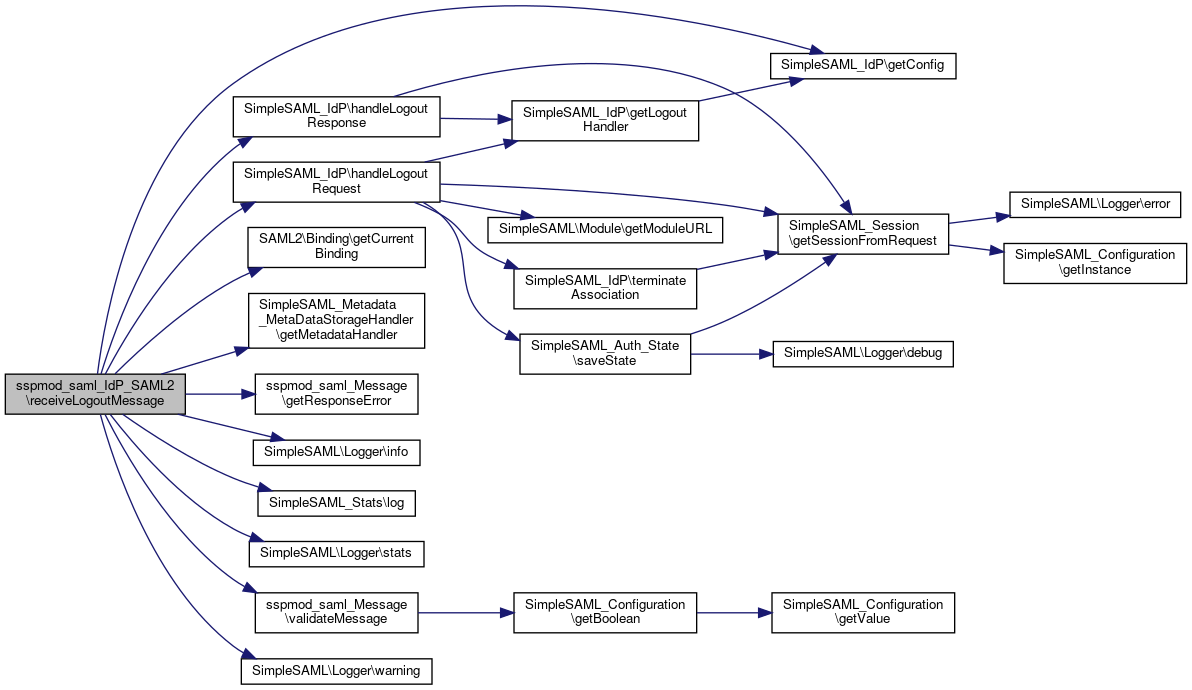
Here is the call graph for this function:◆ receiveLogoutMessage()
|
static |
Receive a logout message.
- Parameters
-
SimpleSAML_IdP $idp The IdP we are receiving it for.
- Exceptions
-
SimpleSAML_Error_BadRequest In case an error occurs while trying to receive the logout message.
Definition at line 556 of file SAML2.php.
References $assocId, $binding, $idp, $idpMetadata, $message, $metadata, $relayState, $spEntityId, $spMetadata, $state, SAML2\Binding\getCurrentBinding(), SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), sspmod_saml_Message\getResponseError(), SimpleSAML\Logger\info(), SimpleSAML_Stats\log(), SimpleSAML\Logger\stats(), sspmod_saml_Message\validateMessage(), and SimpleSAML\Logger\warning().
 Here is the call graph for this function:
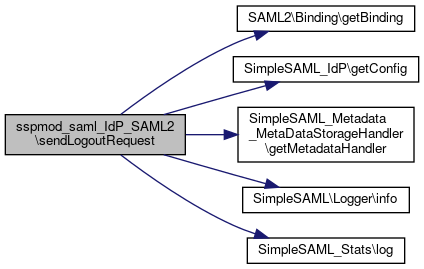
Here is the call graph for this function:◆ sendLogoutRequest()
|
static |
Send a logout request to a given association.
- Parameters
-
SimpleSAML_IdP $idp The IdP we are sending a logout request from. array $association The association that should be terminated. string | NULL $relayState An id that should be carried across the logout.
Definition at line 462 of file SAML2.php.
References $association, $binding, $dst, $idp, $idpMetadata, $lr, $metadata, $relayState, $spMetadata, buildLogoutRequest(), SAML2\Binding\getBinding(), SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), SimpleSAML\Logger\info(), and SimpleSAML_Stats\log().
 Here is the call graph for this function:
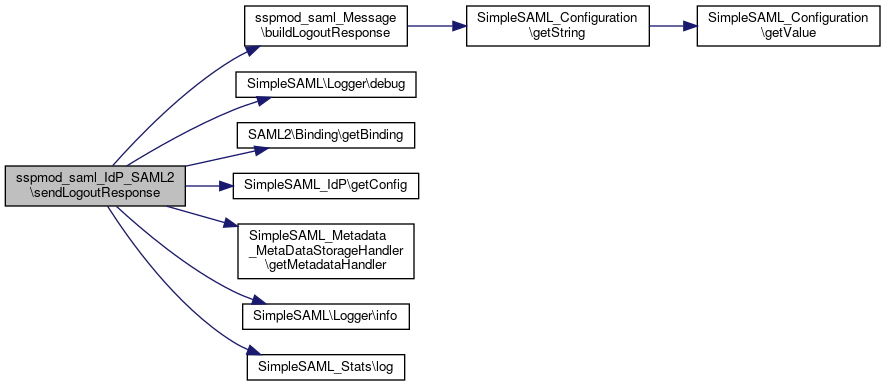
Here is the call graph for this function:◆ sendLogoutResponse()
|
static |
Send a logout response.
- Parameters
-
SimpleSAML_IdP $idp The IdP we are sending a logout request from. array &$state The logout state array.
Definition at line 498 of file SAML2.php.
References $binding, $dst, $idp, $idpMetadata, $lr, $metadata, $spEntityId, $spMetadata, $state, sspmod_saml_Message\buildLogoutResponse(), SimpleSAML\Logger\debug(), SAML2\Binding\getBinding(), SimpleSAML_Metadata_MetaDataStorageHandler\getMetadataHandler(), SimpleSAML\Logger\info(), and SimpleSAML_Stats\log().
 Here is the call graph for this function:
Here is the call graph for this function:◆ sendResponse()
|
static |
Send a response to the SP.
- Parameters
-
array $state The authentication state.
Definition at line 19 of file SAML2.php.
References $association, $binding, $idp, $idpMetadata, $relayState, $spEntityId, $spMetadata, $state, buildAssertion(), buildResponse(), encryptAssertion(), SAML2\Binding\getBinding(), SimpleSAML_IdP\getByState(), SimpleSAML\Logger\info(), SimpleSAML_Configuration\loadFromArray(), and SimpleSAML_Stats\log().
 Here is the call graph for this function:
Here is the call graph for this function:The documentation for this class was generated from the following file:
- libs/composer/vendor/simplesamlphp/simplesamlphp/modules/saml/lib/IdP/SAML2.php